Endpoint Security for Mac
What is Endpoint Security for Mac?
As more companies adopt Mac systems across their workforce, these sleek devices become a bigger target for cyberattacks. The problem? Most teams still rely on built-in tools that aren’t equipped to handle today’s sophisticated threats.
Endpoint security fills that gap.
Endpoint Security for Mac is a set of technologies—antivirus, firewalls, intrusion detection, and more—designed to protect Macs from malware, ransomware, phishing, and unauthorized access.
By investing in Mac-specific endpoint security, your organization:
Lowers the risk of data
breaches
Hardens defenses against evolving
threats
Builds a security posture that scales with your business
Why macOS Endpoint Security?
70%
of businesses using Mac devices report experiencing cyberattacks.
– market.us Scoop
15%
of malware targeting macOS users in 2023 included ransomware and Remote Access Trojans (RATs).
– Moonlock
54.7%
of cyberattacks on macOS involved trojans.
– Bitdefender Threat Landscape Report
CISOs and IT leaders need layered security purpose-built for macOS.
AI-Powered Prevention-first Approach
to Endpoint Security for Mac
Robust Data Loss Prevention
Real-Time Content Inspection
- Scans files, emails, and network traffic for sensitive data like financial records or intellectual property using AI.
USB Device Control
- Blocks unauthorized USB transfers and enforces encryption to prevent data leaks.
Behavioral Analytics
- Detects unusual activity, like USB file transfer, copy-paste to AI SaaS/ Non AI SaaS apps, and airdrop transfers.
Compliance Automation
- Enforces GDPR, HIPAA, and PCI DSS with audit trails and automated policy fixes.
Unified Compliance, Device Security & Management
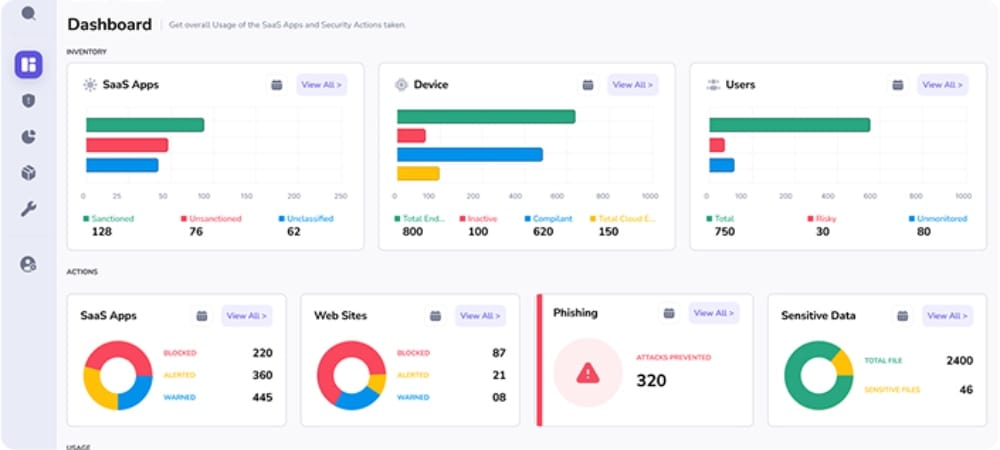
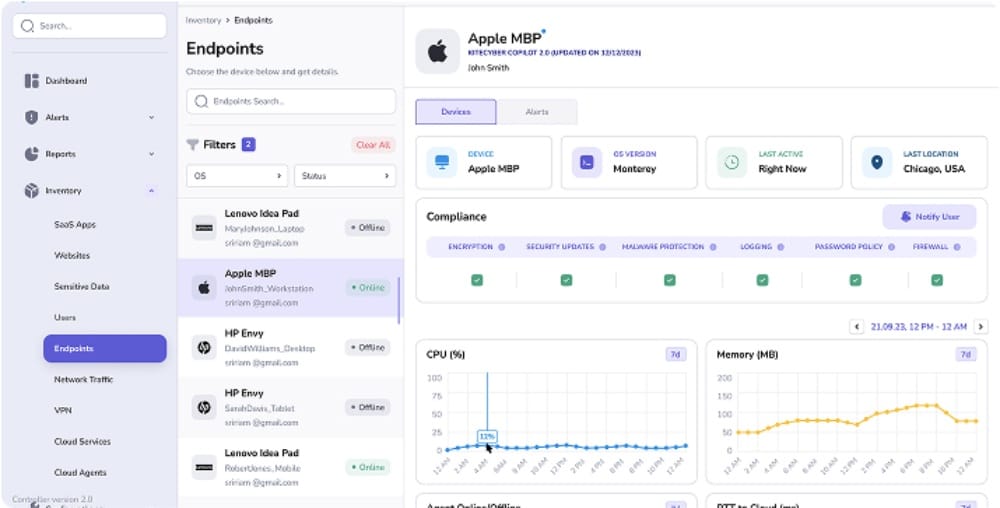
Centralized Dashboard
- Manage policies, monitor devices, and automate compliance reporting.
