Table Of Content
10+ Best Cyberhaven Alternatives & Competitors in 2026 (Ranked & Compared)
-
December 31, 2025
-
The market has shifted toward more integrated solutions that handle Windows, macOS, and Linux with equal precision. If your team includes developers or engineers, you know that Linux support is often an afterthought in the security world. This gap creates a massive blind spot in your data discovery and classification efforts. Finding an alternative to Cyberhaven means finding a tool that treats every operating system as a first-class citizen.
This article compares the top 10 alternatives to Cyberhaven DLP and ranks them in no particular order. Let’s get started!
What is Cyberhaven?
Cyberhaven is a data security platform that differentiates itself through its data lineage approach, tracking sensitive information back to its origins across endpoints, SaaS applications, AI tools, and cloud environments. The agent-based platform specializes in monitoring data movement, uploads, downloads, and endpoint activity, providing visibility into how sensitive data travels throughout your organization.
Core Features of Cyberhaven
- Data lineage tracking to map how data moves across the environment.
- Insider threat monitoring based on abnormal access or sharing behavior.
- SaaS app visibility with pre-built connectors.
- Risk scoring of sensitive events to prioritize response.
- Automated enforcement with alerts, blocks, and policy actions.
Strengths of Cyberhaven DLP
- Strong in insider risk detection due to lineage tracking.
- Provides detailed context for security investigations.
- Cloud-first design with lightweight deployment.
- Growing adoption in industries with intellectual property (IP) protection needs.
Limitations and Challenges
- Licensing starts near USD 42 per user monthly, which can climb fast in large rollouts.
- Linux support remains limited.
- The admin console requires a steep learning curve.
- Few native Zero Trust integrations.
- No built-in UEBA for cloud apps.
- Gaps in endpoint control compared to comprehensive DLP suites.
Additionally, Cyberhaven experienced a security incident in December 2024 when their Chrome extension was compromised, raising concerns about the security of the very tool meant to protect sensitive data.
Why Consider Cyberhaven Alternatives?
There is also the matter of the 2024 Cyberhaven security incident. A phishing attack compromised a Cyberhaven employee’s credentials, leading to a malicious version of their Chrome extension. This event highlighted a critical risk: the tools you trust with your data could become a vector for supply chain attacks. You might want a solution that minimizes these risks through a more robust architecture.
Configuration complexity is another common pain point. Many teams find that setting up overlapping policies in Cyberhaven is tedious. If your policy logic is non-intuitive, you might accidentally exclude critical data from protection. The best Cyberhaven alternatives should simplify the following pain points so you can focus on security rather than troubleshooting your security tool:
- 1. Cost and Scalability Concerns: Many enterprises report Cyberhaven becoming cost-prohibitive as user counts grow. Licensing and data processing expenses increase quickly in global deployments.
- 2. Integration Challenges: Cyberhaven’s ecosystem of integrations is still maturing. Enterprises with large SaaS portfolios may struggle with coverage compared to vendors with broader API libraries.
- 3. Industry-Specific Compliance Needs: Highly regulated sectors—such as healthcare, finance, and defense—often require out-of-the-box HIPAA, PCI DSS, or FedRAMP compliance controls that Cyberhaven may lack.
- 4. Lack of Advanced Analytics and AI Capabilities: Cyberhaven competitors now offer stronger UEBA (User and Entity Behavior Analytics), AI-driven anomaly detection, and automated remediation pipelines. Cyberhaven is currently less mature in these areas.
- 5. Customer Support and User Experience Factors: On G2 and Reddit forums, customers highlight delays in support responsiveness and challenges in onboarding policies. Ease of use lags behind vendors like Microsoft Purview or Kitecyber.
Key Evaluation Criteria for Alternatives to Cyberhaven
- Where did this file originate?
- Who has modified it?
- What applications has it passed through?
- Is this data a copy of a more sensitive original?
When evaluating cyberhaven competitors, you must ensure it maintains this “lineage” capability. Without it, you are stuck with old-school DLP solution that causes endless false positives. For example, a “confidential” tag on a public press release will trigger a false alert every time it is shared. A lineage-aware tool like Kitecyber knows that while the press release might contain sensitive keywords, its origin is the “public relations” folder, so it does not need to be blocked.
Audit and Compliance: Meeting Global Standards
Whether you are dealing with SOC 2, HIPAA, GDPR, or the new DPDP in India, you need a tool that simplifies the audit process. Compliance is no longer just about having a policy; it is about proving that the policy is enforced.
