Table Of Content
7 GDPR Data Discovery Software 2026 (To Avoid Massive Fines)
-
December 9, 2025
-

And the surprising part? These penalties usually aren’t caused by advanced cyberattacks. Most companies simply don’t know where their data is.
You can’t protect something you can’t see. If you don’t know where sensitive customer information lives, staying compliant with GDPR becomes almost impossible.
That’s when data discovery for GDPR comes into picture. GDPR data discovery is the automated process of identifying, classifying, and mapping personal data across your entire IT infrastructure. This foundational step allows businesses to locate sensitive information across cloud, on-premise, and endpoint systems to ensure compliance. It also enables accurate responses to Data Subject Access Requests (DSARs).
Manual spreadsheets and annual audits fail. Data moves too fast. Employees share files on Slack. They upload customer lists to unauthorized AI tools. They store sensitive records on local drives.
You need a gdpr data discovery software to automate this workload. In this guide, you will discover why GDPR data discovery matters more than ever. You will learn what defines a reliable GDPR data discovery solution. You will also discover a list of top gdpr data discovery solutions available right now.
Why GDPR Data Discovery Is a Must
Many companies treat GDPR data discovery as a checkbox exercise. This is a mistake.
Knowing where your data lives is the foundation of all security. You cannot secure a server if you do not know it exists. You cannot protect a customer list if you do not know an employee saved it to their personal Dropbox.
Effective discovery improves your operational efficiency. It highlights redundant data you can delete, saving on storage costs. It identifies risky employee behaviors you can correct with training.
Here are 10 reasons why you need data discovery for GDPR compliance:
If you lack an accurate map of your data, you won’t be able to comply with GDPR requirements around data deletion, portability, or consent. Programs that relied solely on manual spreadsheets or simple BI tools fall short.
A robust data discovery tool doesn’t just scan; it classifies data, identifies PII (personally identifiable information) or other sensitive content, and enables you to manage data properly, whether that means deletion, masking or access controls.
How to Choose a GDPR Data Discovery Software
When evaluating a solution for GDPR data discovery or data discovery for GDPR, you should look for the following qualities:
- Ability to scan across a wide range of data sources: endpoints (devices), file servers, databases, cloud storage, SaaS apps.
- Classification of both structured and unstructured data (documents, emails, images, attachments, legacy data, etc.).
- Automated or configurable policies to classify sensitive data according to GDPR definitions (PII, personal identifiers, etc.).
- Continuous monitoring and data-movement tracking, not only data at rest but also file transfers, uploads, downloads, copy-paste, USB transfers, etc.
- Audit-ready reporting, logs, and compliance documentation to support regulatory audits.
- Ease of deployment, scalability, and support for mixed environments (cloud + on-prem + hybrid).
- Audit-ready reporting, logs, and compliance documentation to support regulatory audits.
7 Best GDPR Data Discovery Software of 2026 (To Avoid Massive Fines)
Here are the best tools to secure your data and keep the regulators away.

This architecture allows it to see everything. It detects sensitive data the moment a user creates it, downloads it, or tries to upload it to an unsanctioned app.
If an employee tries to paste customer emails into ChatGPT, Kitecyber detects the PII (Personally Identifiable Information) and tracks the action in real-time.
Key Features:
- Endpoint-Based Discovery: Discovers GDPR data on Windows, macOS, and Linux devices, even when they are off the corporate network.
- Real-Time Remediation: Blocks sensitive data exfiltration (like uploading a credit card list to a personal Gmail) instantly.
- Shadow IT Visibility: Automatically catalogs every SaaS app in use, helping you build your ROPA (Record of Processing Activities) effortlessly.
- AI-Powered Classification: Uses advanced AI to differentiate between a harmless spreadsheet and one containing sensitive GDPR data.
- Single Agent: Combines discovery, classification, DLP (Data Loss Prevention), and web filtering into one lightweight agent.
Verdict: Kitecyber is the most agile gdpr data discovery software for 2026. It covers the gaps that traditional network-based tools miss, specifically around remote work and GenAI usage.
2. OneTrust

