Table Of Content
Top 10 Innovative Zero Trust Vendors & Solutions in 2025
-
July 24, 2025
-
Despite multiple vendors claiming to move toward Zero Trust Security, only 1% truly meet the definition of true zero trust. You’re likely grappling with a question that keeps security leaders awake at night: which vendor can deliver on the promise of “never trust, always verify” without breaking your infrastructure or budget? The answer lies in understanding the no-nonsense definition of Zero Trust, not just textbook jargon.
This guide from Kitecyber explains Zero Trust and highlights 10 top vendors reshaping cybersecurity in 2025. Let’s dive in.
What is the “No-Bullshit” Definition of Zero-Trust Principle?
Every request to your network or data, whether on-premises or in the cloud, needs verification and continuous validation. Zero Trust flips traditional security. It assumes nothing inside your network is safe. Threats can come from outside (like supply-chain partners) or inside (like employees). Nothing gets a free pass, be it your user, device, internet, app, or partners.
Access comes only after passing rigorous checks. This stops attackers from moving freely if they breach your system. It’s verify first, trust later, every time.
True Zero Trust isn’t about endpoints trusting a central provider. It’s about your assets judging trust based on the origin of client traffic. That’s why only 1% of companies fully nail Zero Trust.
Common Challenges Companies Face with Zero Trust
- Flawed architecture: Small design errors can tank the model.
- No single solution: Zero Trust isn’t a plug-and-play product. Your team must design and build it.
- Legacy systems: Older tools often don’t support modern Zero Trust needs.
- Ongoing effort: It’s not a one-time setup. You need updates, testing, and audits.
What You Should Ask When Evaluating Zero Trust Vendors
1. Are You NIST SP 800-207 Compliant?
- Interoperability across platforms
- No vendor lock-in
- A flexible framework
2. How Do You Protect Against Credential Threats?
- How do you secure human credentials (e.g., MFA, behavioral analytics)?
- What protects non-human credentials like APIs or service accounts?
- How do you stop identity store attacks (e.g., LDAP, Active Directory)?
3. Can You Integrate With Our Existing Infrastructure?
- Integration with GRC tools or IAM tools
- Support for Secure Web Gateways and email security
- Fit with legacy and hybrid environments
4. How Does Your Solution Impact User Experience?
- What’s the learning curve for admins and users?
- Will it disrupt productivity or require heavy retraining?
- Is the interface intuitive and customizable?
5. What’s Your Deployment Timeline and Phased Rollout Strategy?
- How long does implementation take? (Expect 6–8 weeks for assessment)
- What are the phases: kickoff, discovery, evaluation, roadmap?
- Can you support incremental rollout by use case?
6. How Do You Measure Success and Maturity?
- How do you assess our Zero Trust maturity?
- What KPIs track improvements?
- Can you prioritize high-impact use cases?
7. Do You Support a Long-Term Zero Trust Strategy?
- How do you support readiness and change management?
- What training or professional services do you offer?
- How do you ensure ROI as threats evolve?
10 Top Zero Trust Security Vendors, Providers, & Companies
1. Kitecyber - The Hyperconverged Zero Trust Vendor
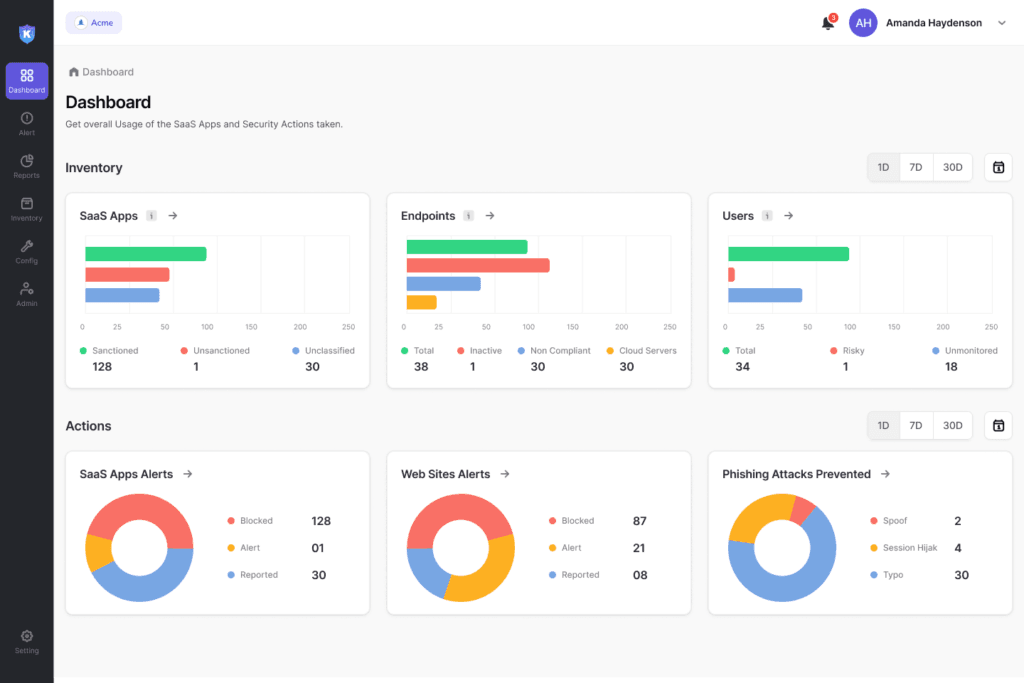
Kitecyber delivers a hyperconverged Security Service Edge (SSE) solution, combining device security, next-gen secure web gateway, data protection, and Zero Trust Network Access (ZTNA) into one lightweight endpoint agent. It tackles visibility gaps in SaaS apps, user activity, and data movement that traditional in-network SASE solutions miss.
