Table Of Content
12 Top Insider Threat Management Solutions & Tools (2025 Edition)
-
August 21, 2025
-
Ever wonder why sensitive data leaks still happen, even with firewalls, EDR, and all the security tools? Here’s why: most companies ignore the real threat, your insiders. Employees, contractors, even trusted admins, pose the single biggest risk to your confidential data. And the 2025 Ponemon report proves it: the average annual cost of insider threats has risen to $17.4M.
So, how do you stop your next headline-making breach? With a next-gen insider threat detection platform built for modern B2B needs.
This guide ranks the best insider threat management solutions for 2025, based on features, real user reviews, G2 ratings, pricing, and proven breach prevention.
Feeling lazy to scroll through? Click here to directly navigate to a Insider Threat Management Software:
- Kitecyber:
Best for AI-powered, Zero Trust–aligned insider risk management across devices, SaaS, Internet. - Cyberhaven: Best for real-time data lineage tracking to stop insider data theft at the source.
- UpGuard: Best for SMBs and mid-sized teams needing lightweight, compliance-driven insider risk protection.
- TeraMind: Best for employee activity monitoring & insider misuse detection across desktops and remote work.
- Varonis Data Security: Best for enterprises needing deep file system monitoring and access control insights.
- Microsoft Purview Insider Risk Management: Best for Microsoft 365-heavy organizations seeking native insider risk workflows.
- DTEX Systems:
Best for scalable workforce visibility with user behavior analytics and insider intent detection. - Everfox (formerly Forcepoint Insider Threat):
Best for government, defense, and regulated industries with stringent insider monitoring needs. - Syteca: Best for niche insider detection deployments where customizable policies and flexibility are required.
- ManageEngine Firewall Analyzer:
Best for network-level insider misuse detection via firewall traffic visibility. - Exabeam Fusion:
Best for SOC teams using UEBA + SIEM to detect insider anomalies and credential misuse. - Proofpoint Insider Threat Management :
Best for SaaS and endpoint insider misuse detection with strong DLP integration.
Why Use Insider Threat Management Solutions?
Insider threats are sneaky. They come from within: employees, contractors, or partners with access to your systems. These threats can lead to financial losses, regulatory fines, and damaged reputations. Insider threat management software solutions helps small businesses by:
- Saving Money: Prevent breaches that cost millions.
- Ensuring Compliance: Meet GDPR, HIPAA, and PCI-DSS standards.
- Maintaining Operations: Avoid disruptions from insider incidents.
- Protecting Reputation: Keep customer trust intact.
- Spotting Threats Early: Catch issues before they escalate.
- Analyzing Behavior: Detects unusual user activity.
- Preventing Data Loss: Stop sensitive data from leaving your network.
Common Reasons for Using Insider Risk Management Solutions
|
Reason |
Description |
|
Ransomware & Data Exfiltration |
Malicious insiders can plant ransomware or steal data undetected |
|
Risk from Trusted Users |
Credential theft, disgruntled employees, and third-party vendors exploit access rights |
|
Cost of Insider Incidents |
Average annual cost hits $17.4M (Ponemon 2025), often exceeding external attacks |
|
Shadow SaaS and BYOD |
Sensitive data leaks through unmanaged apps and devices |
|
Regulatory Compliance Mandates |
GDPR, HIPAA, SOC2, PCI, SEC demand continuous monitoring for insider abuse |
|
Remote/Hybrid Workforce |
Activity is dispersed and traditional network security doesn’t cover endpoints effectively |
|
Excessive Privilege/Credential Abuse |
Users retaining access after job changes or compromised credentials exploited |
|
Alert & Investigation Overload |
Old SIEM/XDR tools flood security teams with noise, missing true insider threats |
12 Top Insider Threat Management Solutions for 2025
Here’s our curated list of the top 12 B2B insider threat software solutions, ranked for small business owners based on effectiveness, affordability, and ease of use.
