Table Of Content
Table Of Content
8 Best Data Security Solutions to Stop Breaches in 2026 (Expert Review)
-
December 26, 2025
-
Data security solutions are comprehensive technologies and strategies designed to protect digital information from unauthorized access, theft, and corruption throughout its lifecycle. Key components include encryption, identity and access management (IAM), and data loss prevention (DLP), which work together to safeguard sensitive assets across cloud and on-premise environments. In this post, you will learn the top 8 data security solutions for 2026. We focused on tools that offer actual visibility and control rather than just empty promises.
The Hidden Costs of Ignoring Data Security in 2025
Top Data Security Solutions & Tools Reviewed (for 2026)
Leading data security solution providers handle discovery, classification, and blocking, but vary in deployment ease and coverage. We reviewed dozens based on user feedback, features, and breach prevention stats. These eight stand out. Each handles data security and protection solutions with proven track records. We rank them by endpoint strength and ease of use.
1. Kitecyber Data Shield
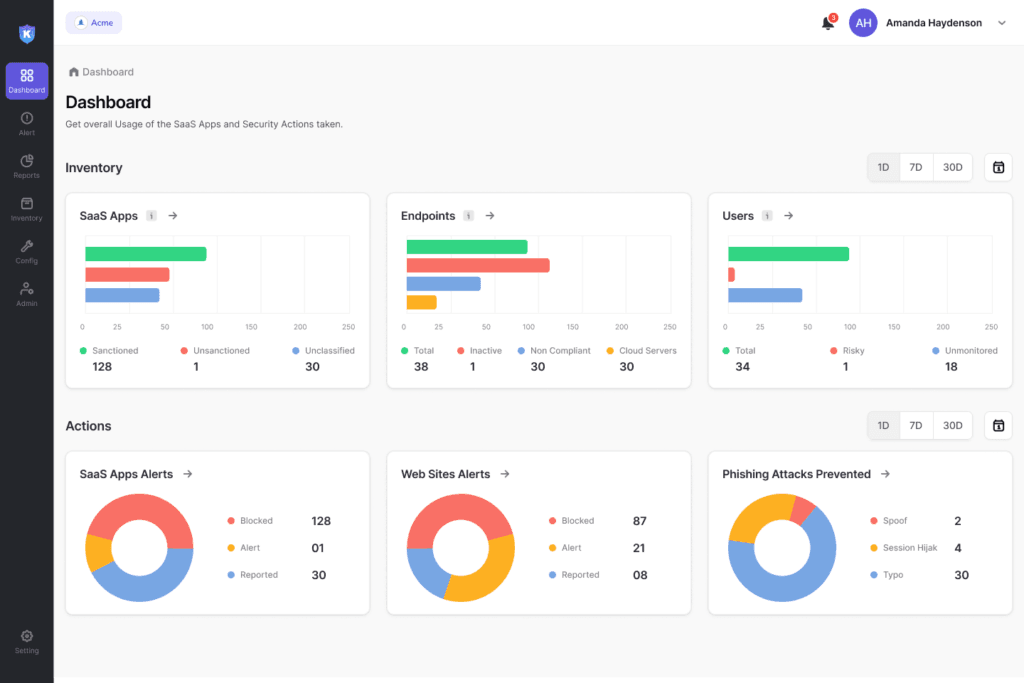
Best for: Unified Data Loss Prevention (DLP) and Insider Threat Protection.
Kitecyber Data Shield stands out as the most comprehensive modern data security solution. While legacy DLPs like Symantec or Forcepoint require months of configuration, Kitecyber offers a streamlined, effective approach that works almost immediately. It addresses the hardest part of data security: insider threats and Shadow AI.
Why it wins: Kitecyber unifies endpoint and network DLP. This means it tracks sensitive data regardless of where a user moves it. If an employee tries to copy a confidential client list to a USB drive, paste it into ChatGPT, or upload it to a personal Google Drive, Kitecyber detects it all.
- Unified Endpoint & Network DLP: Protects data across Windows, macOS, and Linux devices, as well as network traffic.
- Shadow AI Protection: Specifically monitors and blocks sensitive data from being pasted into GenAI tools like ChatGPT or Claude.
- Insider Threat Mitigation: Uses behavioral analysis to detect when an employee with valid access starts acting maliciously (e.g., mass downloading files before resigning).
- Agent-based & Lightweight: Unlike heavy legacy agents that slow down computers, Kitecyber runs efficiently in the background.
User Sentiment: Users on platforms like G2 and Reddit frequently praise the “set and forget” nature of the platform. IT managers highlight how quickly they could deploy Kitecyber DLP as compared to traditional tools. The ability to filter productive web usage while securing data is also a major plus.