How Kitecyber Implements Zero Trust for Modern Organizations
At Kitecyber, Zero Trust is more than a concept: it’s a security model built on the principle that no user (whether contractor, insider or 3rd party person), device, network, or application is ever inherently trusted, whether they are inside or outside your organization’s perimeter. Every access request to an organization’s assets must be verified, identities and devices must be authenticated, and security posture must be continuously monitored. Kitecyber authenticates identities with the help of integration with top IAM providers. This approach significantly reduces the potential impact of a breach and offers strong protection against sophisticated threats.
Endpoints such as laptops, desktops, and mobile devices are prime targets for attackers and often the starting point of data breaches. Unlike traditional security models that focus on defending the network perimeter, Zero Trust shifts the focus to the endpoint itself. This is especially critical in today’s world of remote work, cloud-first operations, and BYOD environments, where devices are constantly connecting from outside the corporate network.
Kitecyber’s Device Trust Engine directly implements Zero Trust at the endpoint, enabling device identification, continuous security posture validation, and policy enforcement before any resource access is granted. A device must meet stringent security requirements: if it doesn’t, access is automatically denied, even with correct user credentials.
Unlike legacy SWG solutions that route web traffic through distant data centers (creating bottlenecks and latency), Kitecyber moves the gateway onto each endpoint:
- Provides URL Filtering, SSL Inspection, and SaaS/ Gen AI App Controls directly on user devices.
- AI-driven controls deliver instant protection, regardless of user location ("Fly Direct").
- Eliminates hairpinning, improving user experience and closing off attack vectors created by central proxies.
- Protects data both at rest and in motion, directly from users’ devices.
- Utilizes User Behavior Analytics (UBA) to monitor data flows, exposures, and abnormal movement, giving you granular visibility into risk.
- Stops sensitive data leakage at the source rather than relying solely on perimeter-based controls.
Kitecyber’s Infra Shield is a ZTNA vendor which replaces legacy VPNs, which are increasingly vulnerable with a passwordless security framework:
- Enforces device-based trust to ensure only secured endpoints can access cloud/private resources.
- Supports both self-hosted and SaaS models for maximum flexibility.
- Applies Zero Touch Provisioning for rapid integration and deployment.
- Private IP enforcement prevents exposure of cloud infrastructure to the public internet, greatly reducing attack surfaces.
All three Kitecyber solutions are built on Zero Trust principles and enhanced with advanced, AI-powered phishing protection and real-time, continuous monitoring. This combination enables organizations to prevent lateral threats while maintaining a robust Zero Trust architecture.
- No assumed trust: Identity, device, and app posture are continuously verified—everywhere your users work.
- Blast radius reduction: Compromised credentials or endpoints cannot laterally move through networks or cloud deployments.
- Unified, simplified security: SWG, DLP, and ZTNA all work together at the endpoint, streamlining security operations and removing dependency on slow, complex, multi-vendor stacks.
- Cloud-native and scalable: Flexible enough for single-cloud or multi-cloud architectures, ensuring consistent Zero Trust enforcement across any environment.
