Kitecyber Data Shield: An Endpoint DLP Solution
Prevent insider threats, unauthorized file transfers, and AI-driven data exfiltration, directly from the endpoint. Kitecyber’s Endpoint DLP protects your business data where it matters most: on the device.

Detect & Manage Insider Theft
Deploy in minutes with zero-touch provisioning
Stop rogue uploads, Airdrop misuse, copy-paste exfiltration.
Overview
Insiders, AI Tools, and Endpoint Blind Spots Are Your Real Data Risk
Most data loss happens at the device level, before the network sees a thing. Here’s what legacy in-network DLP solution misses:
Careless actions
Copy-paste, uploads, or Airdrop misuse.
Malicious intent
Insiders stealing confidential data.

Compromised accounts
Unauthorized access leading to leaks.
Why Endpoint DLP Solution Matters
78%
organizations experienced a data breach even with DLP in place.
50%
of workers who changed jobs within the last two years admitted to taking data when they left
62%
of organizations do not have a mature data loss prevention (DLP) program in place
Product Overview
Kitecyber Data Shield: Unified Endpoint DLP Software
Kitecyber Data Shield secures sensitive data across endpoints, SaaS apps, networks, and storage devices. Monitor behavior. Block risks. Respond instantly.
Identify and protect sensitive data across all
devices
Stop data exfiltration before it
happens
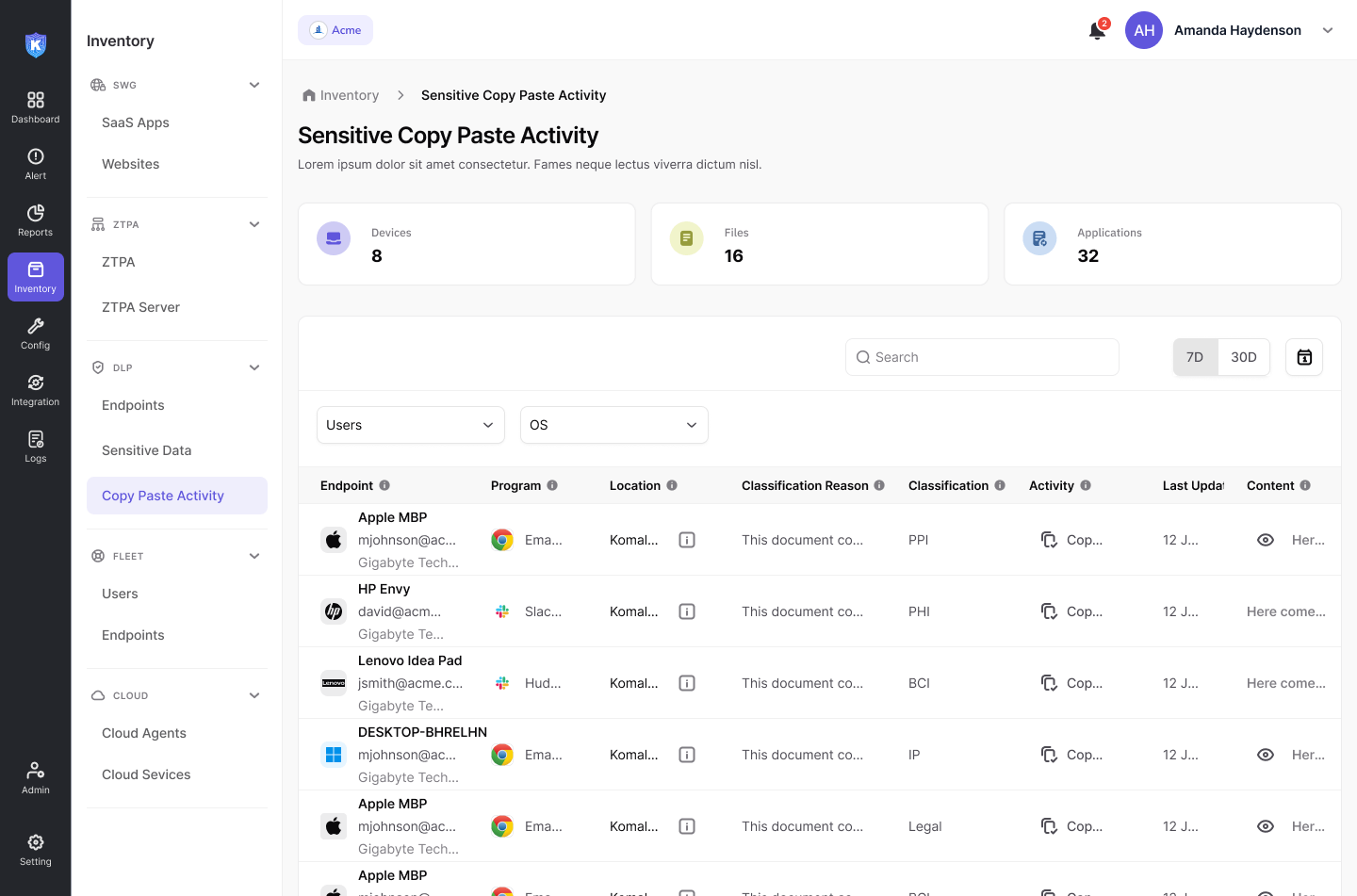
Secure sensitive information—such as PII and ePHI—by detecting and stopping copy-paste activities, email attachments, and insider threats. Stay ahead of potential breaches with proactive monitoring and automated threat mitigation.
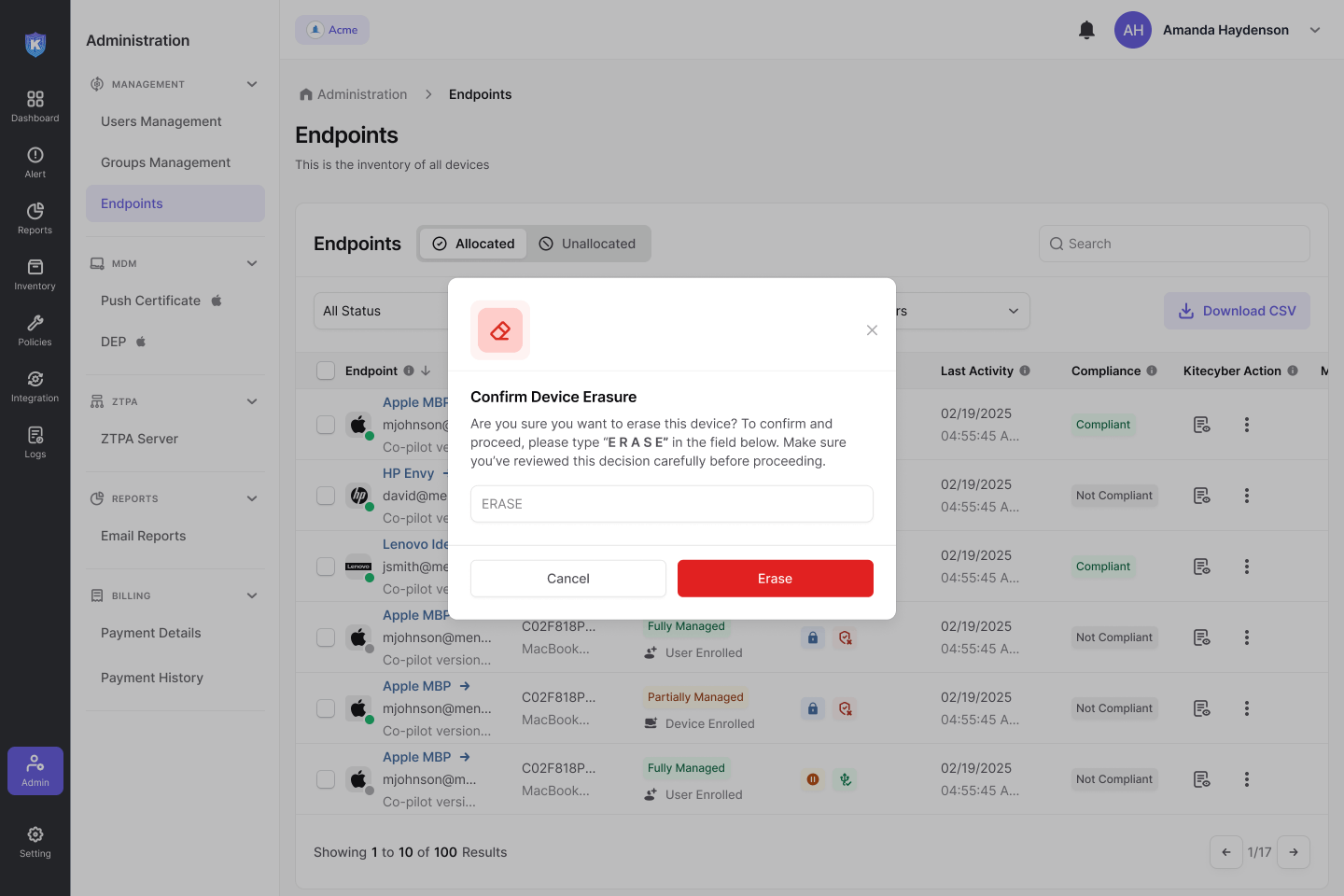
Instantly erase data to prevent unauthorized
access
