Feeling overburdened with IT, Security & Compliance?
AI Powered IT & Security
Automation Software
- Covers MDM, SWG, DLP & ZTNA
- Gen AI Based Automation & Prevention
- Highly Secure Endpoint Based Architecture
- Unified Policy Management and Enforcement
hybrid work, and cloud services. The result is a growing IT gap: too
many tools, too many tickets, too little time, and too much risk. Kitecyber
solves this with an agentic system of action for IT and security.

We replace manual IT and Security with intelligent Agentic AI
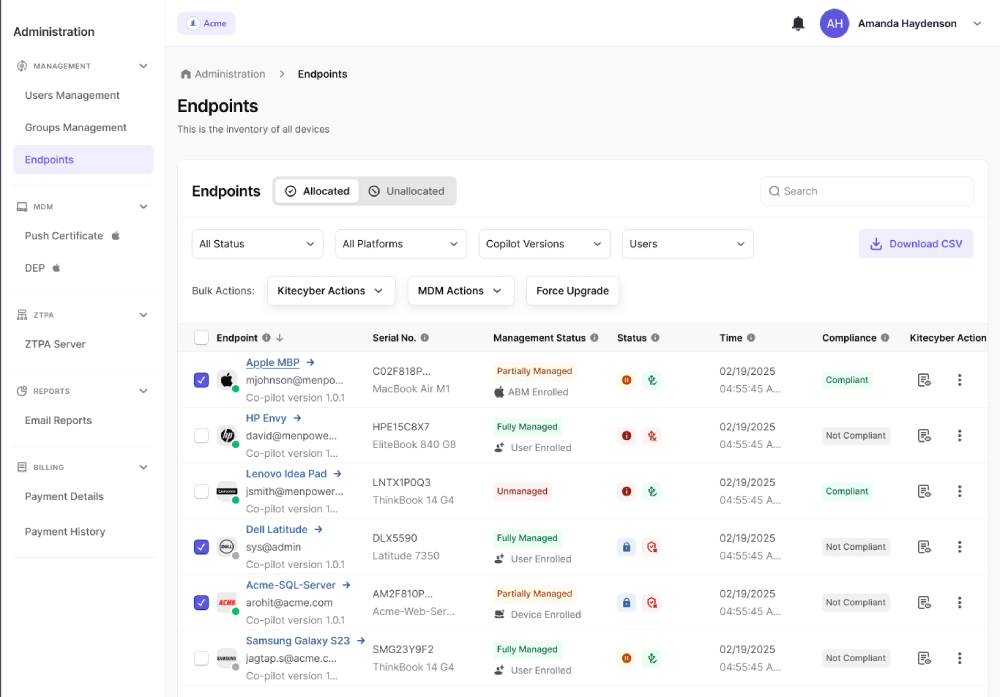
Manage and secure endpoints
Deploy, patch, and secure Mac, Windows, Linux, and iOS devices. Push policies and apps as needed. Eliminate manual tickets & long wait time.

Protect data everywhere
Stop data leaks at the endpoint and network. Block unauthorized transfers, USB misuse, and risky SaaS uploads.