Pros:
- Comprehensive: If you need to manage vendor risk, cookie consent, and DSAR (Data Subject Access Requests) in one place, OneTrust does it all.
- Market Standard: It is widely recognized by auditors and regulators.
- Huge Integration Library: Connects to almost any enterprise system you use.
Cons:
- Complexity: The platform is vast. Implementation often takes months and requires dedicated staff to manage.
- Cost: It is one of the most expensive options on the market.
- Overkill for Mid-Market: Smaller companies often pay for features they never use.
Verdict: If you have a large budget and a dedicated compliance team, OneTrust is a solid, safe choice. For anyone else, it might be too heavy.
3. BigID

It focuses heavily on the “identity” part of data. BigID can look at a piece of data and tell you exactly which customer it belongs to. This makes handling specific user deletion requests much easier.
Pros:
- Identity Intelligence: exceptional at correlating data fragments back to a single person.
- Wide Coverage: Scans mainframe data, cloud data, and on-prem databases effectively.
- Automation: heavily automates the data mapping process required for Article 30 reports.
Cons:
- Resource Intensive: Scanning petabytes of data requires significant compute power and budget.
- Learning Curve: The interface is technical and geared towards data engineers rather than general IT managers.
Verdict: BigID is a powerhouse for organizations that hoard massive amounts of customer data in databases.
4. Varonis
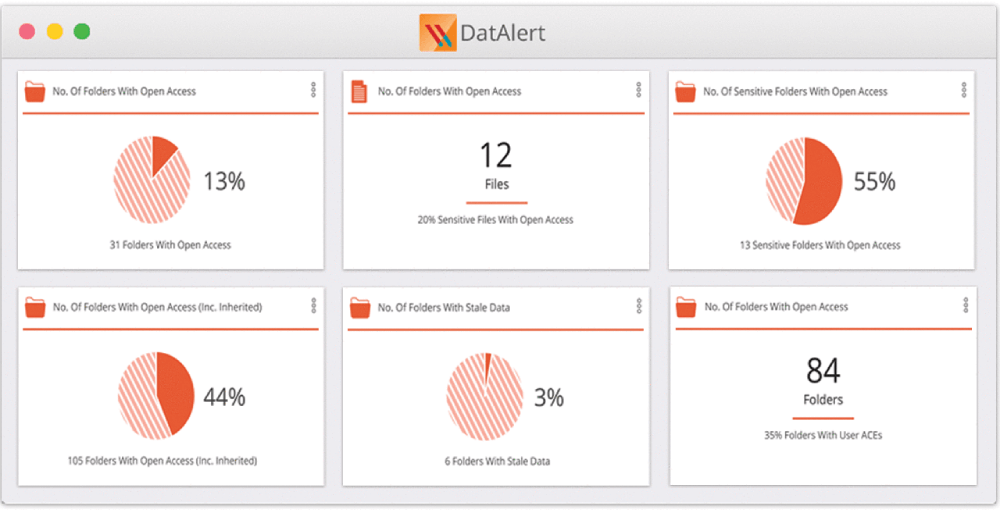
Its strength lies in analyzing permissions. Varonis tells you who has access to sensitive GDPR data and, more importantly, who should not have access. It monitors user behavior to spot anomalies, such as an employee suddenly downloading 500 sensitive files.
Pros:
- Permission Visualization: Shows you exactly which folders have "Everyone" access and helps you lock them down.
- Insider Threat Detection: Alerts you when a user behaves suspiciously with sensitive data.
- Automated Classification: Scans file servers and tags sensitive documents automatically.
Cons:
- On-Prem Heritage: While it has cloud versions, it feels most at home in traditional Windows Server environments.
- Price: specialized security focus comes with a premium price tag.
Verdict: If your main worry is employees stealing files or ransomware encrypting your file servers, Varonis is a strong data discovery for gdpr choice.
5. Osano

For discovery, Osano connects to your SaaS applications to identify where personal data lives. It focuses on the vendor side of things, helping you rate the privacy practices of the software you use.
Pros:
- User Experience: The interface is clean, modern, and intuitive.
- Speed: You can get up and running in days, not months.
- Vendor Risk: Excellent database of vendor privacy scores to help you choose safe tools.
Cons:
- Limited Depth: It does not go as deep into scanning endpoints or custom databases as Kitecyber or BigID.
- Focus: primarily a consent and vendor management tool, with discovery as a secondary feature.
Verdict: Osano is excellent for mid-sized tech companies that need to check the GDPR box quickly without hiring a massive compliance team.
6. Spirion

