Table Of Content
Table Of Content
Replace McAfee DLP with These Alternatives for Windows, Mac, & Linux (2025)
-
September 9, 2025
-
Remote work has made every device a potential data breach. As employees access sensitive information from homes, cafés, or airports, the risk of accidental or malicious data exposure has never been higher. Trellix, formerly known as McAfee’s DLP agent, has done a better job in protecting customers’ sensitive data for years. But let’s be honest: the agent itself is heavy on endpoints, slow on Mac and Linux updates, and a nightmare to configure. If you’re managing a hybrid fleet or remote-first team, that’s not good enough.
So, what’s better in 2025?
We did our research and dug deep into the top-rated McAfee DLP alternatives & replacements that support Windows, macOS, and Linux equally well. The result? A long list of alternatives that do a better job at protecting your sensitive business data than McAfee.
Let’s explore the top 10 alternatives to McAfee (Now Trellix) DLP from the list!
Why Switch from McAfee DLP?
While Trellix (McAfee DLP) is recognized for its robust data protection capabilities, it isn’t without its challenges. Its agent can noticeably slow down endpoints, which is a significant drawback for organizations prioritizing system performance.
Managing policies sometimes feels like solving a puzzle, adding unnecessary complexity for security teams. Support for macOS and Linux often lags behind that for Windows, which can be problematic in diverse IT environments. These pain points are especially impactful as businesses strive to secure a mix of devices across platforms.
Many organizations are therefore drawn to McAfee DLP alternatives that address these shortcomings. Modern competitors offer lighter endpoint agents, faster updates across all major operating systems, and more intuitive interfaces designed for business needs. These alternatives don’t just promise robust protection, they help minimize management headaches, making them suitable for both small businesses and large enterprises aiming to protect sensitive data more efficiently.
Common Reasons for Seeking McAfee DLP Alternatives
- McAfee DLP's agent can consume significant CPU and RAM, slowing down endpoints.
- Policy management is often complex and difficult to navigate.
- Support for macOS and Linux regularly trails behind Windows capabilities.
- Deployment and configuration processes can be complicated.
- The user interface may feel cluttered and unintuitive.
- Limited or outdated features compared to leading alternatives (e.g., data classification, reporting).
- Bugs and stability issues, especially during updates or large-scale deployments.
- Customer support may be slow or less effective.
- Compatibility issues with newer browsers and operating systems.
- Alternative vendors offer enhanced compliance options, better cost efficiency, and easier integrations with modern IT stacks.
A Closer Look: Common Reasons People Seek McAfee DLP Alternatives
|
Reason |
Description |
|
High Resource Usage |
McAfee DLP agent can slow down endpoints by consuming significant CPU and RAM. |
|
Complex Policy Management |
Policy management is often complex and feels like solving a puzzle, increasing admin effort. |
|
Poor macOS/Linux Support |
Support for macOS and Linux regularly lags behind that for Windows, impacting diverse IT. |
|
Complicated Deployment & Configuration |
Deployment and setup processes can be difficult and time-consuming. |
|
Cluttered User Interface |
The UI can be unintuitive and overwhelming for users. |
|
Limited/Outdated Features |
Lacks advanced features present in newer alternatives (e.g., data classification, reporting). |