1. Kitecyber (The #1 Insider Threat Management Tool)
Overview:
Kitecyber is one of the best data context-aware Insider Risk Management Solution that unifies endpoint, network, SaaS, and cloud DLP with a universal AI powered endpoint agent. It protects sensitive data across devices, email, browsers, SaaS, and shadow IT. It stops ransomware, insider threats, and data leaks. Compliance with GDPR, HIPAA, PCI‑DSS, ISO 27001, and more is enforced automatically. Rapid controls and continuous monitoring keep data secure across hybrid/ BYOD and Gen AI powered work environments.
Key Features:
- Endpoint DLP – Sensitive data discovery, tracking, and protection across USBs, drives, cloud, and file sharing.
- Network DLP – Real-time monitoring for SaaS and cloud apps, Gen AI risk controls, end-to-end encryption, and certificate-pinned app visibility.
- Advanced Threat Protection – AI behavioral detection, offline security, insider detection, and Zero Trust verification.
- Data Lineage Tracking - Tracks the movement of sensitive data across endpoints, SaaS apps, and networks, enabling early detection of potential insider theft attempts.
- Threat Response - Upon detecting suspicious activities, such as clipboard misuse or attempts to move sensitive data, admin can use Kitecyber to block access to internal or SaaS apps, quarantine devices, or initiate remote lock/wipe to mitigate insider threats instantly.
- Compliance-Aligned Detection - Kitecyber supports compliance with standards like GDPR, HIPAA, SOC2, and ISO27001 by monitoring and flagging insider activities that violate regulatory policies, ensuring organizations can detect and document potential theft for audits.
- User Entity Behavior Analytics (UEBA) - Kitecyber UEBA detects suspicious activities such as unauthorized data copying, pasting, or transfers by analyzing user actions and establishing trust scores to identify risky insider behaviors.
Here’s what Drew Danner, Managing Director at BD Emerson says about our solution:
"Kitecyber has been amazing for our SMB customers, who can now enjoy enterprise grade security with a simple and cost effective solution."
"Instead of dealing with multiple complex solutions, with Kitecyber they can get advanced security with ease using a single AI copilot”

Kitecyber's Best Insider Threat Management Software Features
|
Feature |
Importance |
|
User Entity Behavioral Analysis(UEBA) |
Establishes baselines of normal activity to detect anomalies, enabling proactive tracking of insider threats, supporting forensic analysis, and reducing the risk of data breaches by identifying malicious or careless behaviors early. |
|
Next-Gen Data Loss Prevention (DLP) |
Tracks sensitive data lineage across endpoints, networks, email, and SaaS apps, preventing exfiltration through monitoring actions like copy-paste, USB transfers, and uploads, which minimizes data theft risks and ensures regulatory compliance. |
|
Anomalous User Behavior Detection |
Identifies unauthorized data access, sharing, or movement with full context, allowing timely mitigation of insider risks and protecting against both intentional and accidental threats. |
|
Data Exfiltration Prevention |
Detects and blocks unauthorized data movements, including encrypted traffic, safeguarding compliance and preventing business risks from insider-driven leaks. |
|
Cloud API and SaaS Risk Management |
Discovers and controls external integrations and apps to secure connections, reducing vulnerabilities to supply chain and insider attacks while preventing sprawl and unauthorized data sharing. |
|
Endpoint Management with Device Trust |
Enables remote lock and wipe for lost devices, tracks events and health metrics, mitigating insider access to compromised endpoints and preventing data misuse in remote or BYOD scenarios. |
Protect Your Data from Insider Threats?
Try Kitecyber – one of the best AI-powered Insider Threat Management solutions for comprehensive data security.
- Real-Time Behavior Analytics: Detects anomalies with AI-driven user behavior monitoring to catch threats early.
- Advanced Data Loss Prevention: Track and block unauthorized data transfers across endpoints, SaaS, and networks.
- Granular Policy Enforcement: Set precise access controls to prevent data exfiltration and ensure compliance.
