Data Exfiltration Detection and
Prevention
Kitecyber is a leading data exfiltration detection and prevention tool.
It continuously discovers sensitive data, monitors flow of this data on the
endpoint and across the network. Eliminate limitations of existing in network
DLP solutions which can be easily bypassed.
Overview
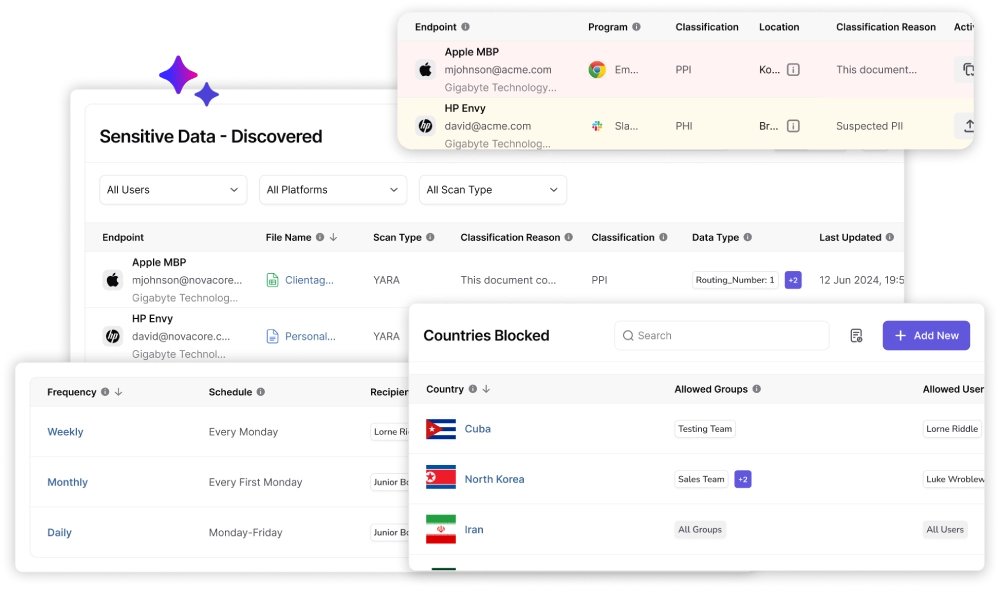
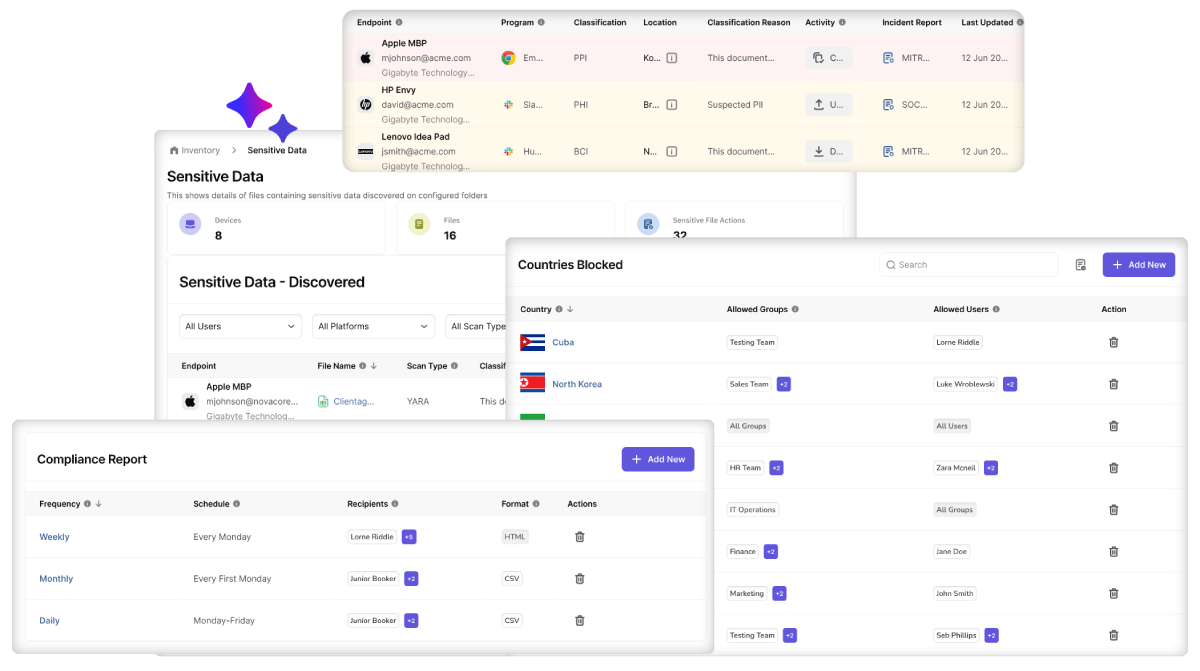
Discover and Protect Sensitive Data
To protect sensitive data exfiltration, you need to understand data operations at the endpoint and data movement on the wire. Furthermore, the solution needs to work for a modern remote workforce that can work from any location and may not send all the data through a single appliance or cloud gateway.
Meet Kitecyber’s hyperconverged DLP solution that combines both endpoint and network DLPs into a single solution operating at the endpoint. This approach provides three unique benefits:
Simple to deploy
It runs on endpoints, so there is no need for cloud gateways or appliances
Comprehensive Data Security
Detect and stop exfiltration attempts in real time, cover both endpoint context and network movement
Cost effective
Small amount of local compute is used, no cloud infrastructure needed
The Problem
Traditional Data Security is Broken
DSPM solutions that discover sensitive data across various cloud storage repositories,
In network DLP solutions that do decryption and reencryption of data to look for sensitive data leakage...
Endpoint DLLP solutions which operate primarily on the endpoint but do not have visibility into network traffic.
Siloed Tools
Fragmented security solutions fail to provide a unified view, leaving gaps in your data protection strategy
Compliance Struggles
Meeting regulatory requirements becomes a nightmare with disjointed tools and unmonitored access
Evolving Threats
Cyberattacks, such as ransomware and data exfiltration, exploit these vulnerabilities faster than you can patch them
Uncover risks and hidden costs
Sensitive data exfiltration at endpoints could lead to serious consequences
65%
