INTRODUCING
Kitecyber's Next Gen SSE Solutions

Unified Endpoint (Device) Management & Security
Next Gen Web Gateway for Secure SaaS/ Internet Access
Next Gen Data Loss Prevention (Network + Endpoints)
Zero Trust Network Access (ZTNA)
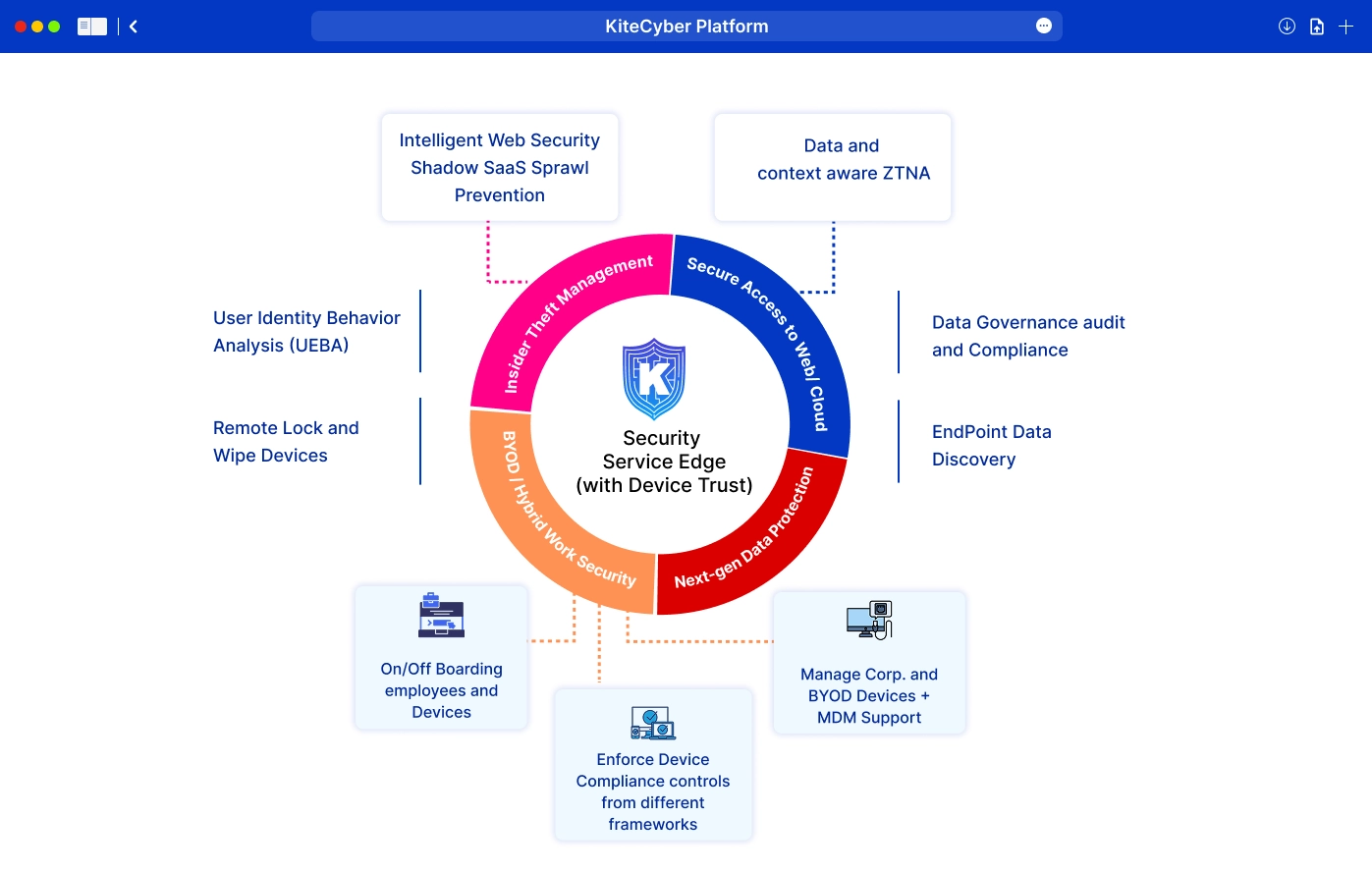
Security Service Edge Unleashed With Kitecyber Platform
Old security tools just don’t cut it anymore. VPNs are slow and clunky. Cloud gateways cause traffic bottlenecks. And your team? They’re working from home, airports, coffee shops, everywhere. That’s why we built Kitecyber, the world’s first hyperconverged suite of SSE solutions that protects users, apps, endpoints and data right from the endpoint. No more relying on overloaded cloud gateways or stacking disconnected tools. Kitecyber combines device security, next-gen secure web gateway, data protection, and Zero Trust network access into a single lightweight endpoint agent. Everything runs through one unified engine, so you get full visibility, smarter policies, and zero integration headaches.