Automate IT support
AI Helpdesk resolves common tickets automatically. Compliance controls enforce continuously. Malicious websites are blocked instantly. Endpoint and network DLP run automatically. No manual intervention needed.
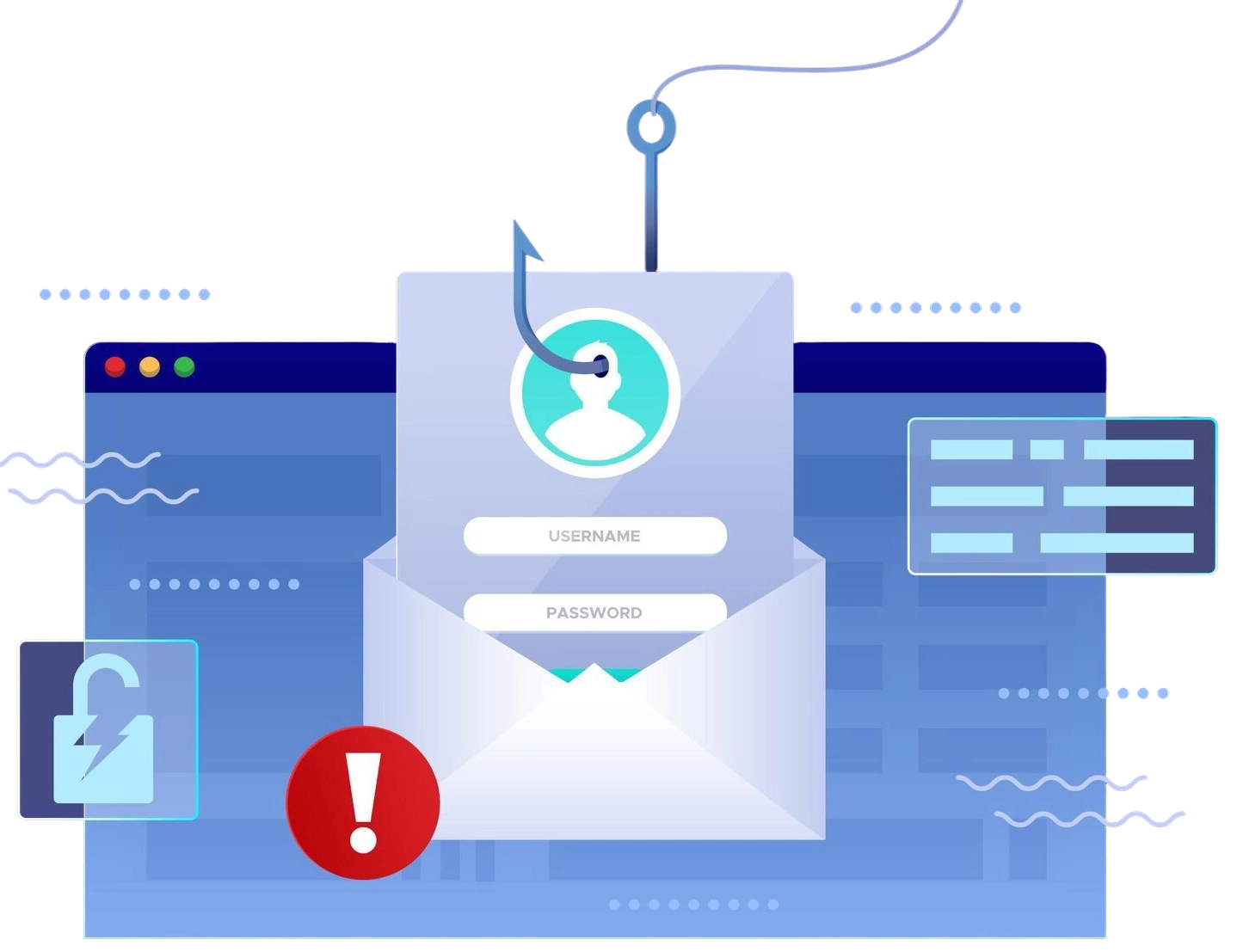
AI powered IT & Security Platform that replaces manual work.
Stop deploying too many point solutions for IT & Security. Kitecyber deploys a single agent to manage devices and provide secure access to your SaaS or private applications. Common IT tasks like onboarding/ offboarding a user, troubleshooting performance issues, meeting compliance controls are fully automated.
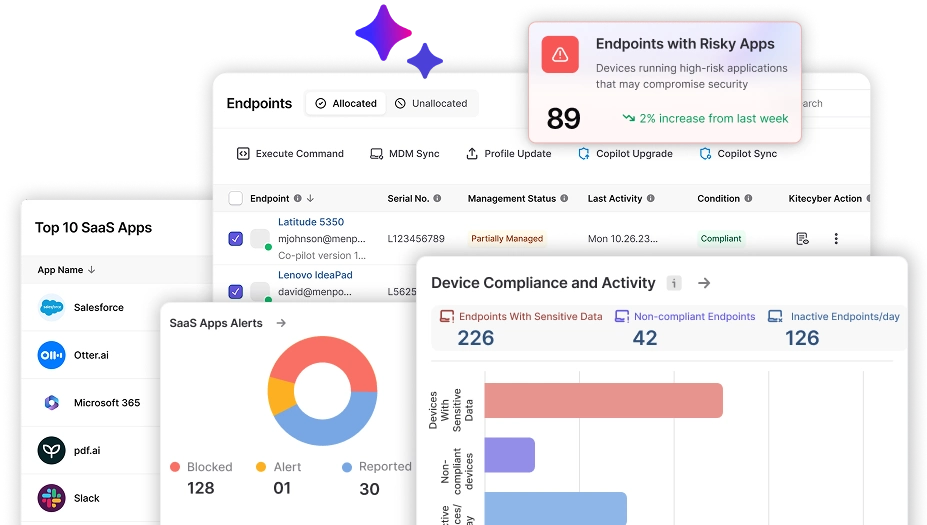
Remotely Manage Every Device With Complete Control
Manage macOS, Windows, Linux, and iOS mobile devices from anywhere using Kitecyber’s multi-OS device management platform. Support your remote/ BYOD work environment from anywhere with adaptable, RMM tools customized to your needs.
- Monitor, patch, and secure endpoints without switching tools;
- Distribute applications remotely and control browser extensions;