Centralized Logging
Your chosen Cyberhaven replacement should provide a centralized dashboard where you can see every policy violation and data movement across the company. This audit trail is essential during a compliance review. You should be able to show an auditor exactly how you protected PII over the last six months with just a few clicks.
Pre-built Templates
Top-tier tools like Kitecyber and Forcepoint offer pre-built policy templates for major regulations. Instead of writing rules from scratch, you can simply toggle on “GDPR Protection” or “HIPAA Compliance.” This significantly reduces the time it takes to get your organization ready for an audit.
What the Industry Isn't Talking About: The Security-UX Balance
The best alternative to Cyberhaven is one that is invisible to the user until they do something truly risky. It should feel like a “guardrail” rather than a “wall.” This is where lightweight, AI-driven tools have a massive advantage over legacy agents. By reducing false positives, you reduce the “security friction” that frustrates your team.
Making the Switch: How to Transition from Cyberhaven
- Define Your Scope: Identify which platforms (Windows, Mac, Linux) and which apps (Slack, Drive, Jira) are most critical.
- Run a Pilot: Deploy your chosen Cyberhaven replacement to a small, diverse group of users. Include at least one developer who uses Linux.
- Evaluate Performance: Monitor the impact on machine performance and network latency. Ask your users for feedback.
- Test the Policies: Trigger a few "safe" policy violations to see how the system responds and how clear the alerts are for your security team.
- Full Rollout: Once you are confident in the tool's efficacy, deploy it to the rest of the organization.
Top Cyberhaven Alternatives in 2025
1. Kitecyber Data Shield: The Best All-Channel Cyberhaven Alternative
Kitecyber Data Shield stands out as a premier Cyberhaven replacement for organizations that require deep visibility across all platforms. Unlike many competitors that focus strictly on cloud apps or Windows, Kitecyber provides comprehensive support for Windows, macOS, and Linux. This is a critical requirement for engineering-heavy organizations where sensitive intellectual property often resides on Linux workstations.
One major advantage of Kitecyber is its approach to different operating systems. Most DLP tools offer a “lite” version for Linux or macOS. Kitecyber ensures feature parity. You get the same level of data discovery and classification on a Linux server as you do on a Windows laptop. This consistency simplifies your audit and compliance reporting because you have a single source of truth for all your endpoints.
- Rapid Deployment and Ease of Use: Its lightweight design and self-service model enable deployment in minutes, a significant advantage for teams seeking fast time-to-value.
- Cost Efficiency: By eliminating the need for expensive cloud gateways and hardware appliances, Kitecyber can offer substantial cost savings, with some users reporting up to a 50% reduction in total cost of ownership (TCO).
- SMBs and mid-sized businesses seeking enterprise-grade security without high complexity.
- Organizations with hybrid or remote workforces needing protection for Windows, macOS, and Linux devices.
- Companies looking to consolidate vendors for IT management, security, and compliance.
2. Nightfall AI
- Rapid, organization-wide rollout with minimal configuration requirements.
- Monitors all major exfiltration paths including SaaS, generative AI apps, and endpoint devices.
- Flexible policies enforceable for specific user subsets, groups, or domains.
- Robust remediation options with manual or automated actions, including real-time blocking.
- Seamless integrations with Okta, Entra ID, Google Directory, MDM solutions, and custom APIs.
3. Microsoft Purview
- Strong AI classification and labeling engine optimized for Microsoft data sources.
- Decent workflow engine to enforce sharing policy controls across Microsoft 365 applications.
- Integration with Azure services provides extensive data governance capabilities.
- Policy templates help address common compliance requirements.
- Centralized management console for unified policy administration.