Verdict: Despite being a newer entry in the segment, Kitecyber has been gaining popularity in terms of clientele across multiple countries. If you need a single, powerful solution to stop data leaks and control insider risk without stalling your team, Kitecyber Data Shield is the primary choice.
2. Velotix
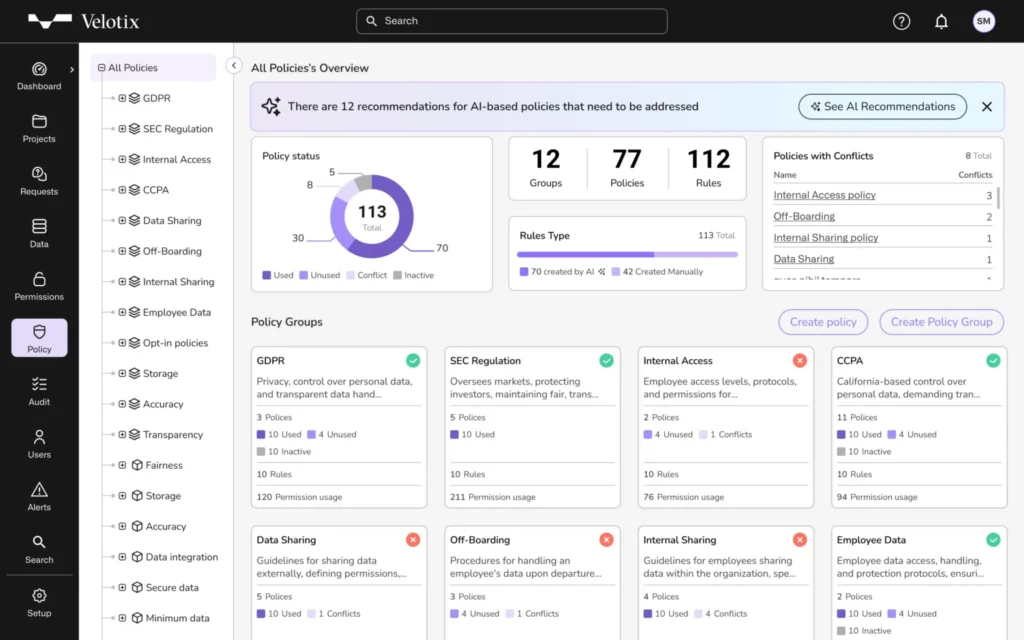
Best for: Democratizing Secure Data Access in Hybrid Environments
Velotix shines as a forward-thinking data security solution that balances accessibility with ironclad protection. Legacy access tools often create bottlenecks with rigid rules that frustrate teams and invite shadow IT. Velotix counters this by leveraging AI to grant precise permissions based on real-time context, ensuring your sensitive data flows to the right users without unnecessary exposure.
Why it is listed: Velotix triumphs through its policy-based access control that adapts to business needs, cutting manual reviews by 90% and minimizing insider risks from overprovisioned accounts.
- AI-Driven Policy Automation: Generates and enforces dynamic access rules using machine learning to match user intent with data sensitivity.
- Context-Aware Data Visibility: Monitors and controls structured/unstructured data flows in real time, preventing leaks via email, cloud shares, or apps.
- Insider Threat Analytics: Flags unusual access patterns, like bulk downloads or off-hours queries, with automated alerts and quarantines.
- Compliance Workflow Integration: Supports GDPR, HIPAA, and PCI DSS with prebuilt templates and one-click audit exports.
User Sentiment: G2 reviewers highlight its intuitive dashboard and rapid deployment, often calling it a “productivity booster” for IT teams. On Reddit’s r/cybersecurity, users commend its edge over traditional IAM tools for handling Shadow AI risks without workflow disruptions.
Verdict: Opt for Velotix when your organization demands quick, compliant data sharing across distributed teams—it’s the smart pick for scaling data security solutions without stifling innovation.