No Cloud Gateway Needed
Say goodbye to bulky, expensive cloud gateways. Kitecyber runs everything right from the endpoint, so there’s no traffic hairpinning, no added latency, and no single point of failure. You get faster performance and stronger security without the overhead.
One Lightweight Endpoint Agent
Everything you need, device management, next-gen secure web gateway, data loss prevention, VPN, SaaS security, and data governance, runs through one smart, conflict-free agent. No bloat. No complexity.
One Integrated Device Trust Engine
All modules share a unified Device Trust Engine that keeps them in sync and eliminates the need for stitching together multiple tools. That means tighter control, fewer gaps, and a stronger security posture, right out of the box.
Endpoint Management and Security With Device Trust
Seamlessly manage and secure Multi-OS or crossplatform corp, BYOD or unmanaged endpoints through a single endpoint security module. Track events and system health metrics like CPU and memory usage for all devices. A lost or stolen device shouldn’t mean lost data. Remote Lock ensures your devices stay locked to your organization, no unauthorized resets, no workarounds, no security gaps. In case of a theft, remotely wipe the data from all devices to prevent a data breach.
Secure Internet and SaaS Access With Next Gen SWG
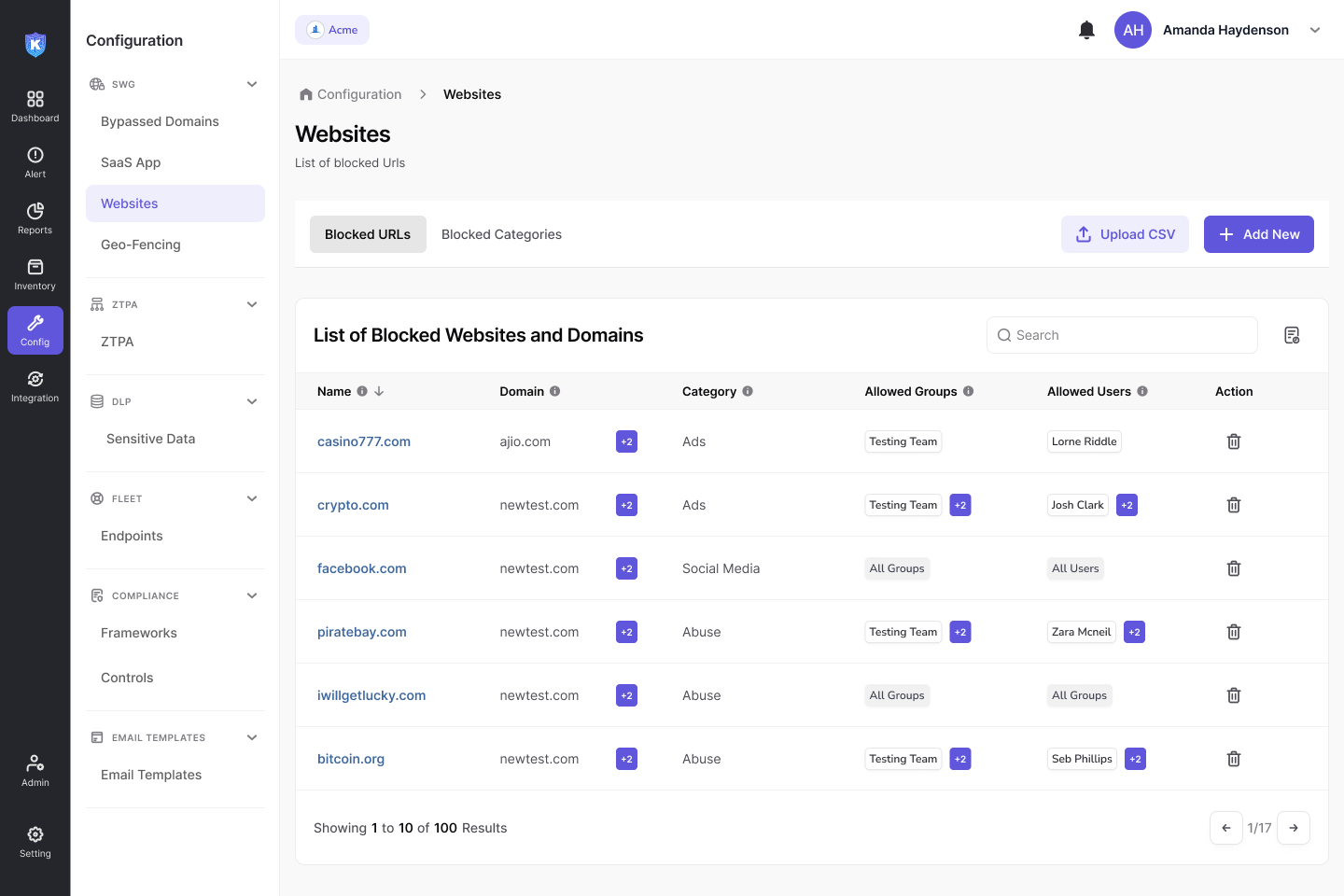
Block malicious websites and prevent phishing attacks. Enforce internet usage policies on endpoints with granular controls. Enable safe browsing with real-time ransomware detection. Discover, classify and secure all SaaS apps used throughout the organization. Decide what apps to sanction and un-sanction, protecting the entire SaaS attack surface. Prevent SaaS apps sprawl with intelligent discovery.
Track Sensitive Data Lineage and Secure Hybrid Work