Maintain full control over your business data, no matter where your devices are. Kitecyber’s Remote Wipe feature allows administrators to erase sensitive business data on devices instantly with a single command—ensuring critical data stays protected from loss, theft, or unauthorized access.
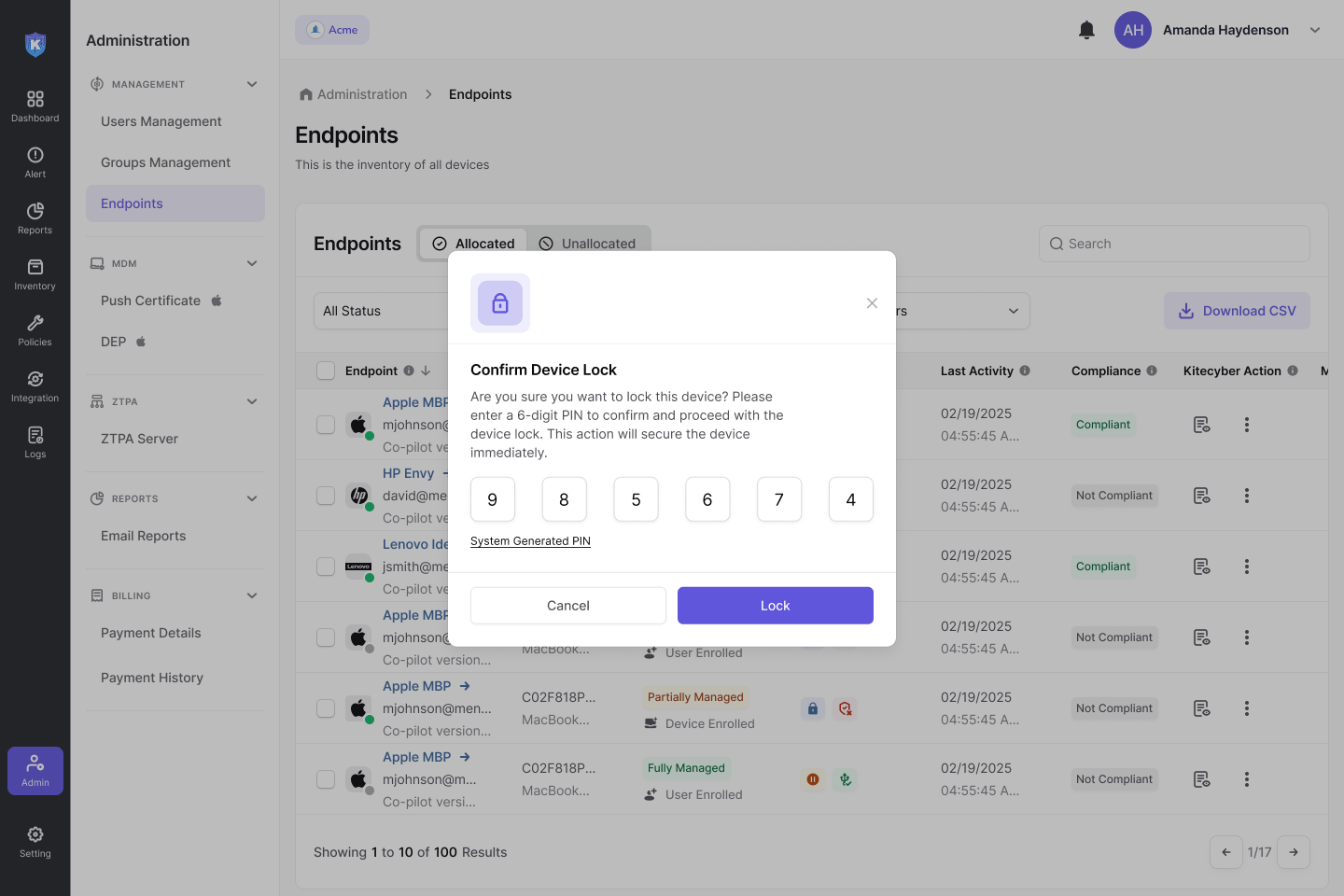
Secure lost or stolen devices with a single
action
Enforce regulatory compliance and prevent data theft
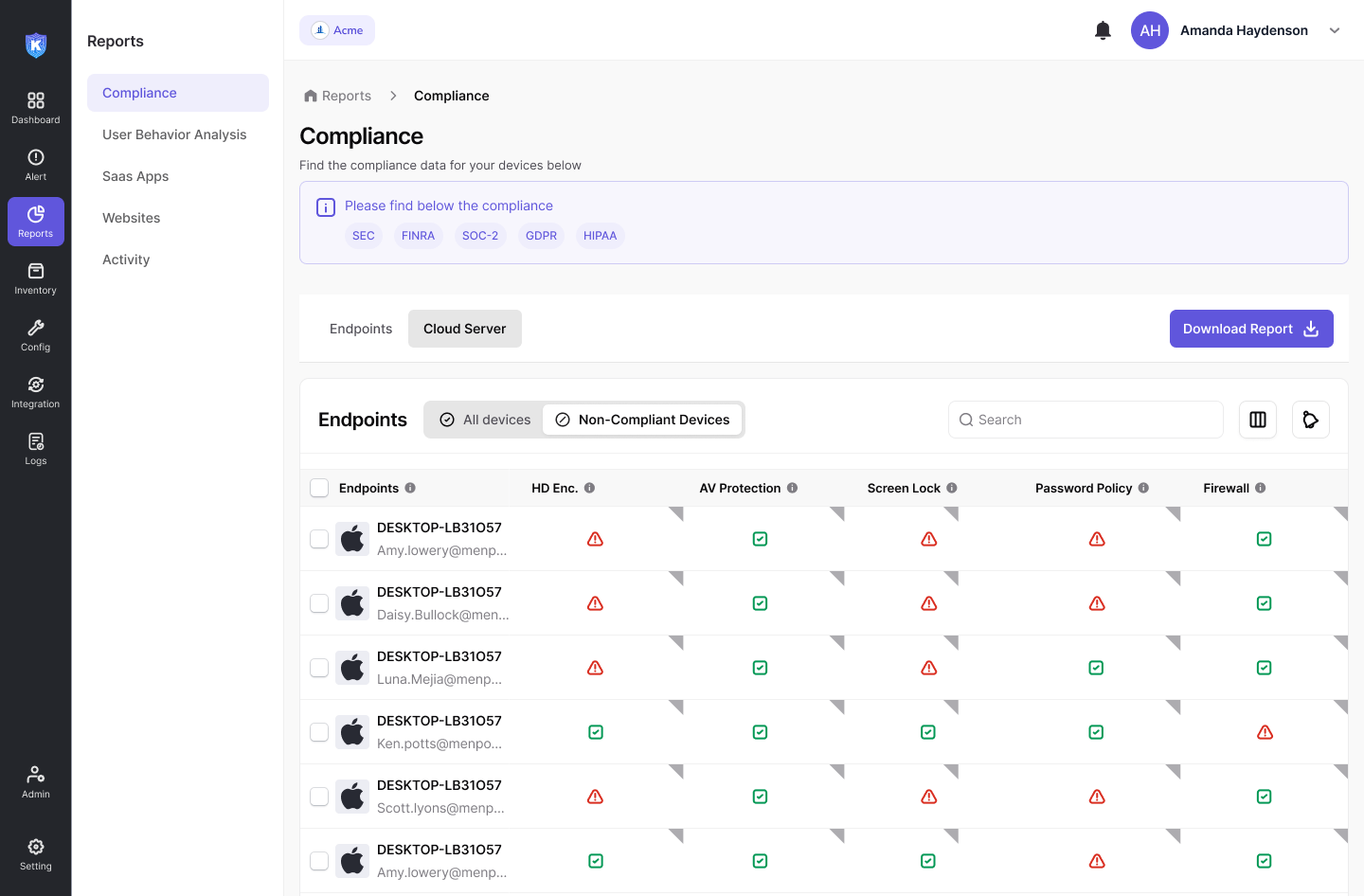
Kitecyber simplifies compliance with built-in monitoring and enforcement for regulations like SEC, FINRA, GDPR, and SOC-2. With predefined endpoint policy templates like HD encryption, AV protection, Screen lock, etc – organizations can ensure their sensitive data stays compliant on all devices.
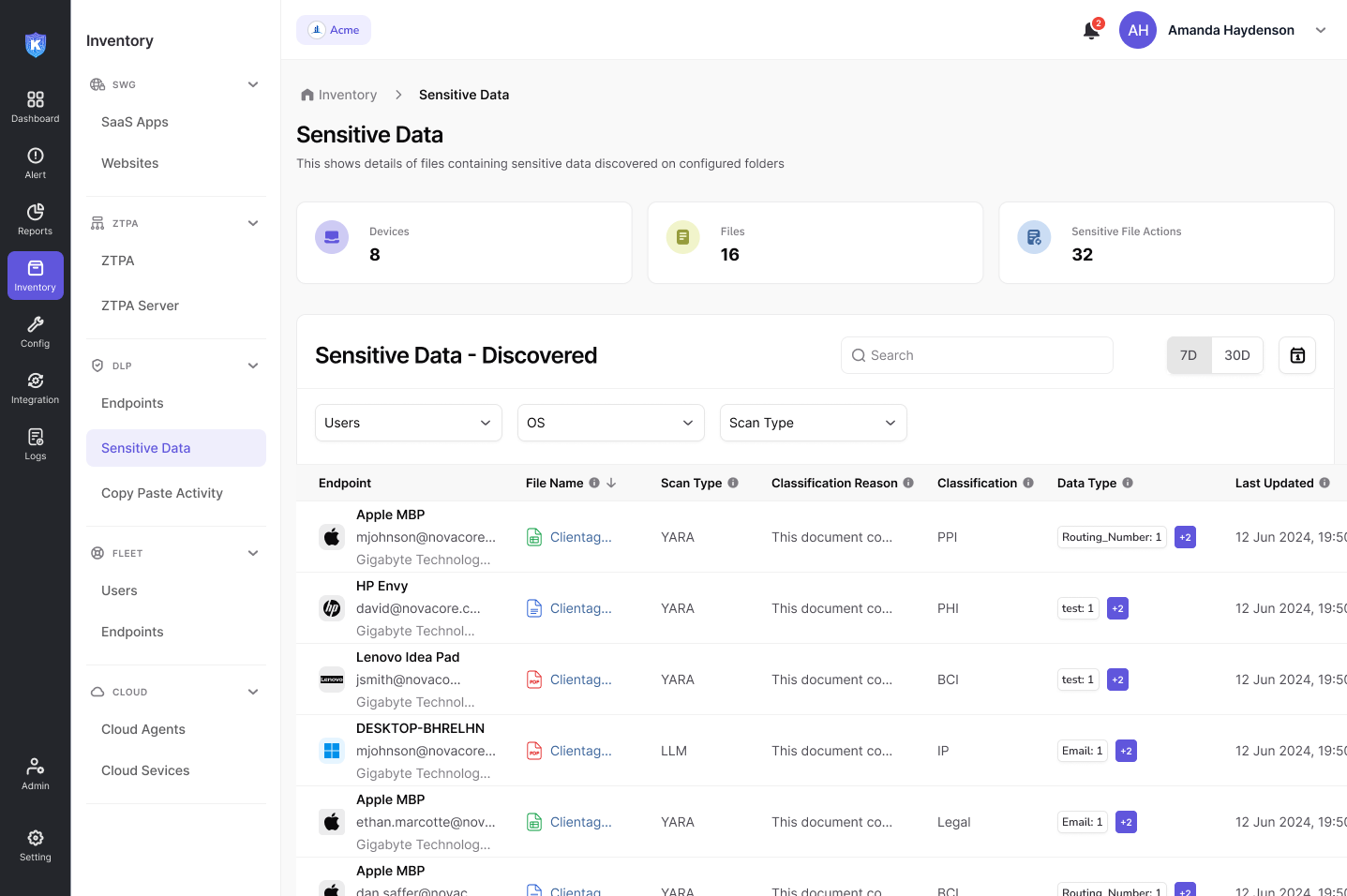
Comprehensive data classification for enhanced security
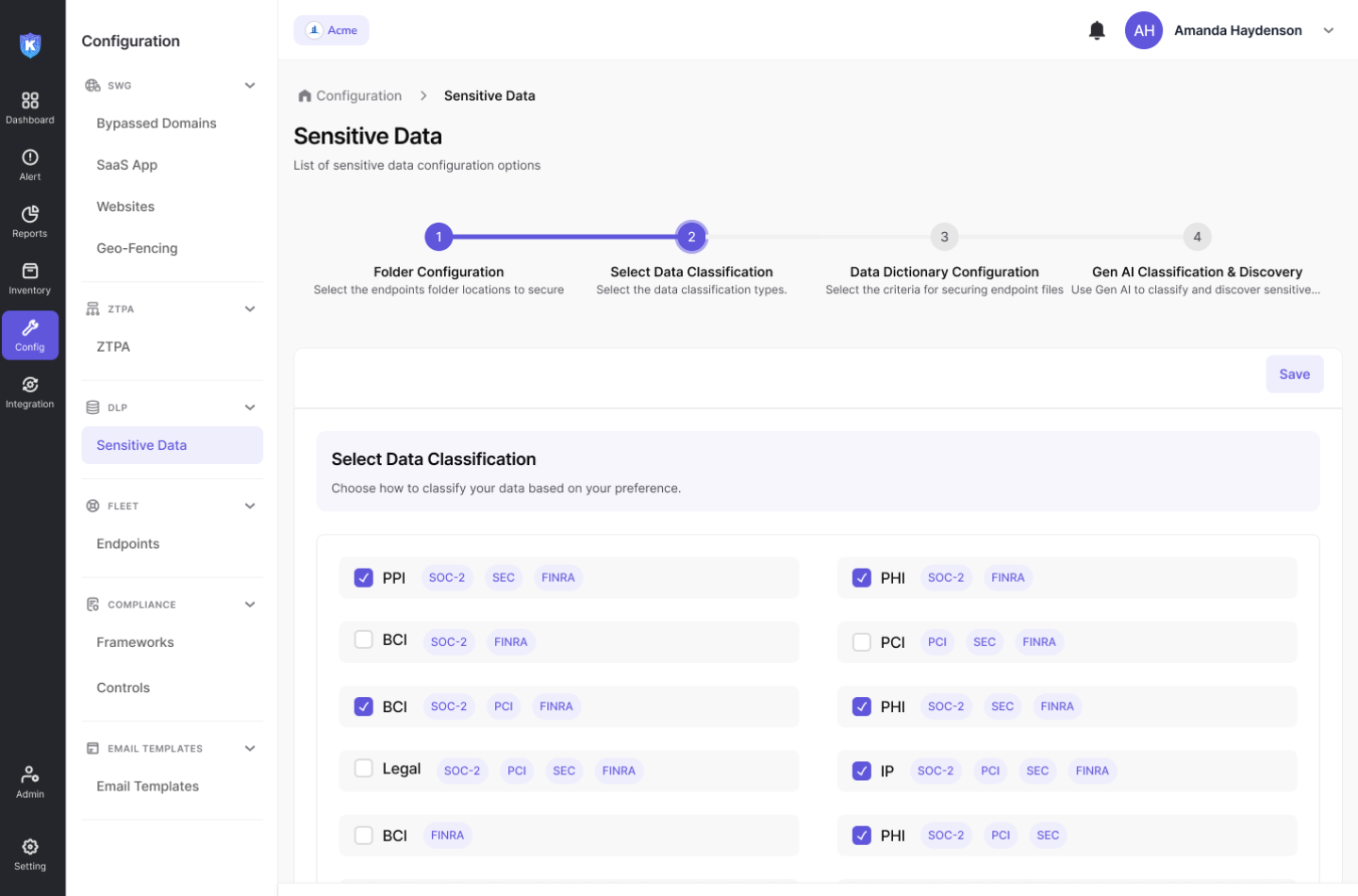
