Table Of Content
Next Gen Secure web gateway “without the web gateway”
- May 27, 2024

Ready to take your security to next level and protect from cyber attacks?
Better security with No extra latency, No hair-pinning, No expensive cloud infrastructure
There are more than 65000 SaaS applications in the world and the number is growing rapidly. Every company uses anywhere from 50 to few hundreds SaaS applications for finance, accounting, software development, marketing, sales and much more.
As the applications are moving to SaaS, so is the data for most of the enterprises. Once the apps are not in the datacenter, it does not make sense to have the traffic go through the VPN connecting users to the datacenter. This movement saw the rise of secure web gateways a decade ago to tunnel all web and SaaS app traffic in order to provide visibility and control over their usage. Furthermore these gateways also provide controls for websites and categories of websites that are unsanctioned or are known to be malicious.
While companies need this protection and features offered by a secure web gateway, the architecture has several challenges and is inherently very inefficient. Here are some of the specific challenges:
Security Gaps
A simple audit will reveal that 50% of the internet traffic cannot be inspected and so unauthorized data movement cannot be controlled. This (50%) represents the attack surface for your modern and internet access. This leads to some serious compliance gap. Also it is easy to bypass data checks due to being an extra hop in the network as a user can simply encrypt a sensitive file and upload to some domain from the LOTS project (https://lots-project.com/)
Operational Complexity
Not every enterprise can afford a professional services team and months to install and fine tune a SASE or SWG solution. This comes from the fact that traffic needs to be tunneled to a cloud gateway, exceptions need to be made as all vendors do not allow their traffic to be tunneled. Complex policies need to be configured on the secure web gateway to handle SaaS Apps, users and websites.
Poor User experience and Performance
All Internet and SaaS app traffic goes through a cloud gateway, which adds extra latency. Some legacy SWGs were built precloud era and have limitations such as:
- Performance degradation issues as one tenant with heavy use of SWG resources would impact other tenants due to resource sharing in their cloud
- Multiple hops in the Internet introduces operational nightmare and complex troubleshooting when users complain
Not every enterprise can afford a professional services team and months to install and fine tune a SASE or SWG solution. This comes from the fact that traffic needs to be tunneled to a cloud gateway, exceptions need to be made as all vendors do not allow their traffic to be tunneled. Complex policies need to be configured on the secure web gateway to handle SaaS Apps, users and websites.
Cost
Finally this cloud infrastructure needs high network bandwidth and compute resources to process all the traffic. It also needs to be highly resilient and over-provisioned to handle spikes in usage or component failures. Ultimately customers have to pay its cost.
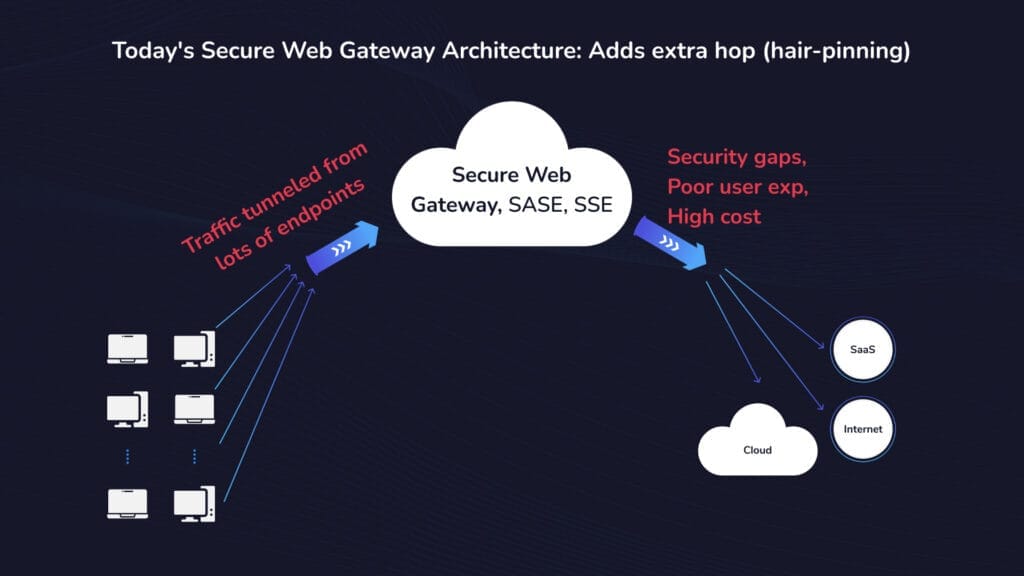
Figure 1: Existing architecture and its limitations
Figure 1 shows the current architecture, with its limitations and in-efficiencies. Here all the traffic is tunneled through a cloud gateway. We have security gaps, high latency and higher cost of cloud infrastructure that customers have to pay.
Can we do better than current solutions?
Do we really need these cloud gateways or can we implement these features at the endpoint?
Endpoints are getting more and more CPU and GPU cores. We have ever growing compute capacity to run AI copilots and personal assistants for editing documents, coding, designing and other jobs.
We could use a small fraction of that capacity to build an AI copilot to secure the endpoint and prevent the user from any harmful actions. The copilot can act as a security expert who can audit a user’s activity and warn them of anything suspicious or malicious.
Furthermore, the copilot can:
- Track SaaS app and Website access while applying any policies the enterprise selects for their employees
- Avoid phishing attacks
- Protect against data exfiltration
- Baseline normal user behavior and detect anomalies
And many more use cases….

Figure 2 shows the new architecture where we move the functionality to the endpoint and direct the traffic from the endpoint to the SaaS applications or Internet, providing your users with an improved experience, at lower cost and complexity.
So a secure web gateway can just be a feature that endpoints can handle and there is no need for this complex architecture anymore.
If you have to choose between the old style cloud gateways or doing a little bit of work at the endpoint and have a truly distributed cloud gateway protection, which one would you choose?
The Kitecyber team, consisting of veterans of the industry having closely observed the evolution of this technology believe that the next generation of security will not rely on these bulky and expensive cloud gateways but will be truly distributed. This new architecture also has the added benefit of being able to add device trust as another factor of authentication while accessing apps.
Visit our product website to learn more, schedule a demo, or sign up for a free trial: User Shield