- Automated Threat Response: Instantly block risky actions like unauthorized sharing with remote lock and wipe.
- Trusted by Global Enterprises: Proven protection for organizations across industries in the United States and India.
- 24/7 Expert Support: Get dedicated assistance to secure your environment anytime.
2. Cyberhaven
Overview: Cyberhaven is a data-centric insider theft management solution that fuses DLP, Insider Risk Management, and DDR (Data Detection & Response). It follows data everywhere (endpoints, SaaS, GenAI tools) using data lineage to understand what the data is and how it’s moving. That lineage context sharply reduces false positives while enabling real-time controls to stop exfiltration. It emphasizes automated coaching/just-in-time prompts, tiered response, and deep investigations (screen/file capture). Recent materials highlight major reductions in false positives and faster investigations.
Key Features:
- High-accuracy detection with real-time user coaching.
- Tracks data lineage to prevent exfiltration.
- AI-powered automation for streamlined controls.
Pros:
- Reduces false positives by up to 90%.
- Fast incident resolution (up to 2x faster).
Cons:
- May be complex for very small teams.
- Limited SaaS coverage - Data Security gaps
3. UpGuard
Overview: UpGuard solution provides a comprehensive platform for managing attack surfaces and third-party risks, including insider threat management.
Key Features:
- Unified cyber threat lifecycle management.
- External attack surface intelligence.
- Real-time scanning and alerts.
Pros:
- 91% of G2 reviewers praise its third-party risk management.
- Easy to use (94% satisfaction rate).
Cons:
- False positives & weak reporting.
- Expensive
4. Teramind
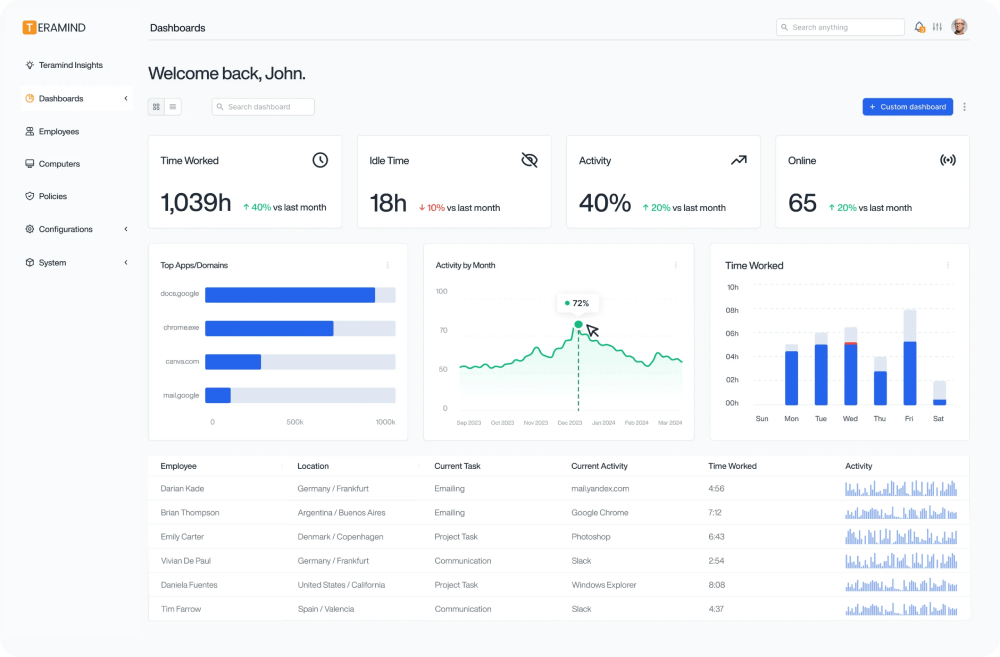
Key Features:
- Detailed behavioral analytics and real-time alerts.
- Comprehensive endpoint and cloud monitoring.