|
Bugs and Stability Issues |
Users face frequent bugs and stability challenges, especially during updates or scaling. |
|
Slow or Ineffective Customer Support |
Technical support may be slow to respond or less helpful than competitors. |
|
Compatibility Issues |
Not fully compatible with newer browsers or operating systems. |
|
Compliance, Cost, and Integration Limitations |
Other vendors may offer better compliance tools, cost savings, and easier integrations. |
|
Heavy Agent |
McAfee’s agent is heavier compared to the lighter alternatives available. |
|
Slower Cross-Platform Updates |
Updates and improvements for non-Windows platforms are slower. |
Top 7 Paid and Free Alternatives to McAfee DLP
1. Kitecyber Data Shield
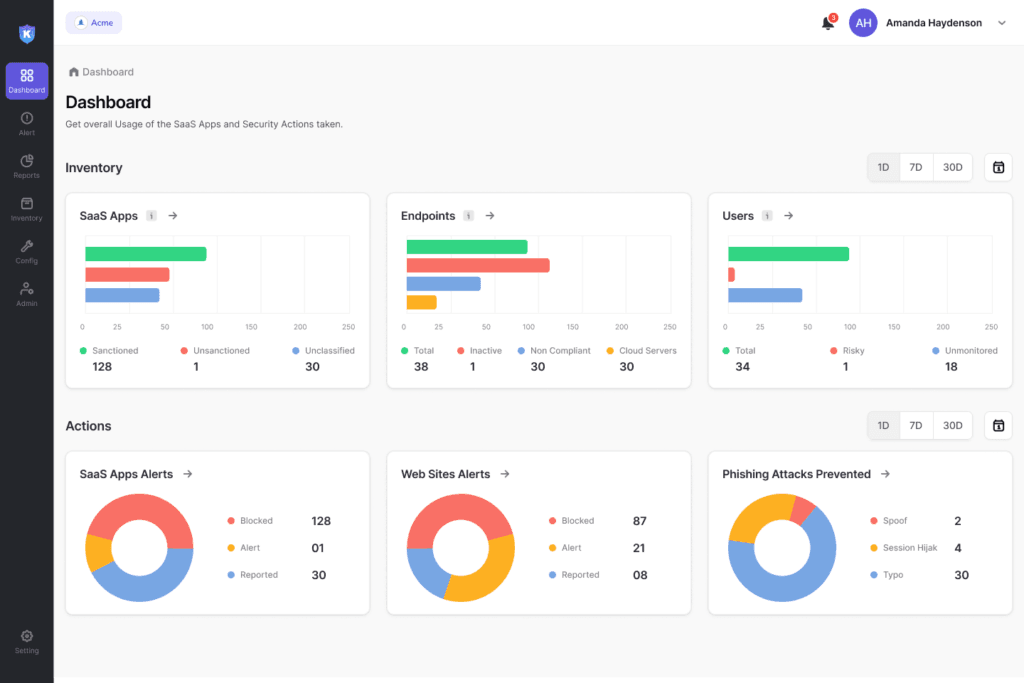
Kitecyber Data Shield simplifies data protection by letting you deploy one lightweight agent across Windows, Mac, and Linux devices to secure sensitive data both in motion, through email, SaaS apps, web, Airplay, and USB, and at rest on endpoints. It supports Mobile Device Management (MDM) for streamlined device oversight. For IT and security admins, a cloud-based SaaS console provides a single dashboard to control and visualize all activity. The AI-driven system automatically discovers and classifies over 80 data types, applies zero-touch encryption, and tracks data lineage, all within the same intuitive interface. With a per-user, per-module, per-month licensing model, costs stay predictable without hidden fees, and bundled pricing with other Kitecyber modules can save you up to 60% compared to competitors, making it a cost-effective, comprehensive DLP alternative to McAfee (Trellix).
- Endpoint-first inspection for encrypted traffic and offline use.
- Instant device lock, wipe, or kill switch on policy breach.
- Built-in zero-trust VPN and secure web gateway.
- Compliance mappings for SOC 2, HIPAA, GDPR.
- Sensitive data discovery & classification
- Sensitive data activity tracking
- Protect USB, Network drives, cloud storage & local file sharing
- Real time upload/download monitoring
- Real time copy/paste reporting and alerts
- Gen AI risk controls & End-to-End encryption
- Data visibility into certificate pinned apps
- Behavioral analytics: AI-driven anomaly detection
- Offline security: Continuous monitoring without connectivity
- Malicious insider detection: Advanced pattern recognition
- Zero-trust architecture: Continuous verification
Kitecyber Data Shield vs (Trellix) McAfee DLP: Why Customers Choose Kitecyber?
- Sensitive Data Detection & Classification: Automated detection and classification of PII, PHI, and regulated data.
- Email & Web Content Filtering: Monitors and controls sensitive data transfers via email, web, and supported cloud applications.
- User/Device Monitoring & Compliance: Real-time alerts and audit logs for all policy events, easy productivity filtering, and strong compliance reporting (GDPR, SOC2, HIPAA, PCI DSS, etc.).
- Offline Enforcement: Policies are enforced on endpoints even when devices are offline or remote.
- Unified Platform: Provides device compliance, secure access, and DLP in one intuitive interface that supports remote/hybrid workforces.
"Kitecyber has been amazing for our SMB customers, who can now enjoy enterprise grade security with a simple and cost effective solution."
"Instead of dealing with multiple complex solutions, with Kitecyber they can get advanced security with ease using a single copilot”

2. Symantec Data Loss Prevention (Broadcom)
- Indexed Document Matching (IDM) and EDM fingerprinting.
- Inline network prevention for email/web ICAP.
- Real-time policy alerts with detailed incident logs.