Secure and track sensitive data lineage across endpoints, internet, email, and SaaS apps. Stop data theft before it happens via unauthorized sharing over the network, unauthorized user actions like copy-&-paste, airdrop, & usb transfer. Ensure compliance with automated reporting and audits. Track user behavior to identify and mitigate insider threats. With just a few clicks, enforce policies, manage privileges, and proactively resolve endpoint issues, ensuring seamless security and an optimized user experience.
Use-case of Kitecyber’s SSE Software
Secure Access to Cloud and Web Apps
Your users are everywhere. So are the apps they use. Kitecyber lets you control who accesses what, whether they’re on the network or not. Enforce Zero Trust access to web, SaaS, and cloud services without slowing users down. Block risky sites. Keep usage compliant.
Detect and Stop Insider Threats in Real Time
Threats don’t wait. Neither should your security. Kitecyber uses anti-phishing techniques, ransomware detection, and browser isolation to stop attacks before they spread. Our DLP tracks any copy-paste, data upload activity inside non-AI and Gen AI SaaS apps to catch hidden threats.
Connect and Protect Remote Workers
VPNs are slow. And risky. Kitecyber gives remote users fast, secure access to apps—without ever exposing your network. Our inside-out ZTNA keeps private apps hidden from the internet. No ACL headaches. No open ports. Just scalable, secure access with low latency, from anywhere in the world.
Find and Lock Down Sensitive Data
Data lives everywhere. Kitecyber finds it, classifies it, and keeps it safe. Our unified DLP works across endpoints, SaaS, and the web. Write policies once, apply them everywhere. Stay compliant with PCI, HIPAA, and GDPR without juggling tools. Simplify protection. Maximize control.
Elevate Your Remote/ BYOD Security Posture with Kitecyber SSE Today
Reach out today to schedule a consultation or request a demo, and see how our Security Service Edge – SSE Solutions can revolutionize your security strategy.
How it works
Frequently asked questions
- Zero Trust Network Access (ZTNA)
- Secure Web Gateway (SWG)
- Cloud Access Security Broker (CASB)