- Privacy-friendly deployment options.
Pros:
- Affordable for small businesses.
- Detailed reporting for compliance.
Cons:
- Privacy concerns from intrusive monitoring
- Complex setup and management overhead.
5. Varonis Data Security Platform
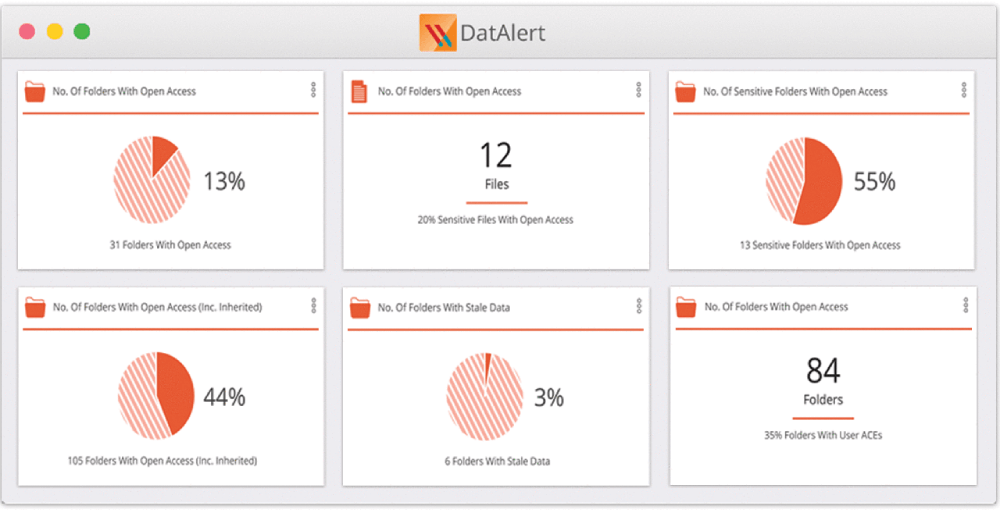
Key Features:
- Automated data discovery and classification.
- Real-time alerts for suspicious activity.
- 24/7 Managed Data Detection and Response (MDDR).
Pros:
- Strong automation for data protection.
- Proactive threat detection.
Cons:
- Visibility only and cannot block upload/download or copy paste of sensitive data
- Blindspots on endpoint like USB, Network drive and native file storage apps
- Complex to setup and high management overhead
- Expensive
6. Microsoft Purview Insider Risk Management
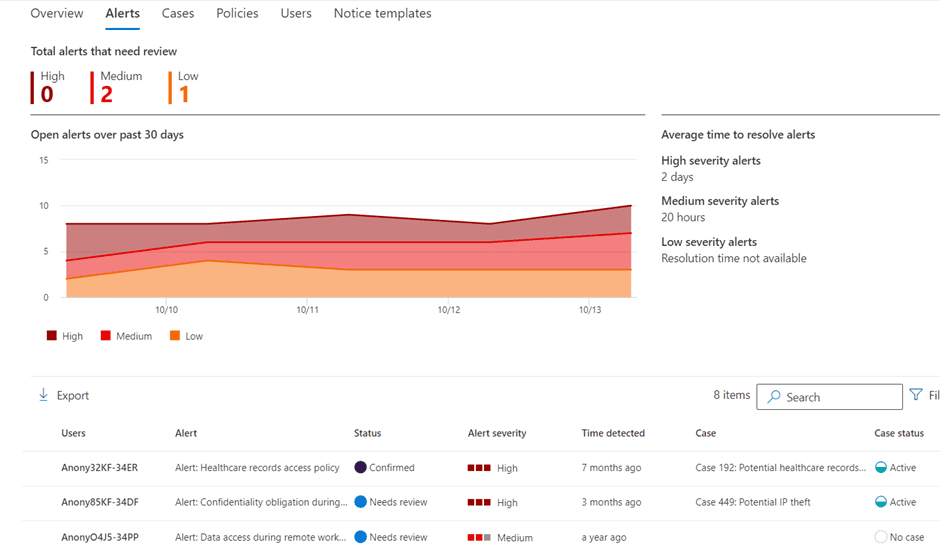
Key Features:
- Correlates signals for IP theft and data leakage.