3. IBM Guardium
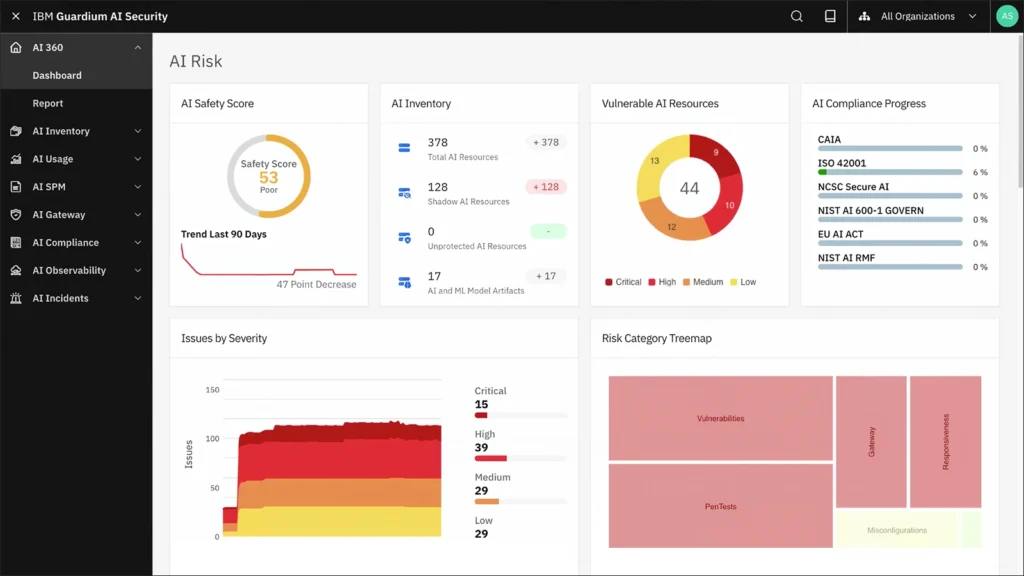
Best for: Database-Centric Threat Monitoring and Compliance Automation
IBM Guardium stands as a powerhouse data security solution tailored for structured data environments. While many tools skim the surface of database activity, Guardium dives deep with real-time oversight that catches anomalies before they escalate, making it indispensable for regulated industries facing constant audit pressures.
Why it wins: Guardium excels by providing unified visibility across hybrid databases, reducing breach detection times by 40% through AI-enhanced behavioral analysis. In 2025’s quantum-threat landscape, its encryption upgrades and policy mapping deliver proactive defense that legacy scanners simply can’t match, saving enterprises millions in fines.
- Real-Time Database Monitoring: Tracks queries, access, and changes across SQL, NoSQL, and mainframes with agentless connectors.
- AI-Powered Threat Prioritization: Analyzes user behavior to predict and block risks like SQL injection or privilege abuse.
- Automated Compliance Mapping: Aligns controls to standards like PCI DSS and GDPR, generating instant reports for auditors.
- Vulnerability Assessment: Scans for misconfigurations and excessive permissions, with remediation workflows.
User Sentiment: G2 feedback praises its robust analytics, though some note a learning curve; Capterra users rate it highly for finance teams. Reddit’s r/fintech threads favor it for “dated but bulletproof” reliability in high-stakes setups.
Verdict: Select IBM Guardium if your data lives primarily in databases and compliance drives your priorities—it’s the go-to for data protection solutions that turn audits into routine checks.
4. Microsoft Purview Information Protection
Best for: Seamless Integration in Microsoft Ecosystems
Microsoft Purview Information Protection emerges as the intuitive data security solution for Office 365 loyalists. Outdated standalone tools force clunky add-ons that fragment protection, but Purview embeds labeling and DLP directly into your daily apps, empowering users to safeguard data without extra steps.
Why it wins: Purview dominates by leveraging Microsoft’s vast ecosystem for automatic classification and enforcement, cutting oversharing incidents by 60% in AI-driven workflows. As 2025 brings tighter AI regs, its Copilot integrations provide unmatched visibility into prompt risks, outshining rivals in native, low-friction deployment.
- Sensitivity Labels and Auto-Classification: Applies encryption and access controls based on AI-detected content like PII or financials.
- Unified DLP Policies: Monitors endpoints, email, and Teams to block leaks with user notifications or quarantines.
- Insider Risk Analytics: Tracks file interactions to spot anomalies, integrating with Defender for holistic alerts.
- AI Workflow Protection: Restricts sensitive data in Copilot prompts and summaries for generative AI safety.
User Sentiment: G2 users love the “seamless” Microsoft tie-in but suggest redaction tweaks; Reddit’s r/microsoft365 calls it essential for hybrid work, with praise for reducing manual compliance chores.
Verdict: Go with Microsoft Purview if your stack revolves around Microsoft tools—it’s the effortless choice among data security and protection solutions for teams already in the ecosystem
5. CrowdStrike Falcon
Best for: Endpoint Protection and Ransomware Defense.
CrowdStrike is a giant in the data security solution providers space for a reason. Their Falcon platform is the gold standard for stopping active attacks, malware, and ransomware.