4. Forcepoint DLP
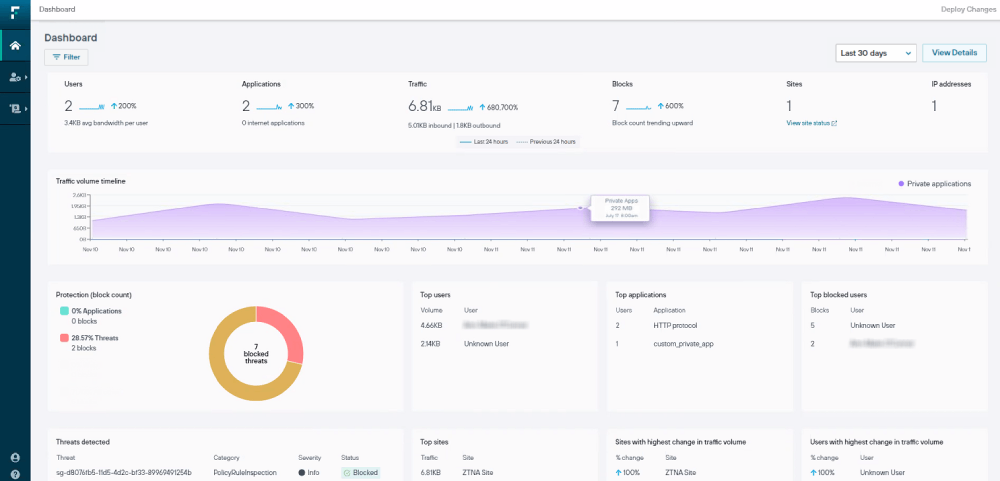
Overview: Forcepoint DLP, part of the Forcepoint One platform, offers broad coverage across endpoints, networks, cloud services, and web traffic. The solution emphasizes risk-adaptive protection that adjusts controls based on user behavior analytics.
- Advanced content inspection and customizable classifier engine for various industries.
- User risk scoring feature for monitoring and mitigating risky user behavior.
- Mobile DLP policy workflows controlling data transmission to mobile devices.
- OCR capabilities for detecting sensitive data within images.
- Pre-defined policy templates with customization options.
5. Symantec DLP (Broadcom)
- Wide coverage spanning multiple platforms and channels.
- Unified administration console simplifying policy management.
- Integration with other Broadcom security solutions for a cohesive ecosystem.
- Scalability designed for large, global enterprise deployments.
- Compliance templates for GDPR, HIPAA, and PCI DSS.
6. Zscaler DLP
Overview: Zscaler DLP integrates data protection within the Zero Trust Exchange platform, providing security service edge (SSE) capabilities alongside traditional DLP functionality.
- Strong inline DLP inspecting traffic across cloud, SaaS, and endpoint environments.
- SSL/TLS decryption capabilities for comprehensive traffic visibility.
- Cloud-native architecture aligning with modern infrastructure trends.
- Integration with Zscaler Internet Access for unified policy enforcement.
7. Proofpoint ObserveIT
- Real-time behavioral analytics for immediate risk identification.
- Detailed forensic data gathering for investigation context.
- Integration with other Proofpoint solutions and third-party tools.
- Session recording and user activity monitoring capabilities.
8. Trellix (McAfee Enterprise + FireEye)
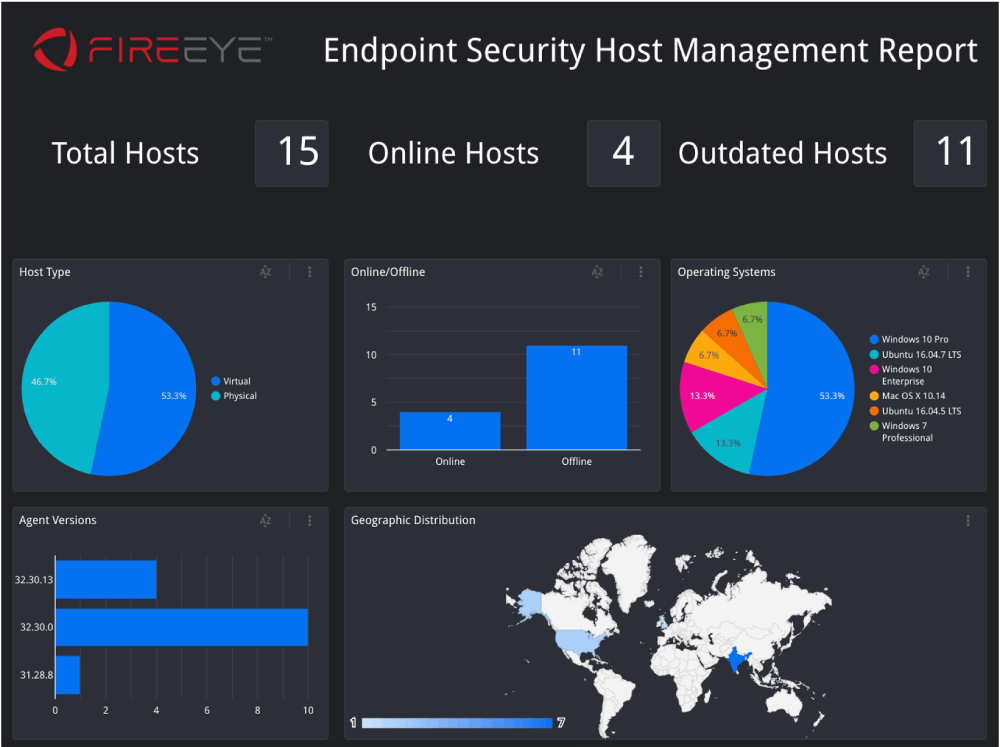
Overview: Trellix represents the merged capabilities of McAfee Enterprise and FireEye, offering a comprehensive DLP solution spanning endpoints, networks, cloud storage, and email.