3. Forcepoint Data Loss Prevention
Forcepoint DLP is a mature, unified platform protecting data in motion, at rest, and in use across cloud applications, email, web, endpoint devices, and networks, managed via a single policy engine. It includes a vast library of compliance templates (covering GDPR, HIPAA, PCI‑DSS, and more) and 1,700+ classifiers for structured and unstructured content detection, The solution embeds risk-adaptive protection powered by user behavior analytics, dynamically updating enforcement based on real-time user risk scores
- Risk-Adaptive Protection adjusts controls based on user risk.
- 1,700+ global compliance templates.
- Drip-DLP detection for slow data leaks.
4. Fortra Digital Guardian
Digital Guardian is another alternative to McAfee DLP, which supports Windows, macOS, Linux, and VDI with kernel-level control and 400+ reports. It’s priced at $21.30/user/year for endpoint DLP. G2 users rate it 4.2 stars, appreciating its forensics but noting a steeper learning curve.
- Kernel-level drivers for precise process control.
- Managed service option for smaller teams.
- Exact Data Match with behavioral analytics.
5. Safetica DLP
- Smart classification with dynamic policy actions.
- Endpoint and Microsoft 365 cloud protection.
- Shadow copy for incident evidence and SIEM integration.
6. Netwrix Endpoint Protector
Known for granular device control and offline enforcement, Netwrix Endpoint Protector DLP supports all major OSes. It’s priced at approximately $22.80/user/year. G2 users rate it 4.5 stars for its USB encryption and zero-day support.
- Content-aware and context scanning on-device.
- Enforced USB encryption with AES-256.
- Central cloud or on-prem console.
7. Microsoft Purview Data Loss Prevention
- Unified classifier and label engine with AIP.
- Endpoint DLP for Windows/Mac with USB blocking.
- Single compliance portal with Defender/Sentinel alerts.
8. Trend Micro Integrated DLP
- Real-time pattern matching across channels.
- Appliance-mode Network Monitor for fast deployment.
- Tight Active Directory sync.
9. Teramind DLP
- Behavioral rules trigger auto-block or lockout.
- Insider-risk heatmaps with AI anomaly detection.
- Forensic video logs for HR/legal cases.
10. Acronis Cyber Protect (with DLP)
- Continuous data protection with immutable backups.
- USB and clipboard control with content rules.
- Single console for patching, EDR, and DLP.
Feature-by-Feature Comparison of McAfee DLP Alternatives
|
Feature/Capability |
Kitecyber |
Symantec |
Forcepoint |
Digital Guardian |
Safetica |
Netwrix EP |
MS Purview |
Trend Micro |
Teramind |
Acronis |
|
G2 Ease of Use* |
8.7 / 10 |
8.6 / 10 |
8.6 / 10 |
7.4 / 10 |
8.9 / 10 |
9.1 / 10 |
8.8 / 10 |
8.0 / 10 |
9.0 / 10 |
9.0 / 10 |
|
Insider Threats |
Comprehensive ★★★★★ - Agent-based behavioral analytics - Encrypted-app & offline monitoring - Password protected file tracking |
Good ★★★★☆ - Monitors risky user behavior via UEBA - Assigns risk scores - Focus on insider threat detection |
Good ★★★★☆ - Risk-adaptive protection based on user context - Behavioral analytics - 150+ behavior indicators |
Good ★★★★☆ - Zero-trust approach with user behavior analytics - Advanced tracking for data leaks - Granular data movement control |
Good ★★★★☆ - Proactive user behavior monitoring - Context analysis - Regulates data access |
Good ★★★★☆ - Real-time anomaly & insider-risk scoring - Offline device support - Automated containment |
Good ★★★★☆ - Monitors data for unintentional sharing - User behavior analytics - Activity tracking |
Good ★★★★☆ - Integrated monitoring across channels - User behavior focus - Compliance templates |
Comprehensive ★★★★★ - Advanced UEBA and behavioral analytics - Real-time risk identification - Employee monitoring integration |
Limited ★★★☆☆ - General threat detection - Limited specific insider focus - Data access monitoring |
|
Ransomware Protection |
Comprehensive ★★★★★ - C2/IP blocking & supply-chain API monitoring - Managed disk-encryption hooks - Mitigates ~80% ransomware techniques for MiTRE style tests |
Good ★★★★☆ - Sandbox detonation for threats - Threat intelligence integration - Multi-layer protection |