data exfiltration happens on corporate devices - Venafi
64%
of financial service organizations have 1,000 or more sensitive files available to every employee - Zenarmor.com
5.67%
of all traffic was data exfiltration to the Dark Web. - BlackFog
Solution Overview
Kitecyber: Industry's first Hyperconverged Data Exfiltration Detection Tool
Stop data exfiltration from any endpoint
One product and policy that covers all endpoints and outbound network access. Leverage endpoint and network context in a single solution
Understand how data
flows
Protect sensitive data at granular level as files are downloaded, edited or transmitted. Identify sensitive data on all endpoints, where it came from and where it may have gone.
Detect and stop risky user behavior
Monitor how data flows across devices and apps in real time. Detect data leakage and alert users in real time, warn them when sensitive data is being copied or moved
Access Governance with Granular Policies
Take full control of sensitive data. Define who can access what based on roles, devices, or locations. Enforce security policies with minimal disruption to workflows.
Data Compliance
Management
Automatically align your data security with industry standards like SOC2, ISO27001, HIPAA, PCI-DSS, GDPR etc.
Benefits
Safeguard critical data with compliance enforcement
Minimize
Risk
Prevent leaks, theft, or unauthorized transfers before they happen.
Simplify
Compliance
Achieve regulatory requirements with centralized policy management and automated report generation
Streamline Investigations
Quickly identify suspicious copy paste activities and respond with blocking access to internal or SaaS apps, quarantine or remote lock a device if needed
Reduce Operational Burden
Replace disjointed tools with one unified platform for seamless protection
Why Kitecyber?
Lightweight and Simple Deployment
Easy setup without impacting user experience.
Broad Coverage
Secure data across SaaS apps, Gen AI apps, endpoints, and cloud.
Low Cost
Eliminate expensive appliances or cloud gateways. Leverage endpoint compute resources
Our Success Stories
Testimonials