- VPN risk eliminated: Removes the need for risky VPNs and traditional network perimeters.
2. Palo Alto Networks - The Enterprise Zero Trust Pioneer
Microsegmentation is a core tenet, instituting granular security controls and compartmentalizing resources to disrupt lateral movement if an attacker gains access. Policy enforcement is applied uniformly through centralized platforms, such as Next-Gen Firewalls (NGFWs), Prisma Cloud, Prisma Access (for SASE and ZTNA), and Cortex XDR for endpoints. Automated threat intelligence and adaptive policy updates ensure rapid identification and mitigation of new threats. This progressive model provides strong, dynamic security that protects applications, users, and data in hybrid, multi-cloud, and remote work environments, dismantling legacy perimeter barriers and complex tool sprawl
- Identity, device, workload validation at every access point.
- Zero Trust segmentation and microsegmentation, stopping lateral movement.
- Unified policy and analytics across network, endpoint, and cloud.
- Integration of AI-driven threat intelligence for real-time protection.
3. Netskope One - Cloud-Native Zero Trust
Netskope One uses a cloud-native Security Service Edge (SSE) platform that implements zero trust at every access point. Its Zero Trust Engine dynamically assesses each transaction using continuous inputs from AI and machine learning, analyzing variables such as app instance, user action, device posture, and behavior. All traffic, including web, cloud, and private app, undergoes granular policy evaluation and real-time security inspections, powered by a single-pass architecture that prevents latency or bottlenecks. Least privilege access is enforced by granting users and devices only the minimum rights necessary, reducing risk across cloud, SaaS, and web resources. Continuous visibility and inline DLP, paired with AI-driven threat analytics, enable organizations to respond quickly to evolving threats. The solution unifies ZTNA, SWG, and CASB, creating a consistent zero trust fabric that protects users and data wherever they operate, and integrates easily with hybrid network setups
- Granular policy enforcement for cloud apps
- Real-time data loss prevention (DLP)
- AI-driven threat intelligence
- Seamless integration with hybrid environments
4. JumpCloud - Identity-Centric Zero Trust
JumpCloud is one of the best zero trust solutions, which employs Zero Trust by rigorously verifying both users and their devices at every access attempt. It maintains a unified cloud directory that orchestrates identity management, single sign-on (SSO), and multi-factor authentication (MFA) across all endpoints, apps, and networks. Conditional access policies enforce dynamic and context-based security, such as location and device health, ensuring only compliant and authorized entities gain entry. Device posture management and automated policy enforcement run continuously, not just at login, to safeguard endpoints even as they move between locations. JumpCloud’s approach allows organizations to consolidate identity and device security in one platform, empowering secure access for hybrid and remote workforces while reducing the risk posed by siloed IAM tools and unmanaged devices.
- Cross-platform device management
- SSO and MFA for secure access
- Conditional access policies
- Support for hybrid and remote workforces
5. Twingate - Modern VPN Alternative
Twingate replaces legacy VPNs by decoupling secure network access from the underlying infrastructure and applying Zero Trust principles to every user, device, and resource. Each access request is evaluated in real time for identity and device trustworthiness, with strict least-privilege policies enforced at the resource level. The software-defined perimeter keeps protected resources invisible from the public internet and blocks direct inbound access, significantly reducing the network attack surface. Twingate clients implement security controls at the network edge and route traffic over encrypted tunnels to authorized connectors, drastically minimizing the potential for lateral movement or privilege escalation. Integration with existing identity providers and device inventory allows organizations to automate provisioning, monitoring, and rapid response, all while simplifying setup and management in both on-premises and cloud environments.