- Privacy-focused with pseudonymized users.
- Policy templates for common scenarios.
Pros:
- Seamless Microsoft 365 integration.
- Strong compliance features.
Cons:
- Limited features and works within Microsoft productivity stack.
- Complex to setup and high management overhead
7. DTEX Systems
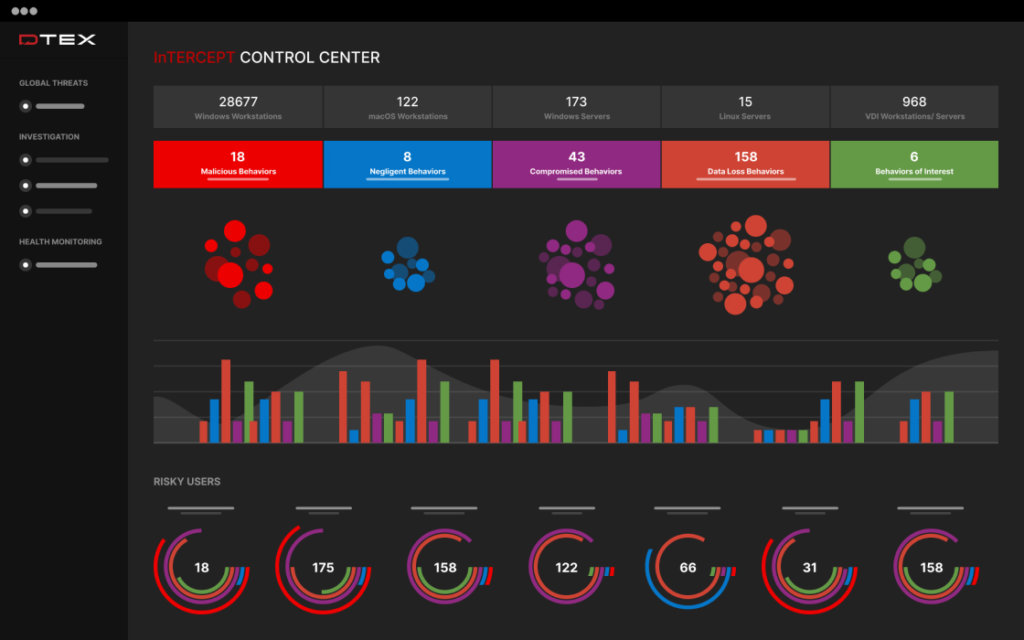
Key Features:
- Real-time detection and response.
- Scales to over 500,000 endpoints.
- AI-guided investigations.
Pros:
- Scalable for growing businesses.
- Rich endpoint telemetry.
Cons:
- Weak enforcement capabilities—it monitors but doesn't intervene directly..
8. Everfox
Key Features:
- Pays for itself in under 6 months (per Forrester).
- Always-on user activity monitoring (UAM/UEBA).
- Linguistic analysis for behavioral insights.
Pros:
- Strong predictive capabilities.
- High-assurance security.
Cons:
- May be overkill for small businesses.
9. Syteca
Key Features:
- Privileged access management with secure vaults.
- Real-time user activity monitoring with customizable alerts.
- 30+ report types for compliance.
Pros:
- Comprehensive and user-friendly.
- Strong real-time monitoring.
Cons:
- Limited pricing transparency.