Easily identify and protect sensitive information with Kitecyber’s built-in data classification system. With 80+ pre-configured classifications, organizations can quickly uncover protected health information (PHI), personally identifiable information (PII), and other critical data types. Configure additional data categories to meet specific business and compliance requirements.
Why choose Kitecyber Endpoint Data Loss Prevention?
| Data Discovery & Protection | Kitecyber Data Shield | In-Network DLP (SASE) |
|---|---|---|
Data discovery & Security | HighWorks without exceptions | WeakDoes not work for End-to-End encrypted apps or data that’s password protected or encrypted |
Data Lineage | ComprehensiveAt rest on user device, user activity and network activity | PartialLimited to network visible activity for non encrypted data |
Privacy | YesSelf hosted or SaaS | No3rd Party Cloud |
Compliance | Covered | Gaps |
Performance & Scaling | High | Poor scaling & performanceMultiple levels of traffic redirections with decryption and re-encryption |
Onboarding | SimpleZero Touch Provisioning in minutes | ComplexRequires skilled professional services with weeks to deploy |
Cost | CheaperLeverage edge computer | ExpensiveCloud based solution |
The Kitecyber Advantage
- Before Kitecyber Data Shield
- In-network DLPs only detect what they’re programmed for, leaving real risks like agentic AI apps and insider threats unnoticed.
- IT waits for about 2 months to deploy hard-to-configure DNS rules, which frustrates employees
- In-network DLPs leave scanning all file types and ignore files of bigger size.
- After Kitecyber Data Shield
- Kitecyber Data Shield runs on your endpoint, adapts to users behaviour, and detects all shadow AI, supply chain apps, and insider actions.
- IT starts tracking sensitive data movement in a few days after copilot deployment.
- Kitecyber Data Shield scan files of all types and sizes .
Use-case
Ensure data security and compliance without slowing teams
Regulatory
Compliance
Ensure adherence to industry regulations like GDPR, HIPAA, and PCI DSS by safeguarding sensitive data across endpoints and SaaS platforms.
Protection of
Confidential Information
Defend your intellectual property and business secrets from breaches caused by insider threats or external attacks.
Prevention of
Data Exfiltration
Stop unauthorized data transfers by monitoring and controlling sensitive information flows across your network
Maximizing Data Visibility and Compliance for a Growing Financial Firm
A rapidly expanding financial firm operating in a highly regulated environment, managing large volumes of sensitive customer and financial data.
Our Success Stories
Testimonials