- Split tunneling for faster performance
- Device posture checks
- Granular access controls
- Easy deployment with minimal infrastructure changes
6. Check Point - Comprehensive Zero Trust
- Advanced threat prevention with AI
- ZTNA for private and SaaS apps
- Unified security management
- Scalable for large enterprises
7. SentinelOne - Endpoint-Driven Zero Trust
- AI-powered endpoint protection
- Dynamic access controls
- Behavioral analytics for threat detection
- Integration with SIEM/SOAR
8. Cisco Zero Trust - Network-Centric Security
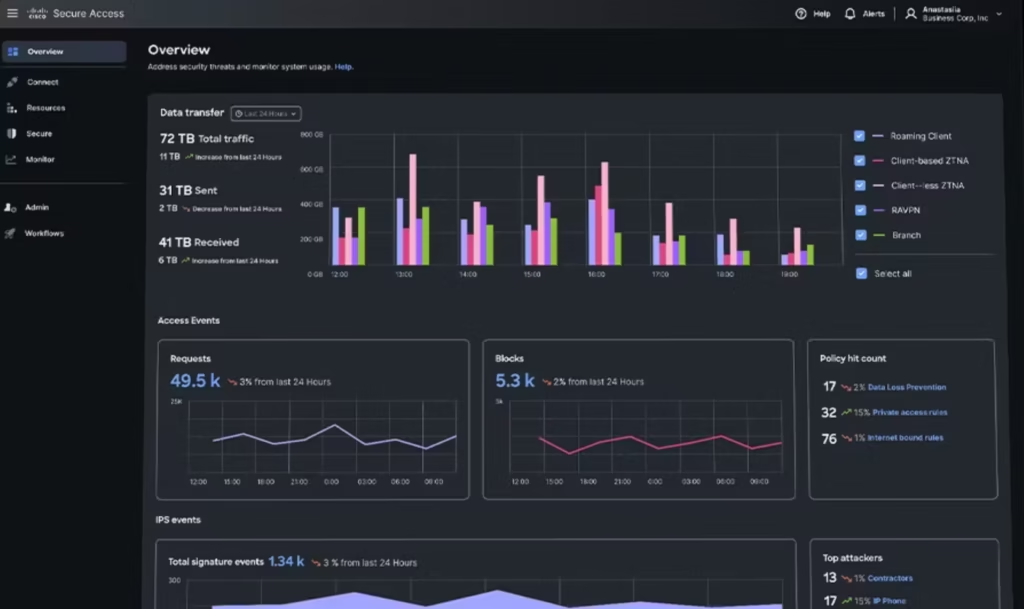
Zero Trust Solution Overview: Cisco Secure Access combines ZTNA, Duo for MFA, and SecureX for threat response, ensuring comprehensive security.
- Duo MFA with device health checks
- SecureX for unified threat response
- Network segmentation
- Cloud and on-premises support
9. Symantec Zero Trust - Enterprise-Grade Protection
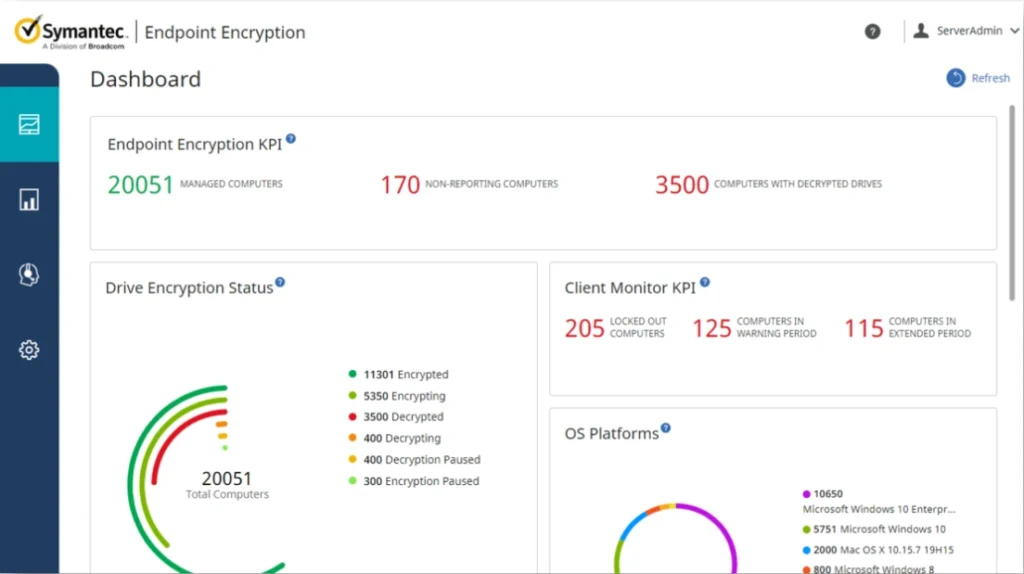
- Advanced DLP for data protection
- ZTNA for secure app access
- Endpoint security with AI analytics
- Centralized policy management
10. Zscaler - Cloud-First Zero Trust
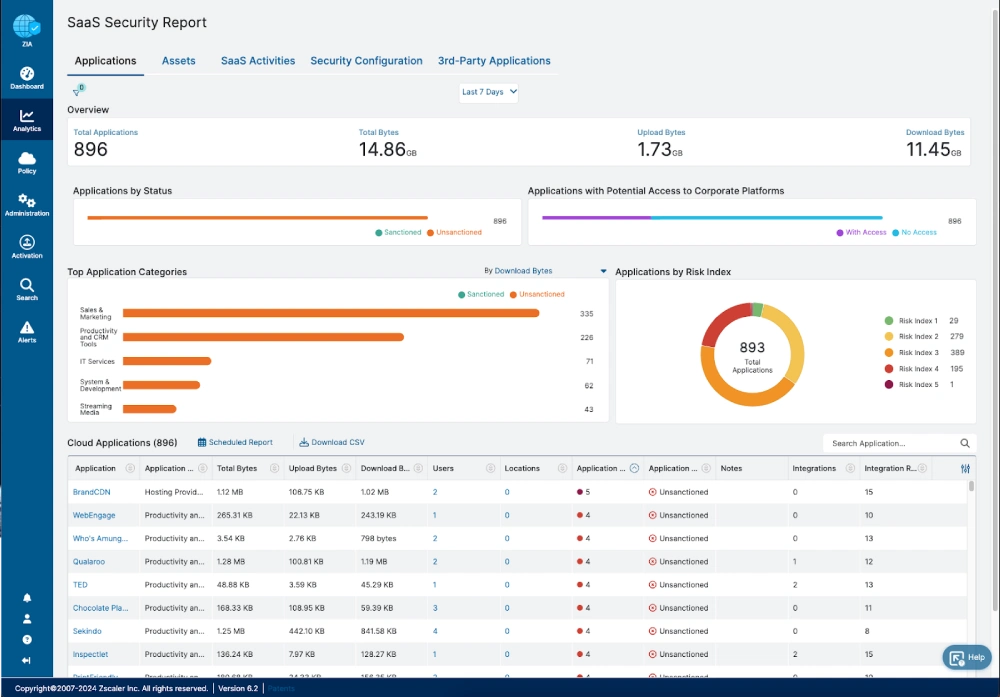
Zscaler’s Zero Trust Exchange operates as a globally distributed, cloud-native platform built on the principle of “never trust, always verify.” It brokers every user-to-app and device-to-app connection through policy-driven segmentation and dynamic context checks, without ever placing users on the network itself. By terminating and inspecting all connections before they reach apps, Zscaler eliminates lateral movement, reduces the internet attack surface, and enforces granular controls for data security and threat prevention, even in encrypted traffic. Automation via AI/ML and unified policy management simplifies zero trust operations at scale, supporting tens of thousands of users and cloud workloads with streamlined management and superior user experiences, removing the need for legacy VPNs, firewalls, and complex architectures.