- MDM with remote lock and wipe, for employee onboarding/offboarding;
- Enforce compliance controls across all devices.
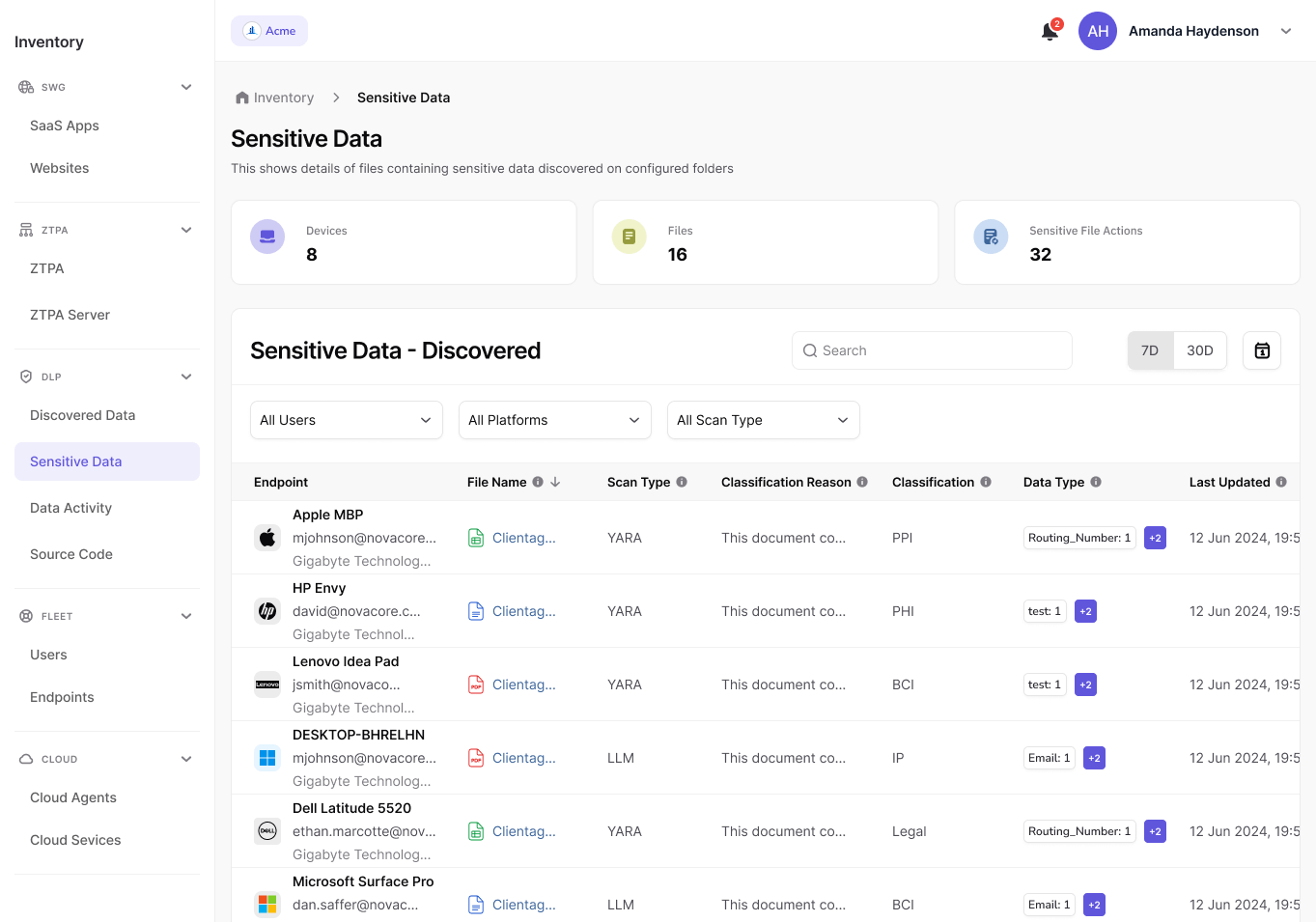
Prevent Sensitive Data Loss on Endpoints and Network
Prevent data leaks before they happen with Kitecyber DLP. Protect sensitive data directly on user devices and as it moves across the network, without disrupting users productivity. Automatically discover and classify sensitive data on endpoints, and enforce policies in real time.
- Track intentional or unintentional employee intentions like unauthorized file uploads on web/ SaaS apps, USB copying, clipboard misuse, and print misuse.
- Train employee about your organization data loss prevention policy and activities using a single endpoint agent;
- Enforce device controls like disk encryption, password policy, anti-virus controls, etc. consistently across Windows, macOS, and Linux devices.
Secure Web Gateway that prevents network data leak
- Block access to risky websites, malicious domains, and unsanctioned SaaS applications;