It claims an extremely low false-positive rate. This means when Spirion says a file contains a social security number or a credit card, it is usually right.
Pros:
- Accuracy: Strong pattern matching reduces the time teams spend reviewing false alarms.
- Remediation: Allows you to shred or redact files directly from the console.
- Legacy Support: Works well in older IT environments.
Cons:
- Endpoint Agents: agent management can be clunky compared to modern cloud-native solutions.
- UI: The interface feels dated compared to newer SaaS platforms.
Verdict: Spirion is a tactical tool. Use it if you have a specific need to clean up legacy file servers or desktops.
7. Transcend

When a user asks to delete their data, Transcend can go into your databases and actually delete it. This “Compliance as Code” approach appeals to CTOs and technical founders.
Pros:
- Full Automation: Reduces the manual work of fulfilling data requests to almost zero.
- Modern Stack: built for companies running on AWS, MongoDB, and modern SaaS tools.
- Data Mapping: Dynamically generates a live data map based on real-time API signals.
Cons:
- Technical Setup: Requires engineering resources to configure properly.
- Niche: Less focus on DLP or endpoint security compared to Kitecyber.
Verdict: If your product is built by engineers for engineers, Transcend will fit your workflow perfectly.
Conclusion
The days of “good enough” compliance are over. The regulators are active, and the fines are getting larger.
For most modern organizations, the challenge is no longer just databases: it is the endpoints, the SaaS apps, and the AI tools your employees use every day.
Kitecyber Data Shield stands out as the best all-around solution for this new reality. It combines visibility with active protection, ensuring that you do not just find your data, you keep it safe.
Review your current stack. If you rely on manual surveys or outdated network scanners, it is time to upgrade. Your data is moving. Your security should move with it.
FAQs on GDPR Data Discovery
It helps companies understand where personal data exists, who can access it, how it flows, and whether it complies with GDPR requirements.
- Limit access to that data,
- Fulfill data subject rights (DSARs),
- Detect and report breaches quickly,
- Maintain audit-ready records.
- Automated scanning across cloud + on-prem
- PII classification (names, emails, IDs, financial data, biometrics, etc.)
- Data mapping & lineage
- Risk scoring and policy alerts
- DSAR/Right-to-Erasure support
- Reporting for audits
- Integration with DLP, SIEM, IAM Tools that combine discovery + classification + action (e.g., DLP enforcement) offer the most value.
- Large data volumes
- Shadow IT
- SaaS sprawl
- Unstructured data
- Distributed cloud storage
- Databases (SQL/NoSQL)
- Cloud storage (AWS, Azure, GCP)
- SaaS apps (Google Workspace, Salesforce, HubSpot, Slack, etc.)
- Endpoints (Windows, macOS, Linux)
- File shares, NAS, email archives
- Collaboration apps (Teams, SharePoint, Notion, etc.)
- Quickly find all data related to a subject
- Export it for data access requests
- Delete or redact it for Right-to-Erasure
- Verify completion
It identifies sensitive data exposure, risky file movements, shadow copies, and unauthorized transfers, essential for GDPR’s Article 32 security requirements.
Kitecyber also integrates discovery with DLP enforcement, blocking violations instantly.
Kitecyber continuously scans endpoints (Windows, macOS, Linux) for:
- Personal data stored locally
- Unauthorized file transfers
- Copying to USB, cloud drives, or email
- Sensitive file creation or exfiltration attempts
Modern platforms (like BigID, OneTrust, Kitecyber) can also take action, such as:
- Blocking high-risk data transfers
- Alerting on policy violations
- Quarantining sensitive files
- Automating compliance workflows
- An organization didn’t know where personal data was stored
- Data was overexposed
- Access controls were weak
- Breach detection was delayed /ul> Discovery software ensures organizations have: A full inventory of PII
- Access restrictions
- Continuous monitoring
- Detectable audit trails This demonstrates proactive compliance, reducing legal and financial risk.