“Kitecyber has been a game changer for our IT and security teams. Now they don’t operate in silos and can see a unified dashboard. We feel much better in our security posture and are saving almost 20 hrs a week in dealing with issues and tickets related to previous solutions. We also saved 50% in our total cost of ownership.”

“Kitecyber helped us with IT, security and compliance as a unified solution. It saved us almost 50% in overall cost as compared to our previous solutions, while significantly improving our security and compliance. the builtin device management and IAM integrations, also optimized our onboarding and offboarding workflows.”

“Kitecyber has been amazing for our SMB customers, who can now enjoy enterprise grade security with a simple and cost effective solution. Instead of dealing with multiple complex solutions, with Kitecyber they can get advanced security with ease using a single copilot”

“No single product prior to Kitecyber could meet so many of the compliance controls while providing advanced SSE protection to SMBs. We are glad to partner with them and integrate with our GRC solution to simplify SMB security and compliance.”

"After being scammed online, we decided to use Kitecyber and it has been awesome to find such a simple and effective security solution with so much coverage. One of the best solutions if you have remote teams who need protection and you need better sleep."
"Robust and reliable cybersecurity platform for device management, secure browsing and VPN"
Kitecyber stood out as a single product that is able to replace multiple point solutions. It was very easy to install even without having any secur...
Read More >>

"Lightweight, Powerful, and Built for Modern Teams to make Endpoint Security Surprisingly Simple"
We've been using KiteCyber for several months now, and it has quickly become a cornerstone of our security stack. The standout benefit is how effor...
Read More >>

"Intuitive yet robust security software"
KitCyber has been extremely simple for us to install for end point security. The built in device management and custom security rules for users has been extremely useful. In addition to protecting from...
Read More >>

"Effective and User-Friendly Cybersecurity Monitoring Platform"
The platform is easy to navigate, with clean dashboards and intuitive workflows. It provides timely threat insights and helps us track incidents efficiently. The customer support team is responsive...
Read More >>

"Easy- Single platform for all IT Security and compliance"
We've had a great experience with KiteCyber — it's a truly user-friendly platform that made onboarding incredibly smooth. The setup process was impressively quick, taking less than an hour...
Read More >>

"ZTNA, URL/App Controls & MDM - all in one"
We’ve been using the platform for ZTNA, URL/App controls, and MDM, and it’s been a smooth experience. It’s feature-rich but easy to use, which made setup and daily management...
Read More >>

"Reliable and Efficient Cybersecurity Partner"
KiteCyber offers an intuitive, well-organized platform that simplifies cybersecurity monitoring and compliance management. The dashboards provide clear visibility into security posture,...
Read More >>