- Cloud-native ZTNA and SWG
- Real-time threat prevention
- Granular user and app policies
- Scalable for global workforces
Conclusion
Implementing Zero Trust is no easy-deal. Flawed designs, legacy systems, and constant maintenance can trip you up. But the rewards like lower security risks & better data movement visibility are worth it. The Zero Trust vendors mentioned in this blog, from Kitecyber’s hyperconverged SSE to Zscaler’s cloud-first platform, offer solutions to truly implement Zero Trust.
When choosing a Zero Trust Security vendor, ask tough questions. Are they NIST SP 800-207 compliant? Can they secure credentials and integrate with your systems? Do they prioritize user experience? The right security partner makes adoption smoother and more effective.
The zero trust market is exploding: from $36.5 billion in 2024 to $78.7 billion by 2029, per MarketsandMarkets. Your next step? Evaluate these vendors. Dig into their solutions. Start small, test, and scale. Your organization’s security depends on it. In a world where trust is a liability, Zero Trust is your strength.

Ajay Gulati
Ajay Gulati is a passionate entrepreneur focused on bringing innovative products to market that solve real-world problems with high impact. He is highly skilled in building and leading effective software development teams, driving success through strong leadership and technical expertise. With deep knowledge across multiple domains, including virtualization, networking, storage, cloud environments, and on-premises systems, he excels in product development and troubleshooting. His experience spans global development environments, working across multiple geographies. As the co-founder of Kitecyber, he is dedicated to advancing AI-driven security solutions.