10. ManageEngine Firewall Analyzer
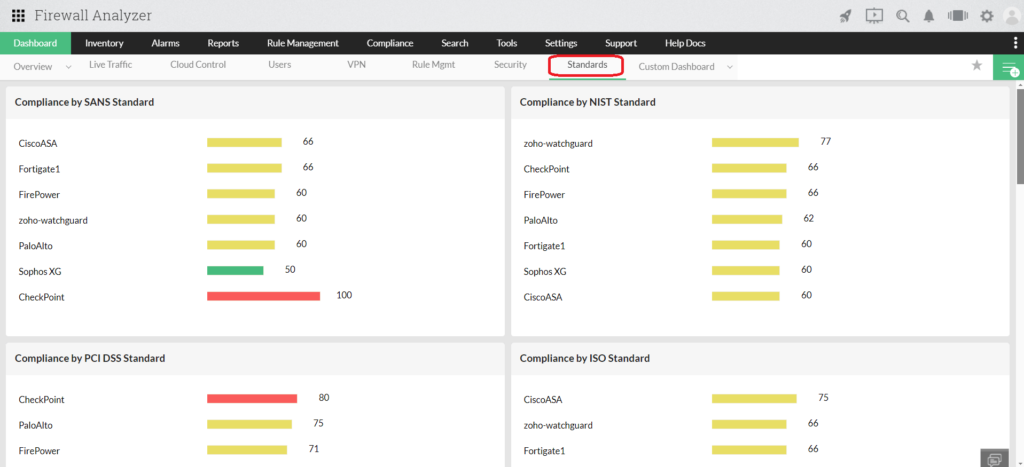
Key Features:
- Agent-less deployment for easy setup.
- Detailed security and traffic reports.
- Supports multiple firewall brands.
Pros:
- Affordable for small businesses.
- Easy to deploy without agents.
Cons:
- Limited focus on insider threats.
11. Exabeam Fusion
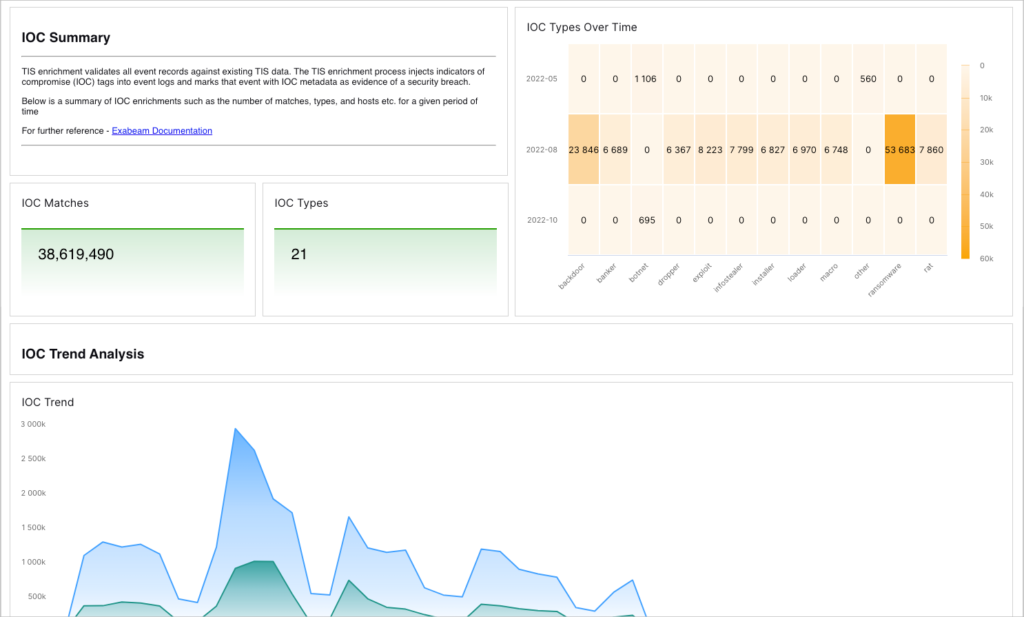
Key Features:
- AI-driven threat detection and response.
- GenAI-powered workflows for efficiency.
- Scalable log collection.