- Common policies enforceable across all channels for unified protection.
- Real-time scanning capabilities with forensic analysis support.
- Data discovery across endpoints, networks, cloud storage, and email systems.
9. Digital Guardian
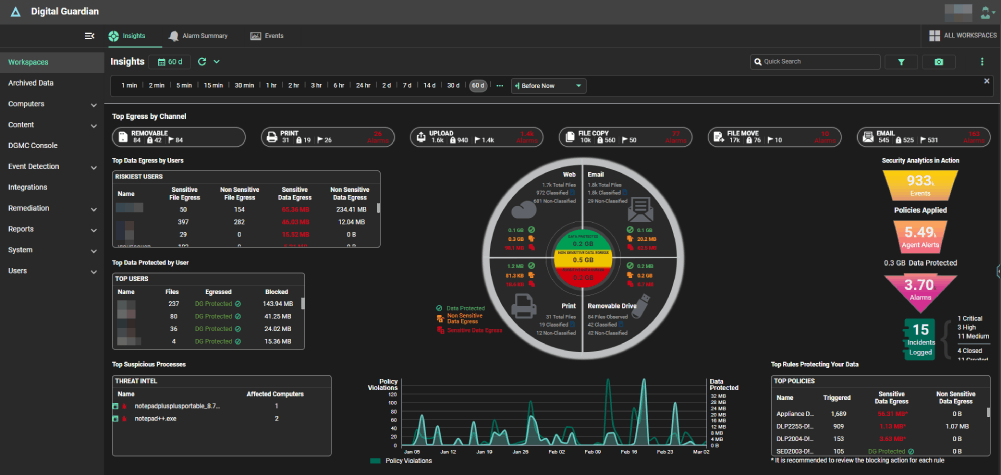
Overview: Now part of Fortra’s cybersecurity portfolio, Digital Guardian emphasizes data discovery, classification, and protection across endpoints and networks.
- Data discovery and classification supporting GDPR, CCPA, and other regulations.
- Flexible deployment options including cloud and on-premises implementations.
- Unique file tagging approach for persistent data protection.
10. Code42 Incydr
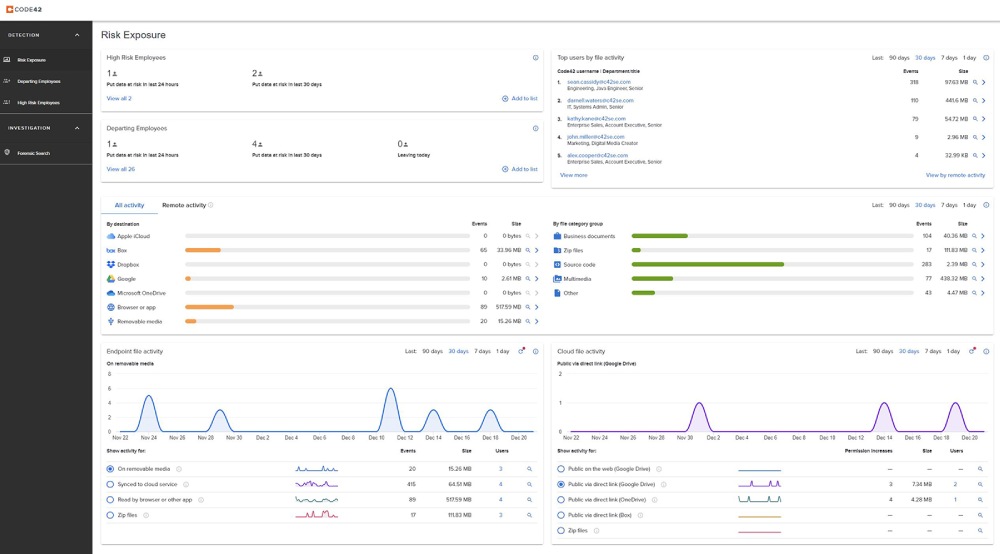
- Strong endpoint monitoring with real-time tracking of file movements.