- Gain visibility into website visits, user behavior, and SaaS apps usage from a single platform;
- Block sensitive data from leaking out to different geographies using Geofencing.
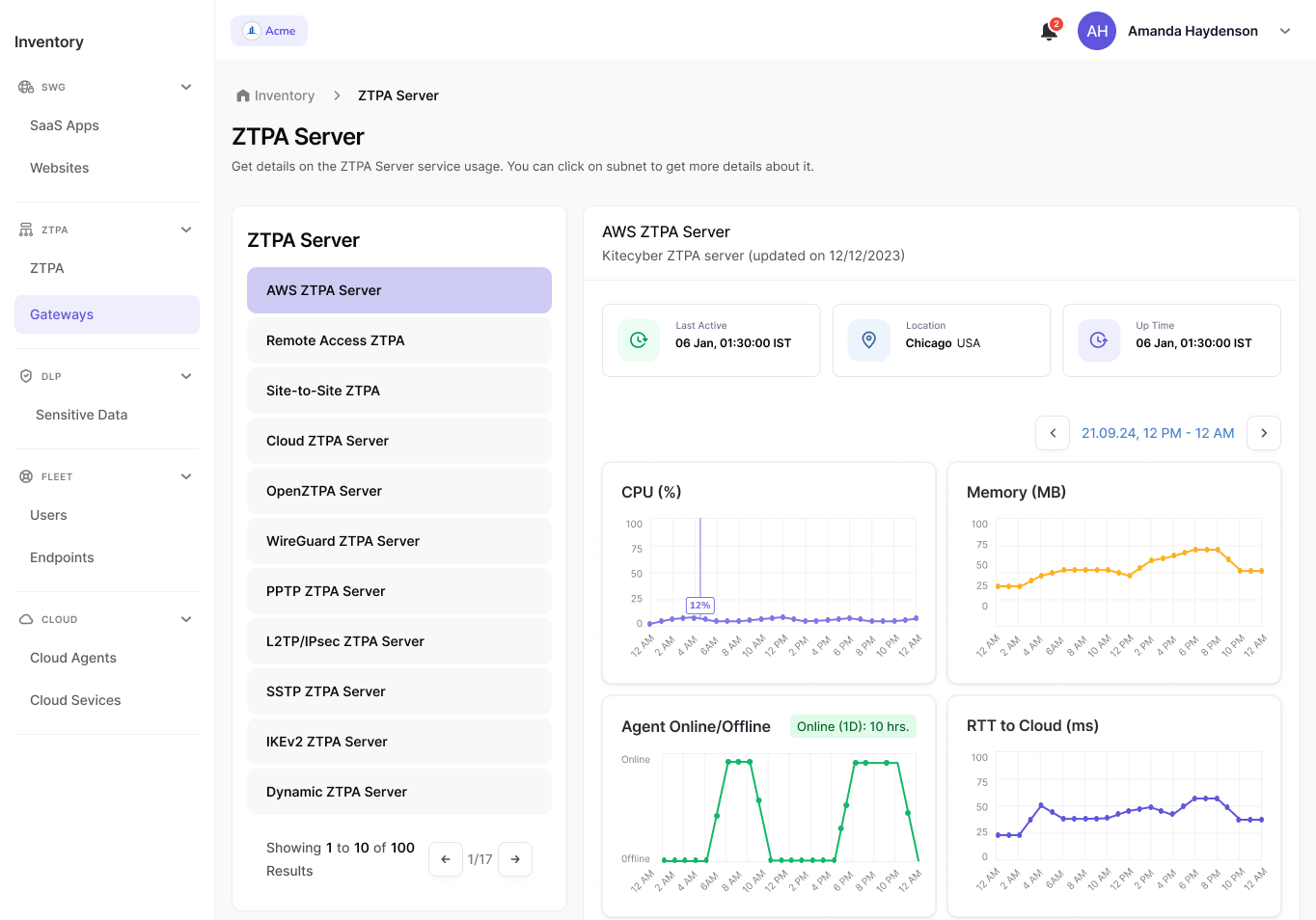
Secure Private Access Without VPN Complexity
Enable users to securely access internal applications and resources from anywhere with Kitecyber Zero Trust Network Access (ZTNA). Replace traditional VPNs with identity and device-aware access controls. Grant application-level access instead of exposing entire networks.
- Verify user identity, device health, and security posture before allowing access;
- Provide seamless and fast connectivity for remote and hybrid teams;
- Reduce attack surface by applying Zero Trust policies across users, devices, and locations.
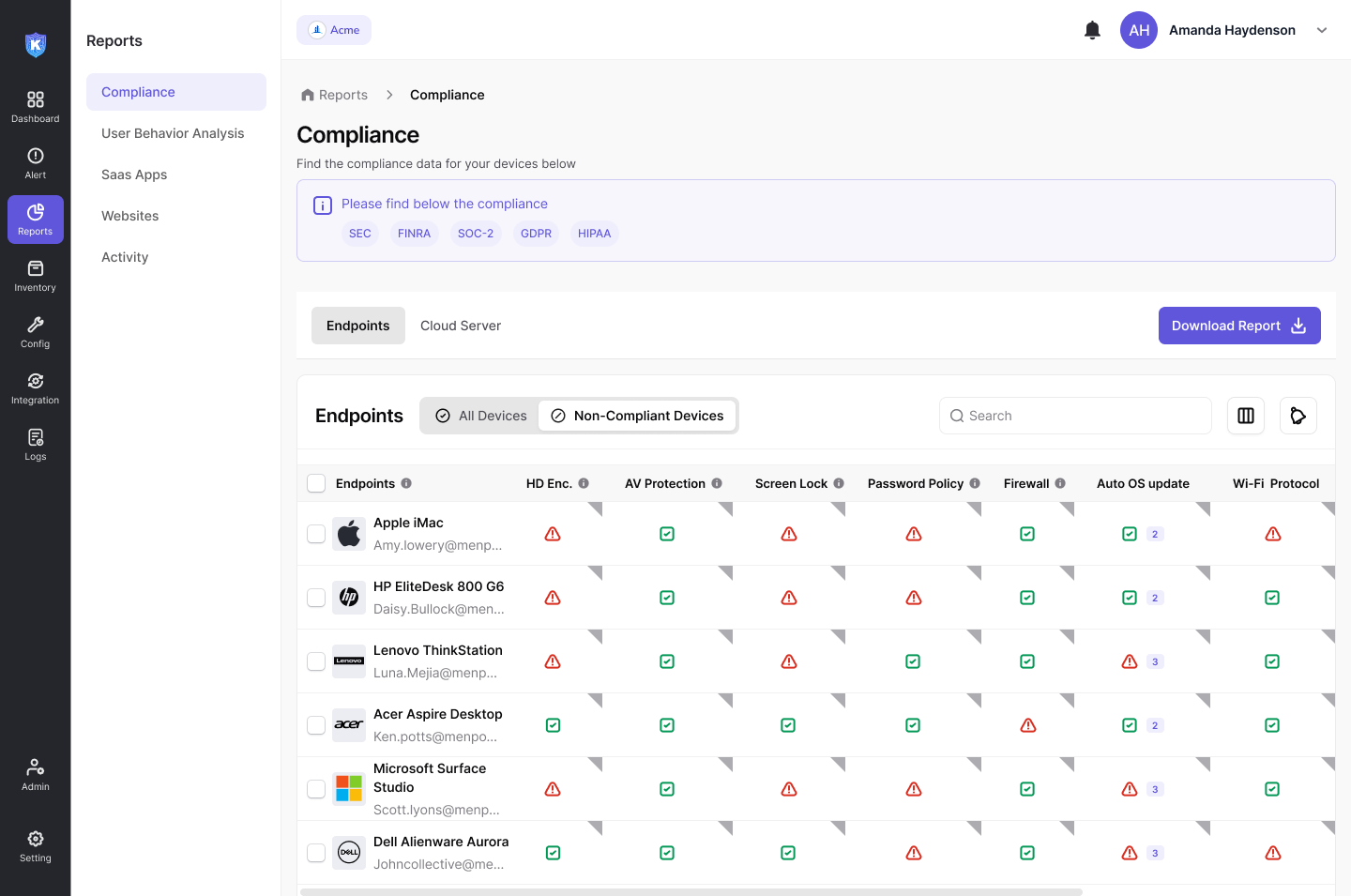
Simplify IT Risk Management with Compliance Enforcement
Stay compliant and reduce operational risk with Kitecyber Compliance. Continuously monitor devices, users, internet and applications against security and compliance policies from a single platform.
- Get daily/ weekly/ monthly incident reports of any compliance violation across company;
- Align IT operations with frameworks like SOC 2, ISO 27001, HIPAA, and internal security standards;
- Reduce compliance workload while strengthening your overall security posture.
Endpoint and Network Security using Gen AI
Any device, any OS. AI Powered IT & security, always.
Windows OS
Secure Windows endpoints throughout the organisation with advanced protection tools.
MacOS
Ensure your employee's MacBooks stay safe & protected with MacOS endpoint security and MDM
Linux OS
Safeguard your Linux devices with tailored endpoint security
How Kitecyber Closes the IT Gap
Agentic System of Action for IT & Security
What changes:
- Employees get instant support through AI chatbot
- AI resolves common tickets without IT involvement
- Device compliance enforced continuously
- Security policies applied in real-time
- Data protection active at every endpoint
- Employees get trained of company’s security policy
- The result: 80% Fewer Tickets. 60% Lower MTTR. 60% Lower cost.