Remote Wipe & Lock
- Secure BYOD Mac devices, protecting data in case of a theft or breach.
Patch Management
- Patches misconfigurations and enforces least-privilege access for Mac devices.
Secure Internet & SaaS Governance
AI-Driven Web Security
- Blocks malicious domains, phishing sites, and risky AI tools in real time.
SaaS Shadow IT Discovery
- Identifies unsanctioned SaaS apps and enforces access policies within the organization.
Zero Trust Network Access (ZTNA)
Replace legacy VPNs with Kitecyber’s Infra Shield, a passwordless ZTNA solution.
| Feature | Legacy VPNs | Kitecyber ZTNA |
|---|---|---|
Credential Security | Password-dependent | Passwordless, device-trusted |
Performance | Latency from gateways | Direct, encrypted connections |
Deployment | Weeks of setup | Zero-touch in minutes |
Best Practices for macOS Endpoint Security (And How Kitecyber Automates Them)
| Best Practice | Kitecyber’s Solution |
|---|---|
Patch outdated software | Patch management software (assumed) |
Enforce least privilege | Role-based access control (RBAC) + privilege monitoring |
Monitor file integrity | Real-time File Integrity Monitoring (FIM) for critical macOS system files |
Compliance controls | Security configuration audits using certified CIS benchmarks for macOS |
Zero Trust Network Access | Passwordless VPN alternative with device and identity checks |
Mac DLP | Sensitive data classification and lineage tracking for macOS endpoints |
AI-powered Anti-Phishing | Omnichannel phishing prevention with AI for Mac users |
Device management | Seamlessly track macOS devices, whether managed or unmanaged (BYOD) |
SaaS security | Secure both sanctioned and unsanctioned SaaS apps for macOS users |
Why Choose Kitecyber for Mac Endpoint Security?
Real-time AI-powered ransomware detection
Filters malicious traffic to SaaS apps, cloud shells, and APIs
Compliance-ready security features
Designed for today’s hybrid work environments

Minimal resource usage: 1.2% CPU, 200 MB RAM—no performance drag
Confidently Secure Every Mac
How it works
Frequently asked questions
macOS includes several native security tools, such as:
- FileVault for full-disk encryption
- Gatekeeper to block unauthorized app installations
- XProtect for automatic malware detection
These features provide a strong foundation but are not sufficient on their own for enterprise-grade security.
Third-party tools significantly boost macOS security by offering capabilities native tools may lack, such as:
- Antivirus software for advanced malware detection and real-time scanning
- EDR (Endpoint Detection and Response) for behavioral analysis and threat response
- Firewalls for controlling inbound and outbound traffic
These tools help create a layered defense against evolving threats.
To maximize Mac endpoint security, businesses should:
- Apply regular software updates
- Conduct employee cybersecurity training
- Implement access controls and role-based permissions
- Perform regular security audits
- Enable two-factor authentication and strong password policies
Following these practices reduces risk and strengthens the overall cybersecurity posture.
A robust Mac endpoint protection solution should offer:
- Real-time threat detection for proactive defense
- Comprehensive malware protection using signature and behavior-based analysis
- Centralized management for simplified IT oversight
- Automated response actions like device quarantining and remote lock/wipe
These features ensure timely responses to threats and scalable protection across all Mac devices.