- Insider threat focus targeting risky user behavior.
- Cloud integration for Google Workspace, M365, Box, Dropbox, and Salesforce.
11. Endpoint Protector by CoSoSys
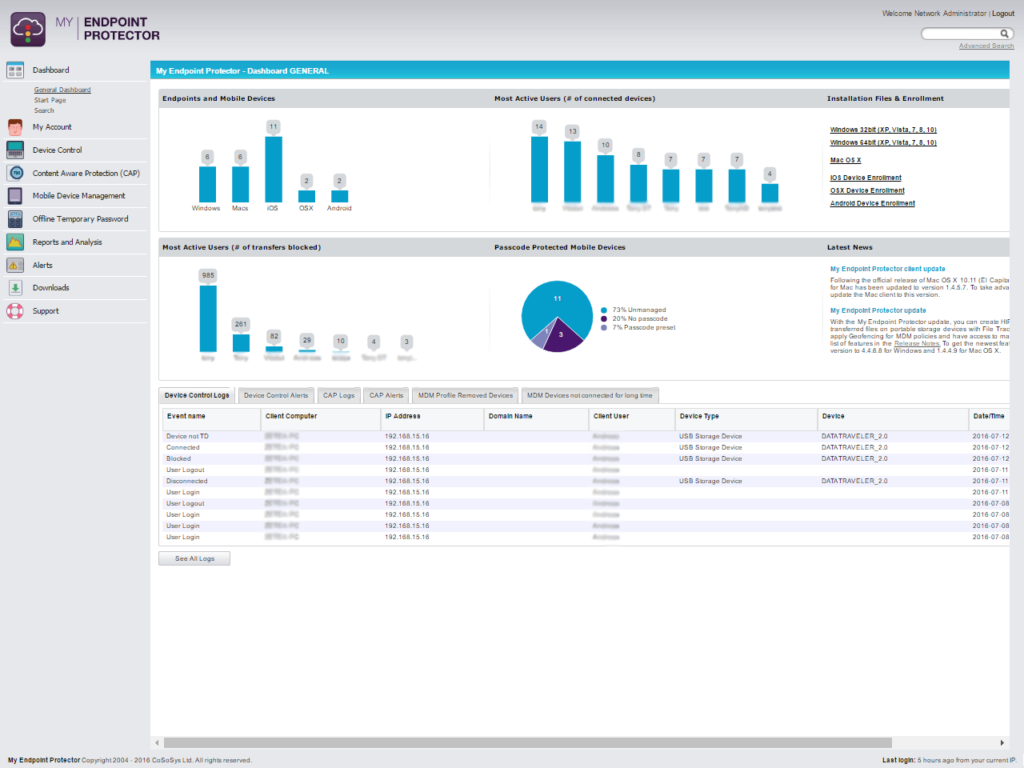
Overview: Endpoint Protector provides content-aware DLP protection with additional device control and mobile device management (MDM) capabilities.
- Content-aware protection examining data context and content.
- Device control capabilities for managing USB and peripheral data transfers.
- Integration with Active Directory for streamlined user management.
Comparative Matrix to Evaluate Cyberhaven Alternatives Head-to-Head
|
Feature/Capability |
Kitecyber Data Shield |
Nightfall AI |
Microsoft Purview |
Forcepoint DLP |
Symantec (Broadcom) |
Zscaler DLP |
Proofpoint ObserveIT |
Trellix DLP |
Digital Guardian |
Code42 Incydr |
Endpoint Protector |
|
G2 Ease of Use |
8.7/10 |
9.1/10 |
8.4/10 |
8.9/10 |
7.2/10 |
8.5/10 |
8.2/10 |
8.5/10 |
7.5/10 |
8.8/10 |
8.6/10 |
|
Insider Threats |
Comprehensive ★★★★★ (Behavioral/Offline) |
Good ★★★★☆ (SaaS/API focus) |
Good ★★★★☆ (Native M365) |
Good ★★★★☆ (Behavioral) |
Good ★★★★☆ (Mature rules) |
Good ★★★★☆ (Inline/Web) |
Comprehensive ★★★★★ (Behavioral) |
Good ★★★★☆ (Risk scoring) |
Comprehensive ★★★★★ (Forensics) |
Good ★★★★☆ (Exfiltration) |
Good ★★★★☆ (Device focus) |
|
Ransomware Protection |
Comprehensive ★★★★★ (C2/IP blocking) |
Good ★★★★☆ (API-level) |
Good ★★★★☆ (Cloud-native) |
Good ★★★★☆ (Sandboxing) |
Good ★★★★☆ (Intrusion) |
Good ★★★★☆ (Web isolation) |
Good ★★★★☆ (Intelligence) |
Good ★★★★☆ (Multi-layer) |
Good ★★★★☆ (Kernel-level) |
Medium ★★★☆☆ (File tracking) |
Good ★★★★☆ (USB-level) |
|
False Positives |
Low ★★★★★ (AI-driven) |
Low ★★★★★ (Context-aware) |
Medium ★★★☆☆ (Template-heavy) |
High ★★☆☆☆ (Signature-based) |
High ★★☆☆☆ (Legacy rules) |
High ★★☆☆☆ (Inline noise) |
Medium ★★★☆☆ (Heuristic) |
High ★★☆☆☆ (Frequent tuning) |
High ★★☆☆☆ (High noise) |
Low ★★★★★ (Movement focus) |
Medium ★★★☆☆ (Content-aware) |
|
User Experience |
Excellent ★★★★★ (< 2% CPU) |