Use cases
IT & Security solutions engineered with you in mind.
Ensure compliance & improve security posture
Single platform for UEM, SWG, ZTNA, and DLP. Audit-ready reporting built in.
Control SaaS sprawl & reduce costs
Discover shadow IT. Block SSO bypasses. Cut unnecessary licenses.
Prevent data exfiltration
Track and block unauthorized transfers and insider threats, even in encrypted channels.
Detect insider threats with UEBA
AI baselines normal behavior. Flags anomalies for fast investigation.
Stop phishing in real-time
Endpoint-based protection blocks credential theft instantly—no training required.
Manage third-party API risks
Discover, control, and block unauthorized API connections before they escalate.
| Category | AI Powered IT & Security | Legacy Solutions |
|---|---|---|
Technology | Built from the ground up using Gen AI, lightweight, high-performant edge-based design. | Traditional SaaS built in the pre Gen AI era. No agentic automation. |
Product Innovation | Unified agentic AI architecture for IT & Security | No user guidance, inefficient network based architecture, dumb alerts burdening SOC and IT teams |
Network Security Performance | Direct-to-app connection. No hair pinning of traffic. | High latency and bandwidth constraints due to routing through regional PoPs and cloud gateways. . |
Data Routing and Privacy | No man in the middle seeing your data | Data going through third party vendors and may go to other countries due to PoP locations |
BYOD Support | Designed for unmanaged devices. Separate policies for BYOD devices and company owned devices | Network based solutions. No control over the endpoint, leading to poor or no BYOD coverage. |
Mean Time to Resolution (MTTR) | Within minutes using AI agents instead of hours or days | Multiple days; Manual ticket resolution using standard ticketing systems |
Alerts Quality & Analysis | Native LLM-powered detections and incident report generation to lower false-positive rates. | Relies on legacy rule-based detection engines. Limited LLM integration, higher false positives. |
Deployment | Super easy to set up, designed for self-service. | 2 to 3 month rollout requiring consultants and extensive IT effort |
Cost Structure | Significantly lower due to the endpoint based architecture and agentic automation | Much higher cost due to manual work and complex security architecture |
Talk to a Security Expert Today.
Our Success Stories
Testimonials