Pros:
- Comprehensive threat response.
- Strong AI analytics.
Cons:
- Complex setup for small teams.
12. Proofpoint Insider Threat Management
Overview: Renowned in compliance-heavy verticals, Proofpoint Insider Theft Management tool offers deep endpoint and user monitoring tied to data movement, exfiltration, and risky behaviors—across laptops, desktops, email, and cloud assets. It leverages contextual analytics, forensic evidence, and integration with SIEM/SOAR for rapid threat response.
Key Features:
- Activity timeline with user context.
- Automated content scanning and classification.
- Privacy controls with data masking.
Pros:
- Strong user behavior focus.
- Seamless integration with SIEM/SOAR.
Cons:
- Complex implementation for small teams
- High false positive rate.
Feature Comparison Table of Top Insider Threat Tools in 2025
|
Feature / Capability |
Kitecyber |
UpGuard |
Teramind |
Varonis |
MS Purview |
DTEX |
Everfox |
Syteca |
ManageEngine |
Exabeam |
Proofpoint |
| Insider Threat Prevention | Comprehensive★★★★★ • Agent-based behavioral analytics • Offline + encrypted-app monitoring | Poor ★★☆☆☆ • Third-party data sources only • Focuses on vendor risk, not users | Good ★★★★☆ • Strong keystroke & activity logging • High invasiveness impacts trust | Good ★★★★☆ • Privileged access & file behavior alerts • Limited on SaaS/endpoint coverage | Good ★★★★☆ • Policy-driven DLP rules • Limited insider behavioral analytics | Comprehensive ★★★★★ • Activity telemetry at scale • Lightweight endpoint collectors | Good ★★★★☆ • Network surveillance heritage • Limited endpoint analytics | Poor ★★☆☆☆ • Narrow scope • Few behavioral controls | Good ★★★★☆ • Logs + UEBA alerts • Requires heavy tuning | Good ★★★★☆ • UEBA for user/entity threats • Not real-time prevention | Good ★★★★☆ • Focused on email insider leaks • Gaps outside comms channels |
| Ransomware Prevention | Comprehensive★★★★★ • Disk-encryption hooks • C2/IP blocking & supply chain checks | Poor ★★☆☆☆ • No endpoint kill-chain coverage • Vendor risk only | Poor ★★☆☆☆ • Post-incident evidence, not prevention | Good ★★★★☆ • File share lockouts • Detects encryption attempts | Good ★★★★☆ • Built-in file sensitivity controls • Gaps on zero-day ransomware | Poor ★★☆☆☆ • Behavioral exfil detection, not ransomware kill chain | Good ★★★★☆ • Network anomaly detection • Limited endpoint lockdown | Poor ★★☆☆☆ • Not ransomware focused | Good ★★★★☆ • Some ransomware rules in DLP • Slow to detect | Poor ★★☆☆☆ • UEBA detection only, not blocking | Good ★★★★☆ • Email-borne ransomware defense • Lacks endpoint layer |
| False Positives | Low★★★★★ • Context-aware ML • Minimal tuning | Good ★★★★☆ • Simple scoring, but lacks depth | Poor ★★☆☆☆ • Overlogging + invasive alerts | Good ★★★★☆ • File sensitivity scoring • High tuning effort | Poor ★★☆☆☆ • Too many rule triggers • Heavy admin tuning needed | Good ★★★★☆ • Context-rich behavioral baseline • Still triggers anomalies | Good ★★★★☆ • Better tuned for gov nets • Less adaptable for SMBs | Poor ★★☆☆☆ • Basic keyword alerts • Lacks ML/AI | Good ★★★★☆ • Acceptable, but heavy SIEM tuning | Good ★★★★☆ • UEBA correlation helps • Still noisy in SMB scale | Poor ★★☆☆☆ • Email keyword-based • Many false positives |