Excellent ★★★★★ (Agentless) |
Good ★★★★☆ (Native) |
Poor ★★☆☆☆ (CPU spikes) |
Poor ★★☆☆☆ (Very heavy) |
Good ★★★★☆ (Latency risk) |
Good ★★★★☆ (Sensor-based) |
Good ★★★★☆ (Light post-tuning) |
Poor ★★☆☆☆ (Kernel impact) |
Excellent ★★★★★ (Transparent) |
Good ★★★★☆ (Minimal impact) |
|
Deployment |
Endpoint ★★★★★ (Pure Cloud) |
SaaS API ★★★★★ (No Agent) |
Native ★★★★☆ (Hybrid) |
Appliance ★★☆☆☆ (Complex) |
Appliance ★★☆☆☆ (Legacy) |
SASE ★★★★☆ (Cloud Proxy) |
Hybrid ★★★☆☆ (Sensors) |
Appliance ★★☆☆☆ (Central) |
Managed ★★★★☆ (Cloud/SaaS) |
Endpoint ★★★★★ (Cloud Agent) |
Hybrid ★★★★☆ (Flexible) |
|
Total Cost (TCO) |
Low ★★★★★ (~50% Savings) |
Low ★★★★★ (No hardware) |
Low ★★★★☆ (If E5) |
High ★☆☆☆☆ ($55+/user) |
High ★☆☆☆☆ (Legacy pricing) |
High ★☆☆☆☆ (Bundle-only) |
Medium ★★★☆☆ ($40-90) |
High ★☆☆☆☆ ($60+) |
High ★☆☆☆☆ ($300k+ start) |
Medium ★★★☆☆ ($40-80) |
Low ★★★★★ (Value-focused) |
|
Linux Support |
Full Parity ★★★★★ |
None ☆☆☆☆☆ |
Limited ★★☆☆☆ |
Limited ★★☆☆☆ |
Good ★★★★☆ |
None ☆☆☆☆☆ |
Limited ★★☆☆☆ |
Limited ★★☆☆☆ |
Good ★★★★☆ |
None ☆☆☆☆☆ |
Good ★★★★☆ |
|
Lineage/Discovery |
Comprehensive ★★★★★ (Audit trails) |
Good ★★★★☆ (SaaS discovery) |
Good ★★★★☆ (M365 data) |
Comprehensive ★★★★★ (Lifecycle) |
Comprehensive ★★★★★ (Enterprise) |
Good ★★★★☆ (Inline only) |
Comprehensive ★★★★★ (User story) |
Limited ★★☆☆☆ (Logs only) |
Comprehensive ★★★★★ (Discovery) |
Limited ★★☆☆☆ (No Content) |
Good ★★★★☆ (Scan-based) |
|
Location Security |
Comprehensive ★★★★★ (Geofencing) |
Poor ★★☆☆☆ (Cloud only) |
Medium ★★★☆☆ (Policy-based) |
Poor ★★☆☆☆ (Minimal) |
Medium ★★★☆☆ (Peripheral) |
Good ★★★★☆ (Geo-IP) |
Poor ★★☆☆☆ (User-focus) |
Good ★★★★☆ (Device rules) |
Good ★★★★☆ (Peripheral) |
Poor ★★☆☆☆ (Minimal) |
Good ★★★★☆ (Device ID) |
Conclusion
The optimal choice balances comprehensive data protection with practical operational considerations. By following the structured evaluation approach outlined in this guide, security leaders can make informed decisions that align with their organization’s unique requirements.