“Kitecyber has been a game changer for our IT and security teams. Now they don’t operate in silos and can see a unified dashboard. We feel much better in our security posture and are saving almost 20 hrs a week in dealing with issues and tickets related to previous solutions. We also saved 50% in our total cost of ownership.”

“Kitecyber helped us with IT, security and compliance as a unified solution. It saved us almost 50% in overall cost as compared to our previous solutions, while significantly improving our security and compliance. the builtin device management and IAM integrations, also optimized our onboarding and offboarding workflows.”

“Kitecyber has been amazing for our SMB customers, who can now enjoy enterprise grade security with a simple and cost effective solution. Instead of dealing with multiple complex solutions, with Kitecyber they can get advanced security with ease using a single copilot”

“No single product prior to Kitecyber could meet so many of the compliance controls while providing advanced SSE protection to SMBs. We are glad to partner with them and integrate with our GRC solution to simplify SMB security and compliance.”

"After being scammed online, we decided to use Kitecyber and it has been awesome to find such a simple and effective security solution with so much coverage. One of the best solutions if you have remote teams who need protection and you need better sleep."
Awards & Recognitions

"Robust and reliable cybersecurity platform for device management, secure browsing and VPN"
Kitecyber stood out as a single product that is able to replace multiple point solutions. It was very easy to install even without having any secur...
Read More >>

"Lightweight, Powerful, and Built for Modern Teams to make Endpoint Security Surprisingly Simple"
We've been using KiteCyber for several months now, and it has quickly become a cornerstone of our security stack. The standout benefit is how effor...
Read More >>

"Intuitive yet robust security software"
KitCyber has been extremely simple for us to install for end point security. The built in device management and custom security rules for users has been extremely useful. In addition to protecting from...
Read More >>

"Effective and User-Friendly Cybersecurity Monitoring Platform"
The platform is easy to navigate, with clean dashboards and intuitive workflows. It provides timely threat insights and helps us track incidents efficiently. The customer support team is responsive...
Read More >>

"Easy- Single platform for all IT Security and compliance"
We've had a great experience with KiteCyber — it's a truly user-friendly platform that made onboarding incredibly smooth. The setup process was impressively quick, taking less than an hour...
Read More >>

"ZTNA, URL/App Controls & MDM - all in one"
We’ve been using the platform for ZTNA, URL/App controls, and MDM, and it’s been a smooth experience. It’s feature-rich but easy to use, which made setup and daily management...
Read More >>

"Reliable and Efficient Cybersecurity Partner"
KiteCyber offers an intuitive, well-organized platform that simplifies cybersecurity monitoring and compliance management. The dashboards provide clear visibility into security posture,...
Read More >>

"Hit ESC (Easy. Secure and Cost-effective) key to security gaps, complex and siloed security tools"
Kitecyber gives us a single, easy-to-use dashboard to protect our devices, apps, data, and...
Read More >>

""Best MDM (and much more) for small business and SMBs.""
Product is phenomenal. Price is incredible. The best thing though is how easy their team makes it...
Read More >>

"Top notch team and cybersecurity platform"
What do you like best about Kitecyber?
They have a robust platform, unique in the market. Their.....
Read More >>

"Great MDM, SWG and ZTNA product"
We were looking for security products to cover our need for device management, compliance controls, SaaS security and VPN to cloud...
Read More >>

"Cyber Security plus Remote Team’s Management Support SaaS"
Post experiencing a scam, we went ahead with enrolling KiteCyber and Not only it prevents our database from scammers and hackers...
Read More >>

"Wonderful Application"
What do you like best about Kitecyber?
It is a mix of Jumpcloud and ZTNA application
What do you dislike about Kitecyber?
It blocks unsafe...
Read More >>

"Great endpoint and network security tool"
What do you like best about Kitecyber?
It works very well with GRC solutions like Scrut and make it easy for customers to get security and compliance...
Read More >>

"Great solution to manage devices, team and complaince"
What do you like best about Kitecyber?
It helped me see all the devices in the company, both allocated and unallocated...
Read More >>

"Best cybersecurity product"
What do you like best about Kitecyber?
Identify cyber threats and zero trust vpn connection..The product is very helpful to understand and identify cyber threats..
Read More >>