“Kitecyber has been a game changer for our IT and security teams. Now they don’t operate in silos and can see a unified dashboard. We feel much better in our security posture and are saving almost 20 hrs a week in dealing with issues and tickets related to previous solutions. We also saved 50% in our total cost of ownership.”

“Kitecyber helped us with IT, security and compliance as a unified solution. It saved us almost 50% in overall cost as compared to our previous solutions, while significantly improving our security and compliance. the builtin device management and IAM integrations, also optimized our onboarding and offboarding workflows.”

“Kitecyber has been amazing for our SMB customers, who can now enjoy enterprise grade security with a simple and cost effective solution. Instead of dealing with multiple complex solutions, with Kitecyber they can get advanced security with ease using a single copilot”

“No single product prior to Kitecyber could meet so many of the compliance controls while providing advanced SSE protection to SMBs. We are glad to partner with them and integrate with our GRC solution to simplify SMB security and compliance.”

"After being scammed online, we decided to use Kitecyber and it has been awesome to find such a simple and effective security solution with so much coverage. One of the best solutions if you have remote teams who need protection and you need better sleep."
Awards & Recognitions

"Robust and reliable cybersecurity platform for device management, secure browsing and VPN"
Kitecyber stood out as a single product that is able to replace multiple point solutions. It was very easy to install even without having any secur...
Read More >>

"Lightweight, Powerful, and Built for Modern Teams to make Endpoint Security Surprisingly Simple"
We've been using KiteCyber for several months now, and it has quickly become a cornerstone of our security stack. The standout benefit is how effor...
Read More >>

"Intuitive yet robust security software"
KitCyber has been extremely simple for us to install for end point security. The built in device management and custom security rules for users has been extremely useful. In addition to protecting from...
Read More >>

"Effective and User-Friendly Cybersecurity Monitoring Platform"
The platform is easy to navigate, with clean dashboards and intuitive workflows. It provides timely threat insights and helps us track incidents efficiently. The customer support team is responsive...
Read More >>

"Easy- Single platform for all IT Security and compliance"
We've had a great experience with KiteCyber — it's a truly user-friendly platform that made onboarding incredibly smooth. The setup process was impressively quick, taking less than an hour...
Read More >>