"Hit ESC (Easy. Secure and Cost-effective) key to security gaps, complex and siloed security tools"
Kitecyber gives us a single, easy-to-use dashboard to protect our devices, apps, data, and...
Read More >>

""Best MDM (and much more) for small business and SMBs.""
Product is phenomenal. Price is incredible. The best thing though is how easy their team makes it...
Read More >>

"Top notch team and cybersecurity platform"
What do you like best about Kitecyber?
They have a robust platform, unique in the market. Their.....
Read More >>

"Great MDM, SWG and ZTNA product"
We were looking for security products to cover our need for device management, compliance controls, SaaS security and VPN to cloud...
Read More >>

"Cyber Security plus Remote Team’s Management Support SaaS"
Post experiencing a scam, we went ahead with enrolling KiteCyber and Not only it prevents our database from scammers and hackers...
Read More >>

"Wonderful Application"
What do you like best about Kitecyber?
It is a mix of Jumpcloud and ZTNA application
What do you dislike about Kitecyber?
It blocks unsafe...
Read More >>

"Great endpoint and network security tool"
What do you like best about Kitecyber?
It works very well with GRC solutions like Scrut and make it easy for customers to get security and compliance...
Read More >>

"Great solution to manage devices, team and complaince"
What do you like best about Kitecyber?
It helped me see all the devices in the company, both allocated and unallocated...
Read More >>

"Best cybersecurity product"
What do you like best about Kitecyber?
Identify cyber threats and zero trust vpn connection..The product is very helpful to understand and identify cyber threats..
Read More >>

Case Studies
Customer Success Stories
FAQ's
Frequently asked questions
Endpoint DLP is critical because it secures the last line of defense—user devices—where most data exits occur. Traditional network-based security often fails to detect data exfiltration via USBs, Bluetooth, cloud uploads, or email. Endpoint DLP provides contextual and content-aware controls to prevent both accidental and intentional data leaks, offering protection at the source of data interaction.
Traditional DLP solutions primarily focus on securing data in transit across networks or data at rest in storage. Endpoint DLP, on the other hand, adds robust visibility and control at the device level—covering data-in-use. It addresses data flow through removable media, wireless interfaces, printing, and virtual environments, ensuring comprehensive coverage.
Key features of Endpoint DLP Software include:
- Data Discovery and Classification: Identifying sensitive data and categorizing it by type and importance.
- Content Monitoring and Filtering: Tracking data movement and enforcing security policies based on data type or context.
- Policy Enforcement: Enforcing customizable rules to allow or block certain actions, such as data sharing or uploading.
Encryption and - Access Control: Encrypting sensitive data and restricting access to authorized users.
- Incident Response and Reporting: Providing alerts, logs, and reports to help identify potential threats and respond to incidents quickly.
Kitecyber’s endpoint DLP solution protects data in three primary states:
- Data in Use: Kitecyber Data Shield monitors data actively being used on devices, such as files being edited or transferred, and ensures sensitive information is handled appropriately.
- Data in Motion: It inspects data as it travels over the network, blocking unauthorized sharing or transmission outside of the secure environment.
- Data at Rest: Kitecyber Data Shield secures stored data within databases, servers, and other storage systems, detecting potential risks and enforcing policies to protect sensitive information from unauthorized access or accidental exposure.
- Complexity of Deployment: Configuring DLP software to work across various devices and environments can be complex, especially in large organizations.
- User Privacy Concerns: Monitoring data activities can raise privacy issues, making it essential to balance security with user privacy.
- High False Positives: DLP tools may trigger false positives, flagging legitimate activities as threats, which can overwhelm security teams.
- Scalability: As organizations grow, scaling DLP solutions to accommodate more data sources and endpoints can be challenging.
- Maintenance and Policy Updates: DLP policies require regular updates to adapt to new threats, regulatory requirements, and organizational changes.
- Data Protection:Endpoint DLP secures sensitive data on individual devices, ensuring it's not leaked or misused.
- Monitoring and Control:These solutions monitor data access and usage on endpoints, allowing for the detection of potential leaks or unauthorized activities.
- Policy Enforcement:Endpoint DLP enforces data protection policies, blocking unauthorized data transmissions and other actions that could compromise sensitive data.
- Remediation:When a potential data breach is detected, endpoint DLP can take remedial actions, such as blocking access or initiating a forensic investigation.
- BYOD Support:Endpoint DLP is particularly important in organizations that have Bring Your Own Device (BYOD) policies, ensuring data remains protected even when accessed from personal devices.