| User Experience | Excellent★★★★★ • <2% CPU load • Transparent UI | Comprehensive ★★★★★ • Lightweight SaaS dashboard | Poor ★★☆☆☆ • Heavy surveillance feel • Privacy intrusive | Good ★★★★☆ • Background monitoring • IT-focused UI | Poor ★★☆☆☆ • Microsoft admin-heavy UX • Complex for end users | Comprehensive ★★★★★ • Endpoint invisible UX • Cloud dashboards | Good ★★★★☆ • Policy-heavy UX • Better for admins than users | Poor ★★☆☆☆ • Clunky interfaces • Limited automation | Good ★★★★☆ • Familiar IT UI • Can be cluttered | Poor ★★☆☆☆ • SIEM dashboards overwhelming | Good ★★★★☆ • User-focused email banners • Good awareness training |
| Deployment Model | Cloud-native, Gateway-less★★★★★ • Pure endpoint agent • No appliances | Good ★★★★☆ • Cloud-first, SaaS only | Good ★★★★☆ • Endpoint agent + SaaS | Good ★★★★☆ • On-prem + cloud mix • File servers centric | Poor ★★☆☆☆ • Hybrid only • Dependent on M365 stack | Comprehensive ★★★★★ • No agents, telemetry stream • SaaS-based | Poor ★★☆☆☆ • Legacy appliance DNA • Not modern endpoint-native | Poor ★★☆☆☆ • Appliance + services mix | Good ★★★★☆ • On-prem agent + cloud control | Poor ★★☆☆☆ • SIEM integration heavy infra | Good ★★★★☆ • SaaS/cloud native for comms |
| TCO (Total Cost of Ownership) | Low★★★★★ • No CAPEX • ~50% lower cost vs legacy | Good ★★★★☆ • Affordable SaaS subs | Poor ★★☆☆☆ • High admin overhead • Privacy backlash risks | Poor ★★☆☆☆ • Expensive per TB • Heavy infra costs | Poor ★★☆☆☆ • Licensing complexity • High OPEX for tuning | Good ★★★★☆ • Reasonable SaaS pricing • Lower infra costs | Poor ★★☆☆☆ • Expensive gov-grade tools • Niche use cases | Good ★★★★☆ • Regionally priced • Smaller scope | Good ★★★★☆ • Affordable SMB pricing • Some admin overhead | Poor ★★☆☆☆ • SIEM + UEBA = high TCO | Good ★★★★☆ • Predictable SaaS cost • Limited to email/security |
How to Choose the Best Insider Threat Solution For SMBs/Small Enterprises:
- Prioritize ease of use and rapid deployment: Kitecyber, Ekran, Netwrix offer simple onboarding with strong out-of-the-box protection.
- Look for unified solutions: Consolidate DLP, compliance, and user activity monitoring to reduce tool sprawl and costs.
- Check compliance coverage: SOC2, GDPR, PCI, HIPAA, etc.
- Consider budget flexibility: Modular subscription plans allow you to expand as you grow (Kitecyber, Ekran are leaders here).
For Large Enterprises/Regulated Firms:
- Behavioral analytics & UEBA are critical: Solutions like Kitecyber, Proofpoint, Exabeam, DTEX, Gurucul deliver robust context, rich forensics, and scale.
- Automated response and workflow: Look for integrations with SOAR and existing SIEM.
- Match your remote/hybrid architecture: Ensure coverage across cloud, SaaS, on-prem, and BYOD. Kitecyber excels in this.
- Vendor support & roadmap: Proven cases and strong roadmap investment are must-haves (Kitecyber/Proofpoint/Exabeam routinely score best in G2 support surveys).
Conclusion
Insider threats are a growing concern, but the right insider threat software product can protect your small business. Kitecyber leads as the #1 choice, offering AI-driven detection, user-friendly design, and compliance support tailored for SMBs. Don’t let a breach derail your business, act now to secure your data.
Try Kitecyber’s Insider Threat Software’s free trial and safeguard your business from insider threats today!