"ZTNA, URL/App Controls & MDM - all in one"
We’ve been using the platform for ZTNA, URL/App controls, and MDM, and it’s been a smooth experience. It’s feature-rich but easy to use, which made setup and daily management...
Read More >>

"Reliable and Efficient Cybersecurity Partner"
KiteCyber offers an intuitive, well-organized platform that simplifies cybersecurity monitoring and compliance management. The dashboards provide clear visibility into security posture,...
Read More >>

"Hit ESC (Easy. Secure and Cost-effective) key to security gaps, complex and siloed security tools"
Kitecyber gives us a single, easy-to-use dashboard to protect our devices, apps, data, and...
Read More >>

""Best MDM (and much more) for small business and SMBs.""
Product is phenomenal. Price is incredible. The best thing though is how easy their team makes it...
Read More >>

"Top notch team and cybersecurity platform"
What do you like best about Kitecyber?
They have a robust platform, unique in the market. Their.....
Read More >>

"Great MDM, SWG and ZTNA product"
We were looking for security products to cover our need for device management, compliance controls, SaaS security and VPN to cloud...
Read More >>

"Cyber Security plus Remote Team’s Management Support SaaS"
Post experiencing a scam, we went ahead with enrolling KiteCyber and Not only it prevents our database from scammers and hackers...
Read More >>

"Wonderful Application"
What do you like best about Kitecyber?
It is a mix of Jumpcloud and ZTNA application
What do you dislike about Kitecyber?
It blocks unsafe...
Read More >>

"Great endpoint and network security tool"
What do you like best about Kitecyber?
It works very well with GRC solutions like Scrut and make it easy for customers to get security and compliance...
Read More >>

"Great solution to manage devices, team and complaince"
What do you like best about Kitecyber?
It helped me see all the devices in the company, both allocated and unallocated...
Read More >>

"Best cybersecurity product"
What do you like best about Kitecyber?
Identify cyber threats and zero trust vpn connection..The product is very helpful to understand and identify cyber threats..
Read More >>

What’s happening
Insights and Blogs

Best Windows DLP Solution in 2026: Stop Data Leaks Before They Cost You Millions

11 Best IT Security Management Software in 2026: Ranked, Tested, and Proven

10 Critical Apple MDM Solutions You Must Deploy Before 2026
FAQ's
Frequently asked questions
Kitecyber implements security compliance policies, endpoint security and protection, sensitive data protection, Internet phishing protection, and Gen AI-based SaaS security. It monitors activity across devices and applications to ensure comprehensive protection without impacting productivity.
Kitecyber is built on the top of Device Trust engine and Zero Trust Principles. It eliminates expensive cloud gateways and VPN appliances, thereby ensuring there is no man-in-the-middle to offer you security. This architecture is endpoint-centric, which includes multiple layers of security. This ensures each layer can help tackle a different vulnerability in endpoints. These layers consist of SWG, data loss prevention tools (DLP), and ZTNA solution for protecting the endpoints.
Kitecyber operates at the user endpoint and identity level, providing visibility into shadow SaaS usage, advanced insider threat detection, and precise data security enforcement, without relying on perimeter-based controls.
Yes, Kitecyber integrates with IAM providers such as Okta, Azure AD, and Google Workspace, amongst others. We also partner and integrate with different GRC solutions, ensuring you stay on top of compliance. When bundled with antivirus or EDR, Kitecyber provides full cybersecurity protection.
Yes, Kitecyber uses identity-based monitoring to identify unauthorized SaaS applications and alerts organizations to shadow IT risks, providing actionable insights to regain control over unmanaged SaaS sprawl.
Kitecyber automates compliance by discovering, classifying, and securing sensitive data. Its reporting and security policies support regulations like PCI DSS, GDPR, and HIPAA, reducing compliance risks.
Yes, Kitecyber detects anomalous user behavior—such as unauthorized data access, sharing, or movement—and provides context and lineage to reduce risks from malicious or careless insiders.
Kitecyber tracks sensitive data lineage across devices, email, SaaS applications, and networks in real time, providing granular visibility to ensure sensitive data is never exposed or mishandled, thereby improving overall security posture.