Why it works: CrowdStrike focuses on the “attack” aspect of data security. It stops hackers from breaching a device to steal data. Its EDR (Endpoint Detection and Response) capabilities allow security teams to isolate an infected laptop remotely before the infection spreads.
- Real-time Threat Detection: Uses AI to identify malicious processes instantly.
- Threat Intelligence: expansive database of known attacker tactics.
- Remote Response: Allows IT teams to investigate and remediate devices from anywhere.
6. Varonis
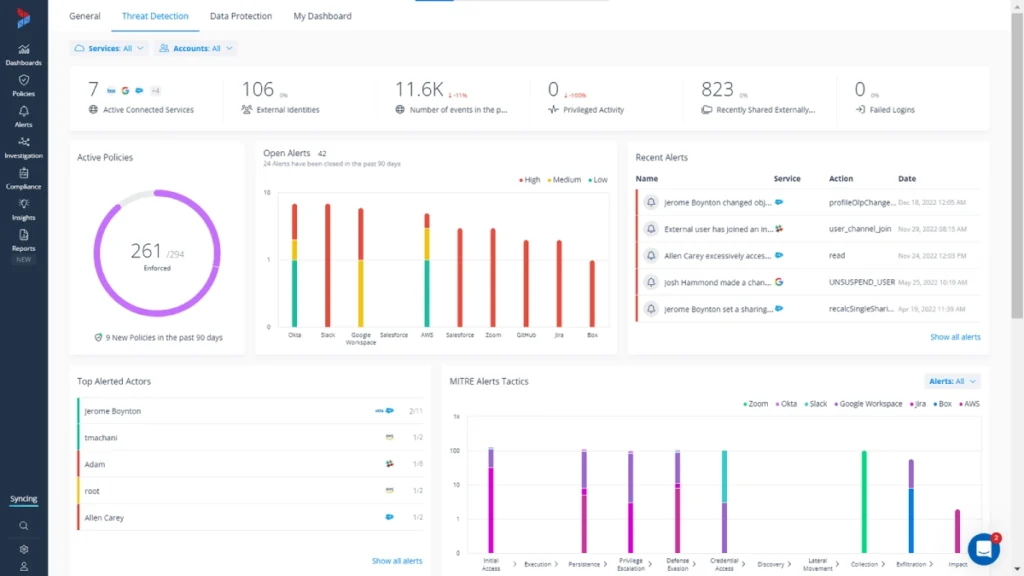
Best for: On-Premise and Hybrid Data Classification.
For organizations with significant on-premise infrastructure or hybrid environments, Varonis offers deep visibility into file servers and Active Directory.
Why it works: Varonis excels at answering the question: “Who has access to this folder?” It monitors file activity to spot unusual behavior, such as a user opening thousands of files in a short period.
- Permission Mapping: Visualizes who can access sensitive folders and helps reduce over-permissioning.
- Threat Detection: Uses machine learning to spot crypto-locker activity on file servers.
- Data Classification: Scans files to identify sensitive content inside them.
7. Forcepoint Data Loss Prevention
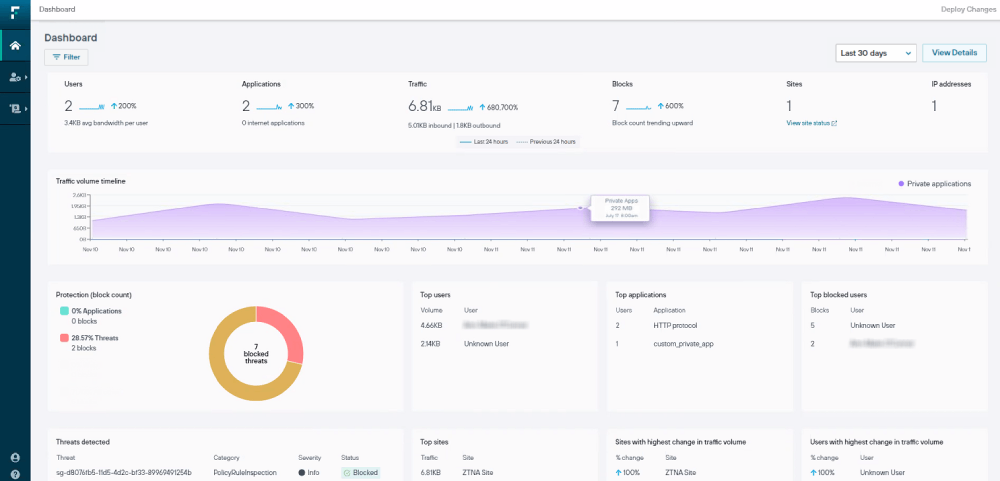
Best for: Inline Network Controls for Global Data Flows
Forcepoint Data Loss Prevention positions itself as a robust data security solution for traffic-heavy networks. Static firewalls let data slip through unchecked channels, yet Forcepoint inspects content on the fly, adapting to user risk levels to block threats without halting legitimate business.