Good ★★★★☆ - IPS & anti-evasion sandboxing - Remote browser isolation - Ransomware-specific defenses |
Good ★★★★☆ - Advanced threat protection - Automated blocking and encryption - Ransomware mitigation |
Limited ★★★☆☆ - Basic threat scanning - No specific ransomware focus noted |
Good ★★★★☆ - Multi-layer endpoint quarantine - Server backup integration - Ransomware containment |
Limited ★★★☆☆ - Integrated with Microsoft security - Limited dedicated ransomware tools |
Good ★★★★☆ - Sandbox as a service - Ransomware detection in endpoints - Web gateway security |
Limited ★★★☆☆ - Behavioral rules for threats - No explicit ransomware protection |
Good ★★★★☆ - Protection from ransomware attacks - Immutable backups and recovery - Efficient threat blocking |
|
False Positive Rates |
Low ★★★★★ - AI-driven detection - Minimal tuning - Contextual awareness |
Medium ★★★☆☆ - May flag non-scope files - Requires some tuning - Signature-based issues |
High ★★☆☆☆ - Occasional false positives - Extensive policy refinement needed - Over-blocking issues |
Medium ★★★☆☆ - Heuristic detection - Moderate tuning required |
Medium ★★★☆☆ - Content inspection rules - Some tuning needed |
High ★★☆☆☆ - Frequent tuning for OCR/signature rules - Noise in encrypted content |
Medium ★★★☆☆ - Potential false positives with RegEx - Heuristic rules require refinement |
Medium ★★★☆☆ - Content-based detection - Moderate tuning |
Low ★★★★★ - Granular policy management to minimize - Advanced rules reduce errors |
Medium ★★★☆☆ - Behavioral detection - Some false alerts possible |
|
User Experience |
Excellent ★★★★★ - < 2 % CPU overhead - Zero network impact - Transparent UI |
Good ★★★★☆ - Complex UI and configuration - Resource-intensive - Good security education |
Poor ★★☆☆☆ - Complex interface for new users - CPU/memory spikes - Slow support |
Good ★★★★☆ - User-friendly but confusing UI - Difficult custom reports - Managed services reduce burden |
Good ★★★★☆ - Intuitive but poor initial setup - Unintuitive configuration - Support issues |
Good ★★★★☆ - Lightweight agent post-tuning - Initial console complexity - Minimal impact |
Good ★★★★☆ - User-friendly interface - Hectic navigation and setup - Memory-intensive |
Good ★★★★☆ - User-friendly centralized management - High resource use possible - Slow policy deployment |
Excellent ★★★★★ - User-friendly interface - Streamlined setup - Customizable alerts |
Good ★★★★☆ - User-friendly with real-time monitoring - Some complex interface reports - Slow customer service |
|
Deployment Model |
No appliances gateways ★★★★★ - Pure endpoint agent - Cloud-native management |
Hybrid ★★★☆☆ - On-premises core and cloud options - Multi-component setup - Supports VDI |
Appliance-based ★★☆☆☆ - Management server & gateways - Complex topology - Flexible network/endpoint/cloud |
Hybrid ★★★☆☆ - SaaS or managed service - Endpoint focus with cloud - Cross-platform support |
Hybrid ★★★☆☆ - Cloud-managed with on-prem options - Multi-OS support - No VDI |
Appliance-based ★★☆☆☆ - Central server setup - Hybrid options - Cross-platform |
Cloud-native ★★★★★ - Integrated with Microsoft 365 - Cloud deployment - No VDI support |
Hybrid ★★★☆☆ - Flexible on-prem/cloud - Endpoint and gateway integration |
Cloud or on-prem ★★★★☆ - Flexible deployment - Supports VDI - High-availability options |
Cloud-native ★★★★★ - Cloud-based with remote management - Supports VDI - Modular add-ons |
|
TCO (Total Cost) |
Low ★★★★★ - No CAPEX appliances - ~50% cost savings vs. legacy |
High ★☆☆☆☆ - $96/year per license - Professional services required - Volume discounts available |
High ★☆☆☆☆ - Contact for pricing - Costly customizations - 30-day free trial |
Medium ★★★☆☆ - Contact for pricing - Managed services optional |
Low ★★★★★ - $54/year per user basic - Annual billing - 30-day free trial |
Medium ★★★☆☆ - Contact for pricing - Typical $20k-$82k/year - Subscription-based |
Medium ★★★☆☆ - E3/E5 subscriptions - Request pricing - 90-day free trial |
Medium ★★★☆☆ - Costly licensing - Contact for details |
Medium ★★★☆☆ - $156/year per user basic - Custom enterprise - 7-day free trial |
Low ★★★★★ - $57/year per computer basic - Custom cloud - 30-day free trial & refund |