Case Studies
Customer Success Stories
Request a Demo Today
How it works
Frequently asked questions
-
- Data Identification and Classification: Identify and classify sensitive data, whether at rest, in motion, or in use.
-
- Monitoring and Analysis: Track how data is accessed, used, and shared across networks, devices, and endpoints.
-
- Policy Enforcement: Apply security policies to restrict or block unauthorized activities, such as sending sensitive information via email or uploading it to unauthorized cloud storage.
-
- Incident Reporting: Alert security teams to potential data breaches or policy violations.
-
- Compliance Assistance: Help organizations meet regulatory requirements like GDPR, HIPAA, PCI DSS, and others by safeguarding sensitive data.
- Prevent Data Breaches: Mitigate the risk of data theft or leaks caused by cyberattacks, insider threats, or inadvertent sharing.
- Protect Intellectual Property: Safeguard proprietary designs, trade secrets, and research from being exposed to competitors or the public.
- Regulatory Compliance: Avoid hefty fines and reputational damage by ensuring compliance with legal and industry-specific regulations.
- Support Remote Work: Secure sensitive data on employees' devices and prevent accidental sharing in increasingly hybrid work environments.
- Maintain Trust: Protect customer and partner data to build and maintain trust.
- Reduce Financial Losses: Prevent the financial and operational consequences of data breaches, including fines, lawsuits, and recovery costs.
- Preventing unauthorized file transfers.
- Monitoring and securing cloud-based data sharing.
- Blocking sensitive information from being sent via email to external recipients.
- Detecting insider threats and potential data exfiltration.
Common Use Cases:
1. Endpoint DLP
- Scope: Operates directly on endpoints, such as desktops, laptops, mobile devices, and servers.
- Focus: Monitors and protects data at the device level, including data in use, data at rest, and data in motion on endpoints.
- Capabilities:
- Detects and prevents sensitive data from being copied to external drives, USB devices, or shared via apps installed on the endpoint.
- Monitors local file transfers and clipboard activities.
- Blocks unauthorized printing or screen captures of sensitive information.
- Enforces policies for data access and usage on remote or offline devices.
- Deployment: Installed as an agent on endpoints.
- Best Use Cases:
- Securing remote workers’ devices.
- Preventing data leakage from portable devices or local activities.
- Enforcing granular policies based on users or devices.
2. Network DLP
- Scope: Operates at the network level, monitoring and protecting data as it moves across the organization's network.
- Focus: Monitors and protects data in motion, ensuring that sensitive information isn’t transmitted over unsecured or unauthorized channels.
- Capabilities:
- Inspects emails, file transfers, and web traffic for sensitive data.
- Blocks or flags unauthorized outbound communications containing sensitive information.
- Monitors data flowing to and from cloud services or external destinations.
- Integrates with firewalls, secure web gateways, and email security tools.
- Deployment: Installed on network appliances or integrated with network infrastructure.
- Best Use Cases:
- Securing data transmitted over email, messaging, or web uploads.
- Monitoring and controlling file transfers to external servers.
- Protecting sensitive data in large-scale enterprise networks.
- Data Visibility: Identifies where sensitive data resides and how it is being used.
- Policy Enforcement: Automatically enforces data protection policies to comply with legal and regulatory requirements.
- Incident Response: Detects and alerts security teams about potential data breaches.
- Audit and Reporting: Provides logs and evidence of data protection measures for audits.
Kitecyber DLP combines the power of both endpoint and network DLP in a single solution. This makes the solution more comprehensive in terms of security, easy to use and more cost effective.
DSPM solutions focus on analyzing data in various cloud storage areas like object store, databases, data warehouses and cloud drives. They typically analyze the data in these places, classify it and present a single dashboard to view the sensitive data. Some of them also analyze who all have access to sensitive data and manage that access. These are complementary to Kitecyber’s DLP solution as they do not analyze the data on the endpoints or its movement.
Data Security Posture Management (DSPM) tools represent the next evolution in cloud data security solutions, designed to address the complex challenges of protecting sensitive data in modern cloud environments. By implementing a DSPM solution, organizations gain comprehensive visibility into their data across multiple cloud platforms, enabling them to automatically discover, classify, and protect sensitive information while ensuring compliance with regulatory requirements such as GDPR, HIPAA, and PCI DSS. This proactive approach to data security helps organizations prevent costly data breaches and maintain robust security postures in an increasingly complex threat landscape.