Why it works: Forcepoint surges ahead with risk-adaptive protection that tunes policies via behavioral insights, reducing false positives by 50% over rule-based systems. For 2025’s borderless enterprises, its unified console across email, web, and endpoints ensures consistent enforcement, outperforming fragmented setups in speed and scale.
- Content-Aware Inspection: Analyzes email, web, and file transfers for sensitive patterns with optical character recognition.
- Behavioral Risk Scoring: Adjusts controls based on user history, blocking high-risk actions dynamically.
- Unified Policy Enforcement: Manages DLP across endpoints, networks, and clouds from one dashboard.
- Incident Forensics: Provides detailed traces for investigations, with automated quarantines.
User Sentiment: G2 reviewers laud its policy flexibility but mention dashboard clutter; Reddit’s r/cybersecurity values its global team support, calling it “enterprise-ready” despite setup time.
Verdict: Choose Forcepoint if cross-border data movement defines your operations—it’s the steadfast data security solution provider for networks under constant scrutiny.
8. Cyera
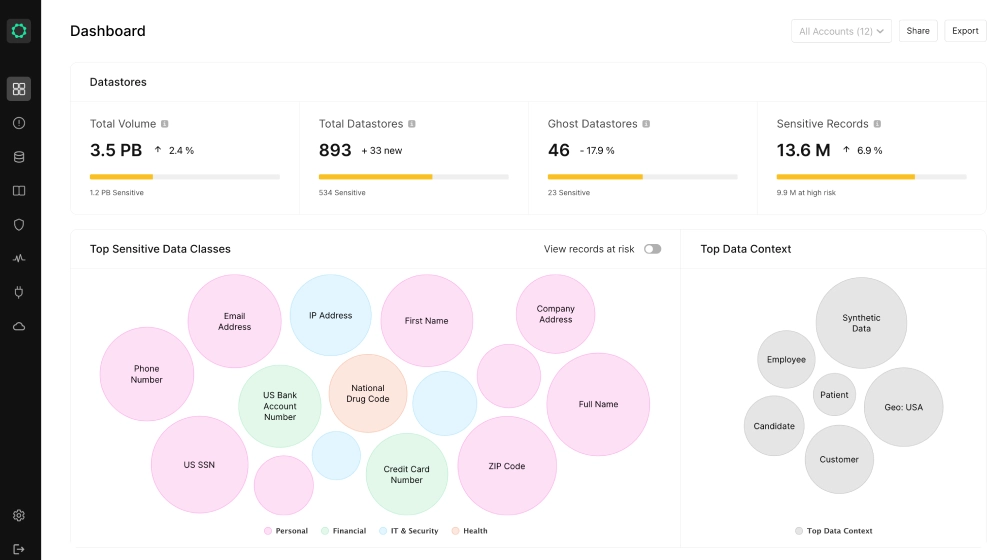
Best for: Cloud-Native Lineage Tracking and AI Risk Mapping
Cyera asserts dominance as an AI-native data security solution for dynamic cloud ecosystems. Traditional mappers lag behind data velocity, but Cyera’s platform traces flows in real time, revealing how sensitive info migrates across apps and agents to preempt breaches.
Why it wins: Cyera accelerates exposure analysis by 50% with semantic lineage, integrating human/AI access views that legacy tools ignore. In 2025’s agentic AI surge, its Access Trail innovation provides unmatched forensics, positioning it ahead for enterprises chasing secure innovation at scale.
- Continuous Data Mapping: Tracks lineage across SaaS, IaaS, and databases with 95% precision.
- AI-SPM for Shadow Tools: Inventories and governs AI models, flagging over-permissioned agents.
- Access Event Auditing: Logs every touchpoint with context on sensitivity and controls.
- Scores exposures by business impact for targeted remediation.
Secure Your Data Before the Next Breach Hits

Ajay Gulati
Ajay Gulati is a passionate entrepreneur focused on bringing innovative products to market that solve real-world problems with high impact. He is highly skilled in building and leading effective software development teams, driving success through strong leadership and technical expertise. With deep knowledge across multiple domains, including virtualization, networking, storage, cloud environments, and on-premises systems, he excels in product development and troubleshooting. His experience spans global development environments, working across multiple geographies. As the co-founder of Kitecyber, he is dedicated to advancing AI-driven security solutions.