|
Endpoint DLP |
Comprehensive ★★★★★ - Win/Mac/Linux - Cloud-storage & USB DLP - Network-share control |
Comprehensive ★★★★★ - Win/Mac/Linux support - USB/Bluetooth control - AES-256 encryption |
Good ★★★★☆ - Windows & Mac - USB control - Kernel-driver scanning |
Comprehensive ★★★★★ - Broad coverage (Win/Mac/Linux) - Automated blocking/encryption - Endpoint focus |
Comprehensive ★★★★★ - Multi-OS endpoint protection - USB/file control - Content inspection |
Comprehensive ★★★★★ - Win/Mac - USB/Bluetooth control - Cross-platform DLP |
Good ★★★★☆ - Endpoint DLP integration - Win/Mac sensors - File control |
Good ★★★★☆ - Integrated endpoint encryption - Mobile security - USB control |
Comprehensive ★★★★★ - Endpoint monitoring - Sensitive data classification - Automated blocking |
Good ★★★★☆ - Endpoint protection - Supports 20+ platforms - Mobile device control |
|
Network DLP – SaaS & Cloud |
Comprehensive ★★★★★ - GenAI app monitoring - Real-time blocking in SaaS apps - Native API integrations |
Comprehensive ★★★★★ - Cloud Prevent and Network Monitor - SSL/TLS decryption - API connectors |
Comprehensive ★★★★★ - SSL/TLS decryption - Email & web gateways - Cloud-native SASE |
Comprehensive ★★★★★ - Cloud DLP solutions - Network traffic monitoring - API integrations |
Good ★★★★☆ - Network traffic control - SaaS app monitoring - Cloud connectors |
Limited ★★☆☆☆ - Basic cloud connectors - Content-aware protection - Limited SaaS focus |
Comprehensive ★★★★★ - API connectors (O365, etc.) - Cloud app monitoring - Integrated with Azure |
Comprehensive ★★★★★ - Cloud storage access control - Network gateways - SaaS protection |
Good ★★★★☆ - Cloud-based DLP - SaaS integration - Network monitoring |
Comprehensive ★★★★★ - Cloud DLP with AWS/Microsoft 365 - SaaS protection - Immutable storage |
|
Data Lineage & Discovery |
Comprehensive ★★★★★ - Cross-platform audit trails - AI classification - Real-time alerts |
Comprehensive ★★★★★ - Data Insight for discovery - Lifecycle view - Metadata labeling |
Comprehensive ★★★★★ - Lifecycle view - DSPM integration - Continuous monitoring |
Comprehensive ★★★★★ - End-to-end data tracking - Automated classification - Continuous discovery |
Comprehensive ★★★★★ - Data-at-rest discovery - Content-aware classification - Audit logs |
Limited ★★☆☆☆ - File-transfer logs - eDiscovery scans - Basic tracking |
Comprehensive ★★★★★ - Sensitive information types - End-to-end tracking - Metadata integration |
Good ★★★★☆ - Data classification - Discovery across channels - Reporting features |
Comprehensive ★★★★★ - Sensitive data classification - Detailed reporting - Data handling insights |
Good ★★★★☆ - Data discovery in backups - Classification tools - Audit trails |
|
Location-Aware Security |
Comprehensive ★★★★★ - Geofencing policies to restrict access by region - Dynamic peripheral control (e.g., camera disable) when on-premises |
Poor ★★☆☆☆ - Limited endpoint peripheral enforcement - No native geolocation |
Poor ★★☆☆☆ - Device control limited to storage - No camera disable or geolocation |
Poor ★★☆☆☆ - Minimal location enforcement - Device control for peripherals |
Good ★★★★☆ - Device control rules to block peripherals - Including camera blocking - No geolocation triggers |
Good ★★★★☆ - Device control for peripherals - Block camera when plugged in - No geolocation |
Poor ★★☆☆☆ - Cloud focus with minimal endpoint location control - No geofencing |
Limited ★★★☆☆ - Basic device control - No specific location-aware features |
Limited ★★★☆☆ - No explicit location enforcement - Peripheral control possible |
Limited ★★★☆☆ - Device control add-ons - No geofencing mentioned |
Replace Trellix (Formerly McAfee DLP) with Kitecyber Data Shield
Switching from McAfee DLP in 2025 doesn’t mean sacrificing security. Kitecyber Data Shield leads with its lightweight, unified approach, but each alternative brings unique strengths. Evaluate your compliance needs, budget, and OS environment to pick the best fit. Most vendors offer free trials, so you can test before committing. Start with Kitecyber for its top G2 rating and cross-platform prowess, and explore others based on your specific requirements.